Fluent Bit, a widely used open-source data collector and processor, has been found to have a major memory loss flaw.

Many big cloud providers use Fluent Bit for their logging because it is easy to use and can be scaled up or down as needed.
Tenable Research found the flaw, which affects Fluent Bit’s built-in HTTP server and has been designated CVE-2024-4323.
This bug could cause a denial of service (DoS), the loss of information, or the execution of code from afar (RCE).
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
Technical Details
A security flaw in a cloud service was being looked into when the weakness was found.
Researchers discovered they could access several metrics and logging URLs, such as several Fluent Bit instances.
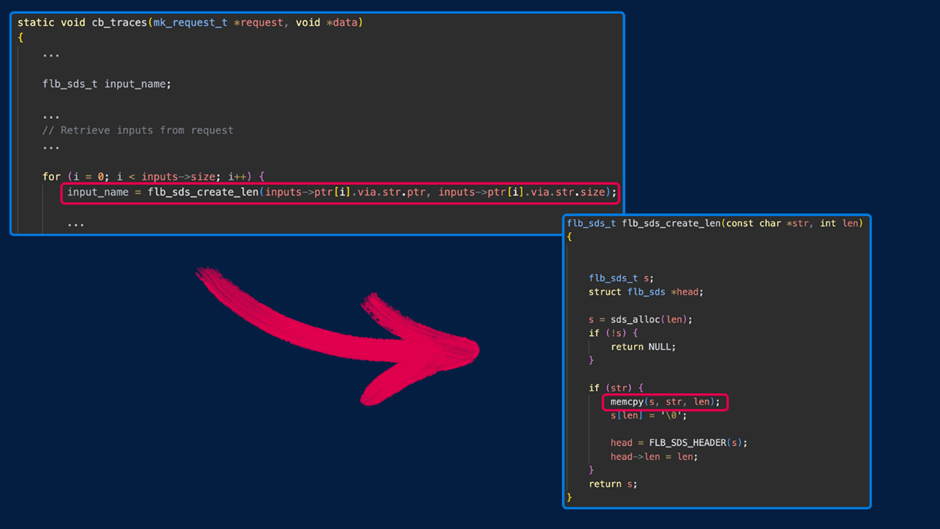
The problem happens because the data types in the “inputs” array of calls to the /api/v1/traces endpoint are not correctly checked.
It can damage memory by sending numbers that aren’t strings, like integers.
This could cause the program to crash, send too much data to the heap, or lose data.
CVE-2024-4323: A Closer Look
There are a few ways to take advantage of the memory corruption bug in Fluent Bit’s tracking API:
- Large Integer Values: A “wild copy” in a later call to memcpy() could cause the program to crash.
- Negative Values: Values between 1 and 16 can cause the heap to overwrite memory next to them.
- Small Integer Values: This can let the client see memory that is close by. If the value is -17, it leads to a crash because of a null pointer dereference after a failed malloc() of zero.
- Targeted Integer Values: The following values can cause stack corruption and other memory corruption problems.
The experts used this flaw in the lab to crash the service and set off a denial-of-service event.
They could also get back pieces of memory next to each other, which sometimes revealed parts of secrets and could mean that information was getting out.
Mitigation and Recommendations
Fluent Bit’s developers were notified of the problem on April 30, 2024, and a fix was added to the project’s main branch on May 15, 2024.
The fix includes ensuring the data types in the “inputs” array are correct.
It is suggested that users update to the newest version (3.0.4) as soon as it comes out.
If you can’t upgrade, you should look at Fluent Bit’s monitoring API and make sure that only approved users can access it.
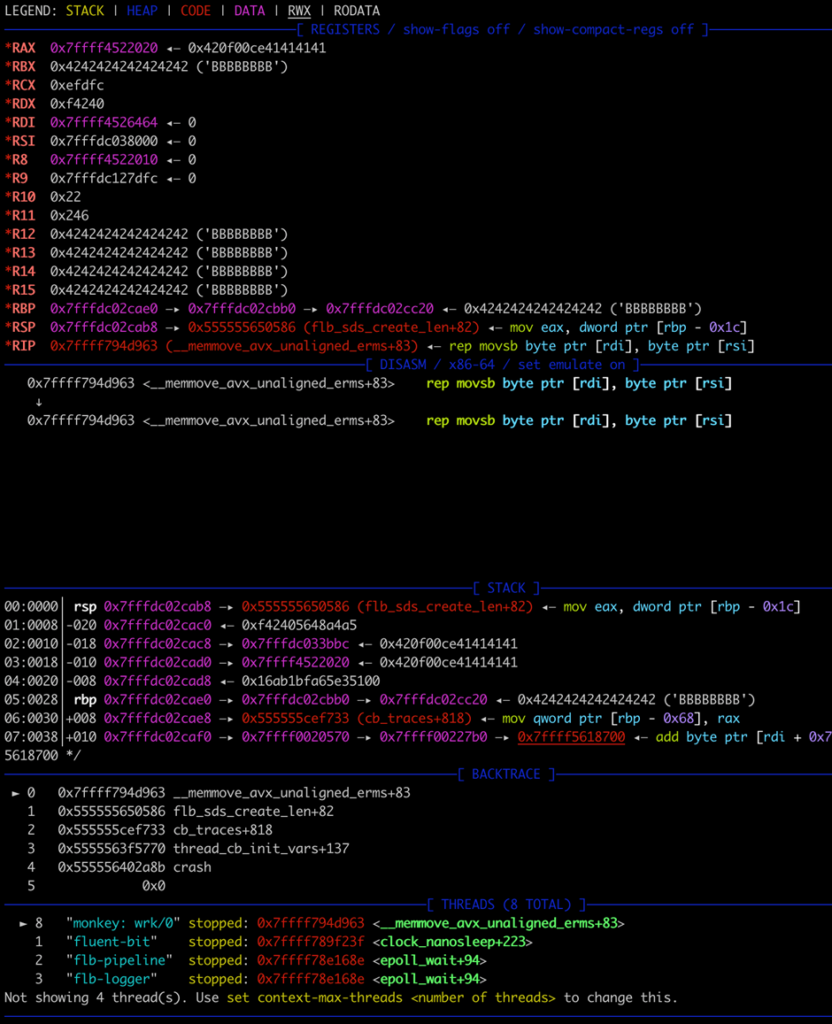
The above debugger output indicates a heap-buffer overflow, but ultimately, the crash is caused by an attempt to write to a protected memory region.
If you depend on cloud services that use Fluent Bit, you should contact the cloud source to ensure you get any updates or fixes as soon as possible.
Big cloud service companies like Microsoft, Amazon, and Google have been told about the problem.
The discovery of CVE-2024-4323 shows the importance of logging and monitoring tools to get regular updates and strict security measures.
Businesses need to use defense-in-depth strategies and the concept of least privilege to prevent attackers from abusing their power.
Since logging infrastructure is an important part of both cloud-based and on-premises settings, fixing these problems immediately is necessary to maintain security.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
.webp?w=696&resize=696,0&ssl=1)


.png
)
