SAP has issued Security Note 3536965 to address multiple high-severity vulnerabilities in the Adobe Document Services of SAP NetWeaver AS for JAVA.
These vulnerabilities, identified as CVE-2024-47578, CVE-2024-47579, and CVE-2024-47580, allow attackers to manipulate or upload malicious PDF files, potentially compromising internal systems and exposing sensitive data.
Details of the Vulnerabilities
CVE-2024-47578: Server-Side Request Forgery (SSRF)
This flaw allows attackers with administrative privileges to send specially crafted requests from a vulnerable web application.
Exploiting this vulnerability, attackers can access internal systems behind firewalls, read or modify sensitive files, and even disrupt system availability. Businesses could face operational downtime due to this severe disruption.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
CVE-2024-47579: Unauthorized File Manipulation
This vulnerability enables attackers, with administrative rights, to exploit an exposed web service, uploading or downloading custom PDF font files.
By abusing this functionality, attackers can embed server files into font files and access sensitive data without impacting system availability or functionality.
CVE-2024-47580: PDF File Vulnerability
Here, attackers can create PDFs containing embedded attachments referencing internal server files.
When these PDFs are downloaded, they provide unauthorized access to sensitive server files, leaving the system’s integrity intact but exposing confidential data.
These vulnerabilities pose severe threats, including unauthorized access to sensitive business data, intellectual property, and private information.
Exploitation of the SSRF vulnerability could allow attackers to pivot within internal networks, amplifying the potential damage. Such breaches not only risk regulatory non-compliance but also cause reputational harm and financial losses.
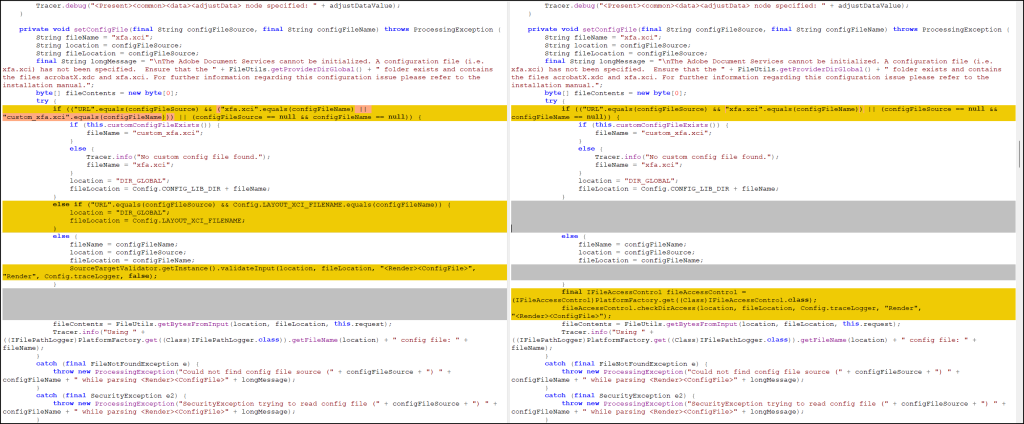
According to the Redray report, SAP recommends applying Security Note 3536965 to patch these vulnerabilities in all affected SAP NetWeaver AS for JAVA environments. Key steps for mitigation include:
- Patch Deployment
Install the patch without delay in all impacted systems. Ensure Adobe Document Services is updated to the recommended patch level. - Testing & Monitoring
After applying the patch, thoroughly test the system to confirm the vulnerabilities have been resolved. Regular monitoring of application logs is crucial for detecting potential prior exploitation. - Access Controls
Implement the principle of least privilege to restrict administrative access. Enable multi-factor authentication (MFA) for all privileged accounts. - Network Segmentation
Isolate SAP NetWeaver AS for JAVA environments from other network segments, and adjust firewall settings to limit unnecessary traffic to and from Adobe Document Services. - Regular Security Audits
Conduct vulnerability scans and penetration testing to proactively identify and address security gaps.
Enterprises should automate patch management to minimize exposure time to vulnerabilities and encourage security awareness among employees.
Regularly reviewing SAP Security Notes and maintaining an incident response plan can further enhance organizational resilience against cyberattacks.
The discovery of CVE-2024-47578, CVE-2024-47579, and CVE-2024-47580 highlights the urgent need for proactive security measures.
Applying SAP’s recommended patches and implementing robust defenses will help organizations mitigate risks and maintain operational stability.
Investigate Real-World Malicious Links,Malware & Phishing Attacks With ANY.RUN - Try for Free



.png
)
