Microsoft Urges users to patch for BlueKeep RDP vulnerability as it could result in more effective attacks. The Bluekeep exploit can be used to deliver to more notorious malware.
On November 2, 2019, security researcher Kevin Beaumont spotted the RDP attacks that could crash the machine, Marcus Hutchins who analyzed the dumps says that hackers leveraging the Bluekeep vulnerability to install Monero Cryptocurrency miner.
Bluekeep(CVE-2019-0708) is a wormable critical RCE vulnerability in Remote desktop services that let hackers access the vulnerable machine without authentication. As vulnerability is wormable, it could rapidly compromise millions of machines in a short period.
Bluekeep Metasploit Module
Microsoft researchers connected the previous coin mining attack campaign in September with the October BlueKeep Metasploit campaign. Both the campaigns connected to the same command-and-control infrastructure and they are aimed to install a coin miner.
“This indicated that the same attackers were likely responsible for both coin mining campaigns—they have and they are incorporating the BlueKeep exploit into their arsenal.”
Microsoft worked with the researchers to investigate the crashes and they confirmed BlueKeep exploit module for the Metasploit penetration testing framework used.
The exploit module used in the attack found to be unstable as it resulted in several crashes. Microsft has built a behavioral detection so that Microsoft Defender ATP customers are protected from the Metasploit module that hit’s Beaumont honeypots.
Microsoft analysis shows that an increase in RDP-related crashes due to the unstable BlueKeep Metasploit module.
Coin Miner Campaigns
The attacks launched as a port scanner’s, if the scanner spotted any vulnerable internet-facing RDP machine, it employs the BlueKeep Metasploit module to run a PowerShell that downloads another encoded Powershell’s from the attackers’ server.
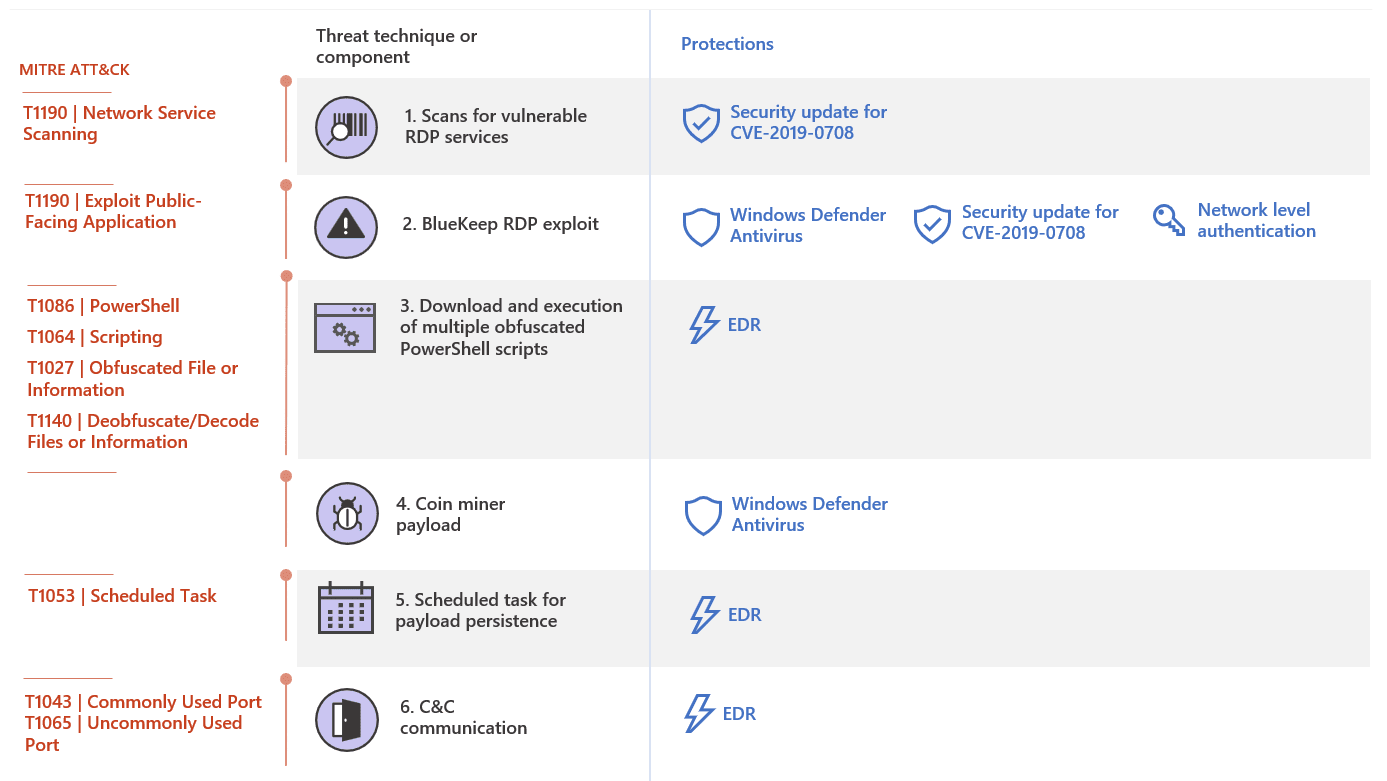
Once these encoded Powershell’s are executed, they download the final coin miner payload and the coin miner payload connected with command-and-control infrastructure at 5[.]100[.]251[.]106.
Beaumont added that “another IP 193[.]104[.]205[.]59 is actively exploiting BlueKeep vulnerability, this one against a honeypot in Singapore.”
The following are the countries that show the presence of coin miner payload used in these attacks, based on Microsoft machine learning models.
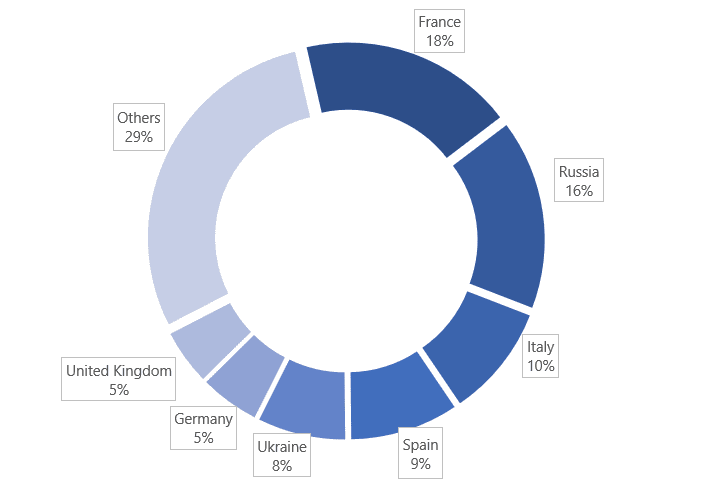
Microsoft urges user’s to apply the patch, it may emerge as a serious threat and it can be exploited without leaving traces.
Mitigations
- Block Remote Desktop Services if they are not in use.
- Block TCP port 3389 at the Enterprise Perimeter Firewall.
- Apply the patch to the vulnerable Machines that have RDP Enabled
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and Hacking News update.



.png
)
