A critical authentication vulnerability in Fortinet’s FortiGate SSL VPN appliance tracked as CVE-2024-55591, has been weaponized in active attacks.
Threat actors have exploited this vulnerability to gain super-admin privileges, bypassing the authentication mechanism, and compromising devices globally.
Cybersecurity experts warn organizations using vulnerable Fortinet systems to patch immediately to prevent catastrophic breaches.
Fortinet’s Authentication Vulnerability Explained
The vulnerability resides in FortiOS’s JS console functionality, which provides administrators with a CLI (Command Line Interface) console via a web-based GUI.
A critical flaw in this feature allows attackers to establish unauthorized WebSocket connections and bypass authentication layers to gain access to an all-powerful CLI.
Are you from SOC/DFIR Teams? - Analyse Malware Files & Links with ANY.RUN Sandox -> Try for Free
What makes CVE-2024-55591 particularly dangerous is that it chains multiple issues:
- Authentication Bypass via Alternate Path:
The vulnerability enables attackers to utilize the local_access_token parameter in the query string to trick FortiOS into thinking it’s handling a legitimate session. This bypasses standard session verification checks. - WebSocket Exploitation:
The attack leverages a race condition in the WebSocket-to-Telnet connection mechanism, allowing unauthorized access to Fortinet’s CLI process via a crafted WebSocket request. - Privilege Escalation:
By injecting crafted JSON payloads, attackers can assign themselves a “super_admin” role, granting unrestricted access to the appliance’s administrative functions. - Exploitation in the Wild:
Arctic Wolf first discovered the vulnerability being exploited before public disclosure. This aligns with reports of weaponized exploits used against unpatched FortiOS deployments worldwide.
In-The-Wild Exploitation and Critical Impact
The exploit’s power lies in creating a backdoor super-admin account unnoticed post-attack.
Compromising a FortiGate device often translates to unrestricted access to corporate networks, enabling attackers to launch ransomware, exfiltrate sensitive data, and spread laterally across an organization.
Arctic Wolf’s investigation revealed Indicators of Compromise (IoCs) with adversaries leveraging the CLI to execute privileged commands stealthily.
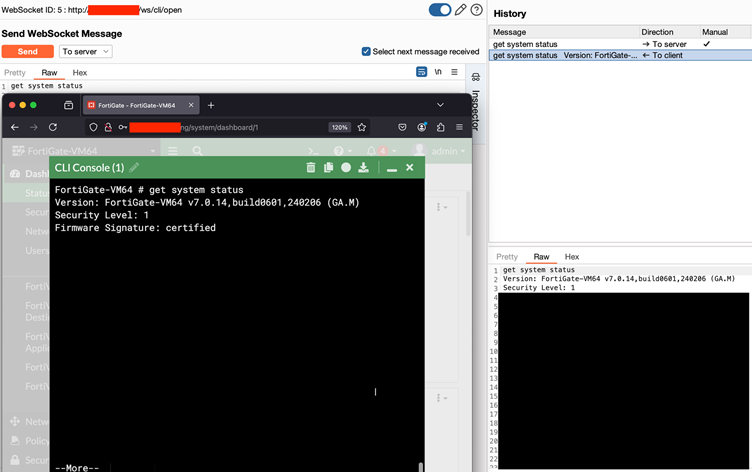
Logs show exploitation attempts targeting /ws/cli/open endpoints via WebSockets, marking the attack as deliberate and precise.
Shadowserver Foundation, monitoring global FortiGate deployments, reported at least 50,000 exposed and vulnerable systems still online as of January 2025. This highlights the urgency for organizations to patch affected systems.
Technical Insights into CVE-2024-55591
Upon reviewing Fortinet’s advisory and analyzing the vulnerable code, researchers identified that the flaw exists primarily in how dispatch() authenticates WebSocket connections. During the attack:
- The Node.js server function dispatch() mishandles session verification, allowing attackers to trick it using a crafted local_access_token.
- A race condition within the WebSocket connection logic lets attackers interact with the appliance’s Telnet-based CLI process without proper credentials.
Using this exploit:
- Attackers send a pre-authenticated WebSocket request to the /ws/cli/ endpoint.
- They inject malicious values to force Telnet CLI access by racing the authentication sequence.
- The payload can escalate privileges and execute arbitrary commands on the device.
According to the WatchTowr report, Fortinet acknowledged the vulnerability in a public advisory, urging customers to apply patches for affected versions of FortiOS and FortiProxy.
The advisory states: “An Authentication Bypass Using an Alternate Path or Channel vulnerability [CWE-288] may allow a remote attacker to gain super-admin privileges via crafted requests to the Node.js WebSocket module.”
Mitigation Steps:
- Update Software: Apply patches provided in Fortinet’s PSIRT FG-IR-24-535 immediately.
- Restrict Management Access: Ensure administrative interfaces are not exposed to the open internet.
- Monitor IoCs: Use detection tools and logs to identify exploitation attempts, such as suspicious WebSocket traffic targeting CLI endpoints.
Security researchers have emphasized the need for manufacturers to adopt stringent testing and minimize reliance on monolithic architectures like Fortinet’s Node.js implementation, which can harbor latent, high-impact vulnerabilities.
For now, organizations relying on FortiGate appliances are advised to patch promptly and conduct thorough security audits of their networks. As always, prevention begins with vigilance.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
