It turns out that Akamai’s team of researchers accidentally killed a newly discovered cryptocurrency mining botnet known as KmsdBot during the investigation.
Due to a syntax error, the botnet was unable to send commands any longer, and as a result, it was destroyed.
KmsdBot and its C2 functionality
KMSDBot is a cryptomining botnet that uses weak credentials and SSH to infect its victims with a crypto-mining malware and then deploy the miner. Apart from this, the KmsdBot is equipped with command-and-control capabilities.
After one of Akamai’s honeypots was contaminated with the botnet, the Akamai team assessed the situation and reported on it.
A variety of microarchitectures were used in the botnet’s deployment to target Linux and Windows devices, and on these devices, it deploy the following components:-
- Miners
- DDoS bot army
It primarily targets firms that are involved in gaming and technology, as well as manufacturers of luxury vehicles.
It is imperative to note that the ability to gain C2 is arguably the most lethal aspect of any malicious entity, and KmsdBot is the one that has the C2 functionalities.
Event Information
Researchers from Akamai reported that the operating mechanism of the botnet in a controlled environment, they sent commands that mistakenly neutralized the malware.
A bot stopped sending commands as soon as it received a command that was improperly formatted. A possible reason for this could be that the program was not built with an internal error-checking feature that would check the commands coming into its source code for errors before they were executed.
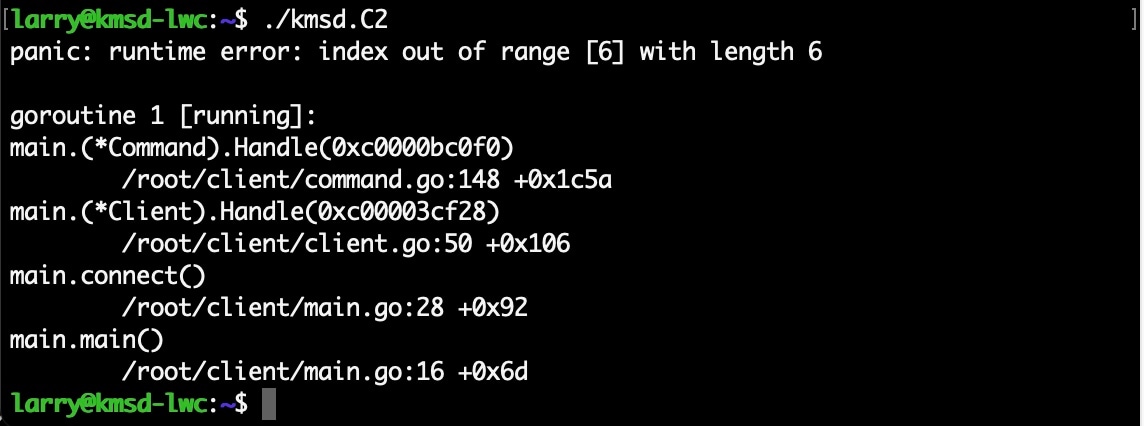
On the infected devices, the Go binary stop interacting with its C2 server, as a result when the instruction is given to the target website without a space between the port number.
A persistence mechanism is not present in the botnet, due to its lack of functionality. In short, in the event of detection, the operators of the botnet will need to re-infect the target device.
As a result, this can be seen as an example of how technology is capricious, and how even the person who is exploiting it may find themselves exploited, too.
Secure Web Gateway – Web Filter Rules, Activity Tracking & Malware Protection – Download Free E-Book



.png
)
