Analyzing malware has become increasingly challenging, especially with the growing popularity of programming languages like Golang.
Golang, or Go, has captivated developers for its extensive features but has also proven to be an attractive choice for malware authors, thanks to its embedded libraries, sizable binaries, and potential for obfuscation.
To combat these challenges, Volexity has introduced GoResolver, an innovative, open-source tool designed to simplify the reverse engineering of obfuscated Golang malware.
The Rise of Golang in Malware Development
Golang has emerged as a preferred language for malware developers due to its capability to produce binaries with embedded libraries, making them harder to deconstruct.
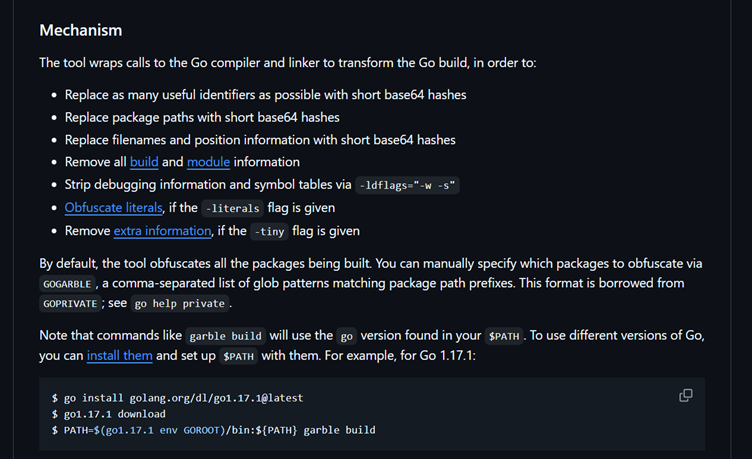
Reverse engineers often struggle with analyzing Golang binaries due to their sheer size and complexity. This difficulty is compounded when obfuscation tools like Garble are used to obscure function and package names.
Garble’s obfuscation properties strip symbol tables and randomize names, making manual static analysis tedious and time-consuming.
Volexity’s investigations frequently encounter Golang malware, prompting the need for advanced solutions to address the challenges posed by such obfuscators. GoResolver was developed in response to this need.
Introducing GoResolver
GoResolver is a groundbreaking open-source tool that leverages control-flow graph similarity techniques to resolve obfuscated function names.
By analyzing the paths a binary takes during execution, GoResolver can identify similarities between control-flow graphs of obfuscated and clean binaries, restoring symbol information that would otherwise be lost.
Key features of GoResolver include:
- Symbol Recovery: Retrieves obfuscated function and package names.
- Control-Flow Graph Analysis: Identifies graph similarities to recover original symbol information.
- Integration with Popular Tools: Provides plugins for IDA Pro and Ghidra to streamline workflows.
- Open-Source Accessibility: Available for download on GitHub, encouraging collaboration and continuous improvement.
Tackling Garble Obfuscation
Garble is a widely used Golang obfuscator that presents unique challenges. While it strips symbol tables and randomizes names, the obfuscation reveals patterns that GoResolver can exploit.
For example, Garble’s randomized names must remain consistent within a package, enabling analysts to infer package identities.
Using this logic, GoResolver improves symbol recovery by associating functions with their respective packages.
Additionally, GoResolver bypasses obfuscation limitations by fingerprinting Golang runtime versions.
By testing similarities among runtime fragments, GoResolver efficiently identifies the exact Golang version used to compile the malware, enabling accurate binary analysis.
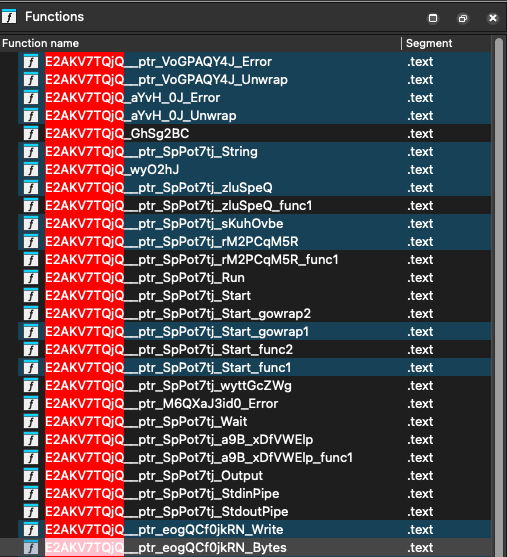
Volexity demonstrated GoResolver’s capabilities by analyzing a Garble-obfuscated Stowaway agent. Initially, disassembled binaries contained generic names, complicating analysis.
When submitted to GoResolver, the tool identified the Golang version through runtime fingerprinting and resolved obfuscated symbols.
Using control-flow graph similarity, GoResolver restored meaningful function names and package associations, allowing analysts to focus on the malware’s core logic rather than runtime and library methods.
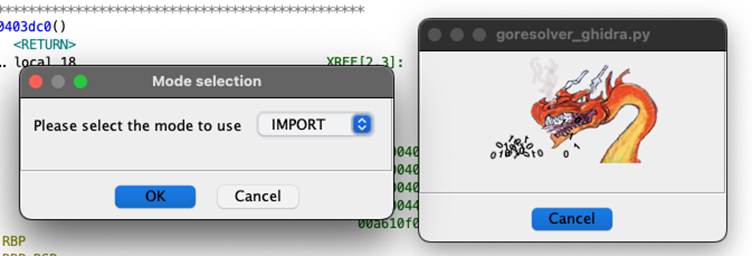
Integration with IDA Pro and Ghidra
To expedite workflows, GoResolver offers plugins for IDA Pro and Ghidra, two of the most widely used reverse-engineering platforms.
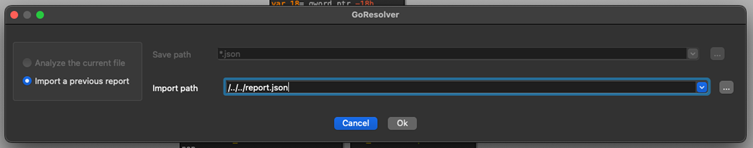
Analysts can choose between analyzing samples directly within the tools or importing pre-generated symbol reports. These plugins enhance efficiency, ensuring seamless integration into malware analysis operations.
GoResolver is a pioneering tool that addresses the growing challenge of reverse-engineering obfuscated Golang malware.
By combining symbol extraction techniques with control-flow graph analysis, GoResolver offers unparalleled capabilities for retrieving lost symbol information and understanding binary layouts.
It empowers cybersecurity analysts to focus on core malware functionality, improving the efficiency of forensic investigations.
Volexity plans to expand GoResolver’s capabilities, including features like automatic Golang string parsing and enhanced binary analysis.
The tool is available for download on GitHub, and the repository will continue to be updated with new features and enhancements.
For cybersecurity professionals tackling Golang malware, GoResolver is a must-have in their arsenal, ensuring deeper insights and faster analysis to combat emerging threats effectively.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
