Researcher uncovered a critical chain of vulnerabilities in Popular EA’s Origin gaming client allows attackers to take over the players account and committing the identity theft against 300 Million EA Gamers.
EA (Electronic Arts) is a second largest American based video gaming company who is behind the some of the most famous games including EA Sports titles FIFA, Madden NFL, NHL, NBA Live, and UFC.
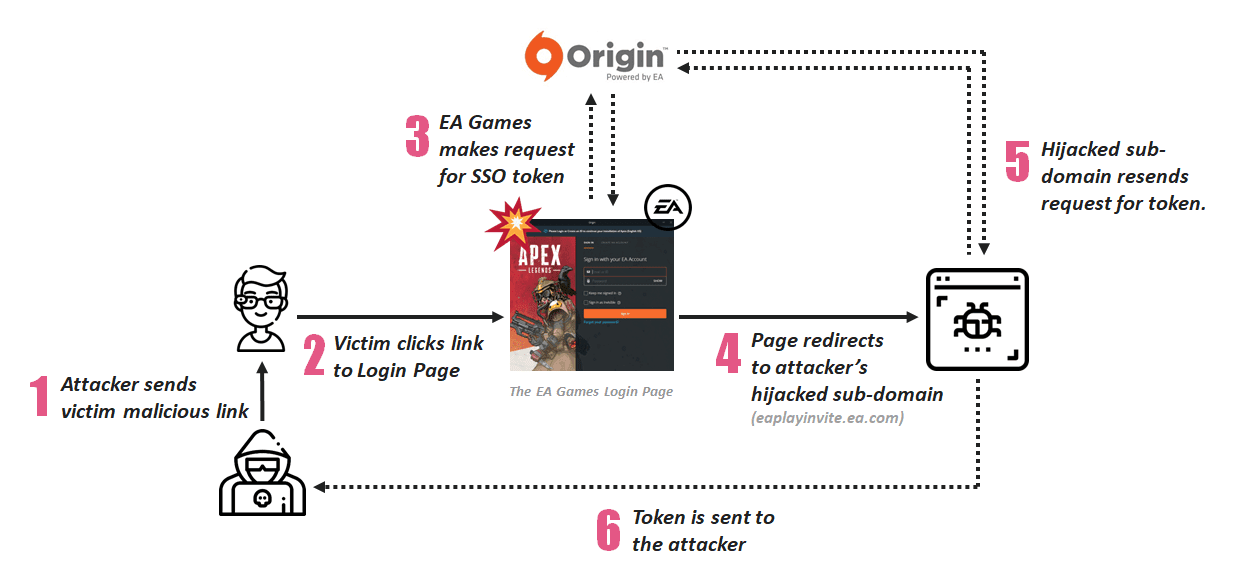
The vulnerability resides in the EA origin game client platform can be exploited by abusing the authentication token that used for abandoned subdomains with the OAuth Single Sign-On (SSO) and users login process Trust mechanism.
There are several domains including ea.com and origin.com used by EA to provide different services for its gamers that helps users to create a new account and guide to purchase new games in the EA store.
EA Games also configured some of the subdomains under the main domains with DNS address and CNAME records.
During the coordination research conducted by CyberInt and Check Point analyzed one of the EA Games subdomain eaplayinvite.ea.com which is configured with a DNS CNAME and it is pointed to another subdomain ea-invite-reg.azurewebsites.net.
The subdomain used by EA Games hosted in Microsoft Azure (ea-invite-reg.azurewebsites.net) was no longer in use, but the alias record still exists with eaplayinvite.ea.com.
So the researchers opted to register “ea-invite-reg” with Azure that allows them to hijack the subdomain “eaplayinvite.ea.com “ along with the interception of any legitimate EA Games’ user requests.”
According to cyberint, “Having seized control of the eaplayinvite.ea.com subdomain guided research toward the new goal of examining how the TRUST mechanism between EA Games’ ea.com or origin.com domains and their subdomains could be abused to manipulate the OAuth protocol implementation for full account take-over/exploitation”
In results, Researchers figured out that the EA games oAuth SSO implementation within several EA services such as answers.ea.com, help.ea.com, and accounts.ea.com.
“The SSO mechanism exchanges the user credentials (username & password) by unique SSO Token and this token can be used to authenticate any platform that belongs to EA network.”
So if the attacker steals the SSO Token by sending the specially crafted malicious link to victims, it gives them an active login session, eventually trigger the authentication to hijack the victim’s account.
Watch the demonstration about how an attacker hijacking the gamers live session to compromise their entire account and gain access to their sensitive data.
According to Oded Vanunu, Head of Products Vulnerability Research for Check Point, “EA’s Origin platform is hugely popular; and if left unpatched, these flaws would have enabled hackers to hijack and exploit millions of users’ accounts,”
This critical vulnerability not only provides access to the gamers account but it allows the attacker to purchase the virtual currency using the user’s credit card.
In order to avoid such attacks and protect from session hijacking, Check Point and CyberInt strongly advise users to enable two-factor authentication and only use the official website when downloading or purchasing games.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.



.png
)
