Researchers detected an attack involving a fake KMSPico activator tool, which delivered Vidar Stealer through several events.
The attack leveraged Java dependencies and a malicious AutoIt script to disable Windows Defender and decrypt the Vidar payload via the shellcode.
The user performed a web search for KMSPico and browsed to the top result (kmspico[.]ws), which is marketed as a “universal activator” for Windows but appears to no longer be maintained.
The site is hosted behind Cloudflare Turnstile and requires human input to download the final Zip package, a tactic to hide the page and final payload from automated web crawlers.
The Malicious Package
The ZIP archive contains Java dependencies and the malicious executable Setuper_KMS-ACTIV.exe.
Analyze any MaliciousURL, Files & Emails & Configuration With ANY RUN : Start your Analysis
Upon launching the executable, javaw.exe starts, disabling behavior monitoring in Windows Defender and dropping the malicious AutoIt script named “x” along with AutoIt named Flour.pif.
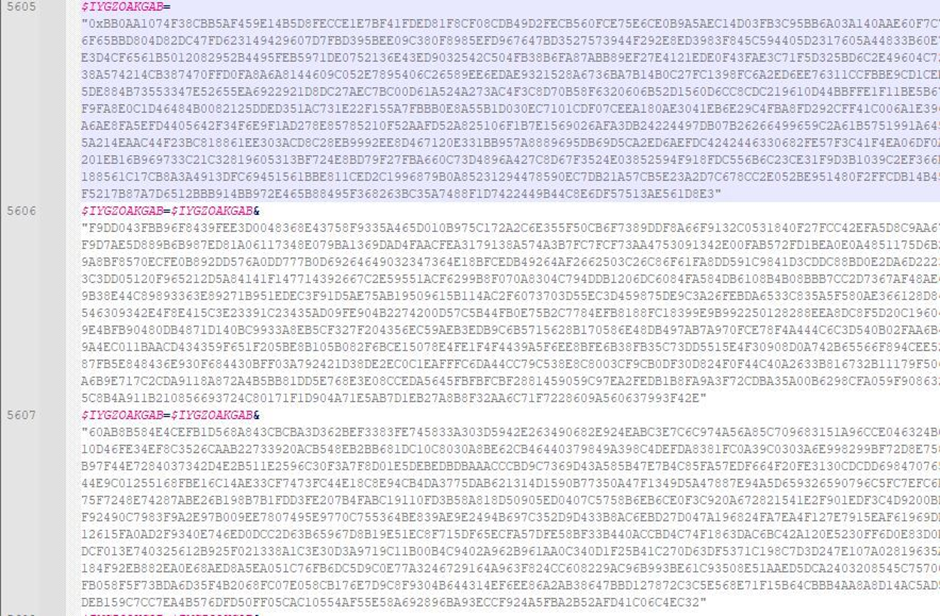
The AutoIt script contains the encrypted Vidar payload that will be injected into the current running AutoIt process.
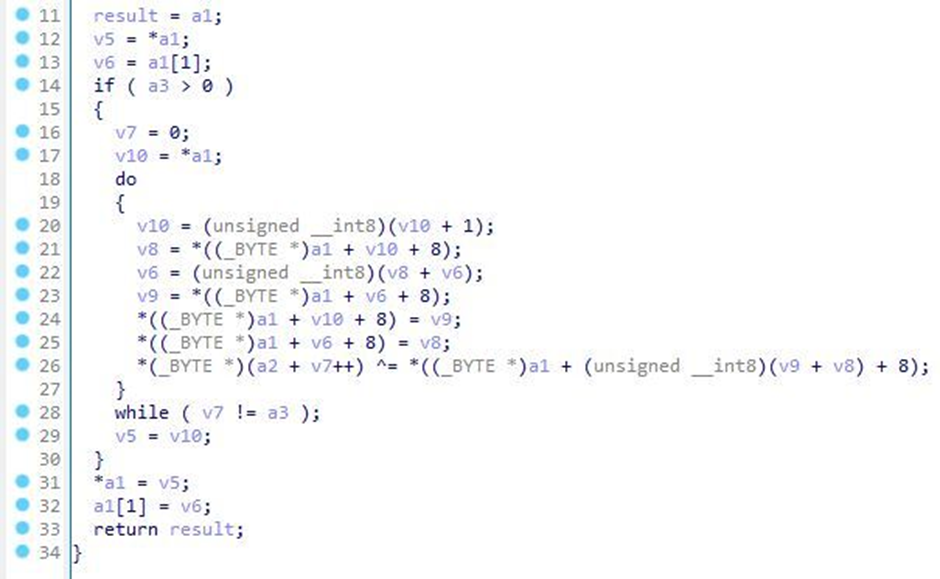
The shellcode is responsible for decrypting the Vidar payload using the RC4 decryption algorithm, which is obfuscated by a hardcoded key in the malicious AutoIt script.
The Command and Control Infrastructure
Vidar Stealer uses Telegram for the Dead Drop Resolver (DDR) to store the C2 IP address.

Threat actors use a dead drop resolver to host command and control (C2) information on legitimate external web services. They embed and often obfuscate domains or IP addresses within content posted on sites and popular applications such as Telegram and Stealer, thus concealing the C2 infrastructure.
The Response
eSentire’s 24/7 SOC Cyber Analysts team isolated the affected host and notified the customer of suspicious activities, providing additional support and remediation.
This incident reminds us that malware-laden applications, particularly greyware piracy tools, are hidden in plain sight among web search results. It stresses the importance of user awareness to guard against such threats.
Using a fake KMSpico activator tool as a malware delivery vector highlights the importance of avoiding illegal software activators and ensuring that all software is obtained from legitimate sources.
The attack, which leveraged Java dependencies and a malicious AutoIt script to disable Windows Defender, underscores the necessity of maintaining up-to-date security software and implementing additional layers of defense to detect and prevent such malicious activities.
Recommendations
eSentire’s Threat Response Unit (TRU) recommends implementing the following controls to help secure your organization against Vidar Stealer malware:
- Confirm that all devices are protected with Endpoint Detection and Response (EDR) solutions.
- Implement a Phishing and Security Awareness Training (PSAT) program that educates and informs your employees on emerging threats in the threat landscape.
- Encourage employees to use password managers instead of web browsers’ password storage features. Use master passwords where applicable.
Organizations can better protect themselves against the ever-evolving threat landscape by staying vigilant and following these recommendations.
Looking for Full Data Breach Protection? Try Cynet's All-in-One Cybersecurity Platform for MSPs: Try Free Demo



.png
)
