A recent investigation into misconfigured Apache Airflow instances has uncovered critical vulnerabilities exposing login credentials, API keys, and cloud service access tokens to potential attackers.
These workflow platform misconfigurations—primarily caused by insecure coding practices and outdated deployments—have compromised data security across industries such as finance, healthcare, and e-commerce, with credentials for AWS, Slack, PayPal, and internal databases left unprotected.

Architecture and Vulnerabilities in Apache Airflow
Apache Airflow, the open-source workflow management system with 22.8K GitHub stars, uses Python-based Directed Acyclic Graphs (DAGs) to orchestrate tasks across distributed systems, as per a report by Intezer.
Its flexibility in integrating with external services via Variables (key-value stores for credentials) and Connections (encrypted authentication parameters) becomes a liability when misconfigured. Researchers identified four primary vectors for credential leakage:
- Hardcoded Secrets in DAG Scripts
Inline credentials embedded directly in task code remain prevalent. For example, a PostgreSQL password exposed in a production DAG:
postgres_conn = PostgresHook(
postgres_conn_id='prod_db',
host='db.example.com',
password='s3cr3tP@ssw0rd' # Hardcoded credentials
)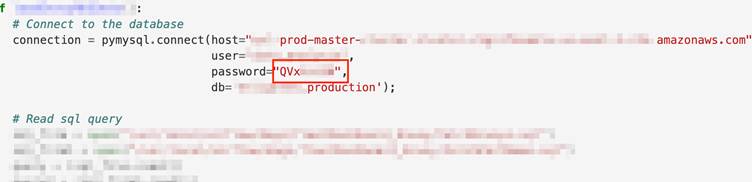
This anti-pattern bypasses Airflow’s secure Connections framework, leaving credentials visible in version control and UI audits.
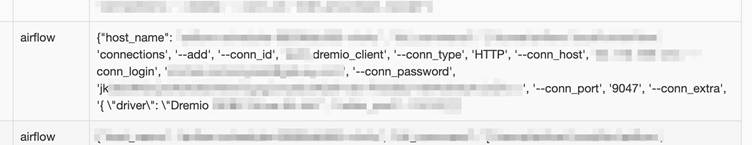
- Unencrypted Variables and Connection Metadata
While Airflow’s Fernet encryption can secure Variables, misconfigurations often leave them decrypted. A Slack webhook token stored in plaintext:
slack_token = Variable.get("alert_webhook") # Returns 'xoxb-1234-abcd' unencryptedSimilarly, AWS keys placed in the Extra field of Connections—meant for non-secret metadata—bypass Fernet protection.
- Legacy Logging Vulnerabilities (CVE-2020-17511)
Versions prior to 1.10.13 log credentials in clear text when using CLI tools. Attackers exploiting this could harvest passwords from task logs:
INFO – Executing: airflow users create -u admin -p insecure_password123
- Exposed Configuration Files
Misguided airflow.cfg settings like expose_config = True publicly reveal Fernet keys and database URIs. One instance exposed a decryption key critical for variable security:
fernet_key = qWISL8cA12345EXAMPLE_KEYAttack Surface and Observed Payloads
Threat actors exploiting these flaws gain access to:
- Cloud Infrastructure: AWS IAM keys linked to production environments
- Internal Systems: Database credentials for MySQL, Snowflake, and Hadoop clusters
- Collaboration Tools: Slack tokens enabling social engineering campaigns
- Payment Processors: PayPal API keys for transaction manipulation
Researchers highlighted cases where exposed Docker image names (e.g., internal-registry.example/biometric_processing:v2.1) could facilitate supply chain attacks by substituting malicious containers.
Unsecured Airflow instances violate GDPR and CCPA regulations through unintended data leakage, risking fines up to 4% of global revenue.
The Colonial Pipeline breach precedent demonstrates how credential leaks enable ransomware deployment and operational disruptions.
Mitigation Strategies
- Version Upgrades: Migrate to Airflow ≥2.0, which mandates authentication for REST API endpoints and scrubs sensitive logs.
- Network Segmentation: Restrict instance access via IP whitelisting and VPNs.
- Secrets Management: Integrate with Vault or AWS Secrets Manager instead of using Variables.
- Code Reviews: Implement pre-commit hooks to detect hardcoded credentials using tools like detect-secrets.
detect-secrets scan --update .secrets.baselineAs organizations accelerate workflow automation, securing orchestration platforms becomes non-negotiable.
The exposed instances—many running versions deprecated since 2020—underscore the urgency of patch management and DevSecOps integration.
Cybersecurity teams must audit Airflow deployments for these misconfigurations before attackers exploit them at scale.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



