Several critical vulnerabilities affecting Mali Graphics Processing Units (GPUs) have surfaced, allowing hackers to exploit flaws in GPU drivers to gain full control of devices.
The vulnerabilities tracked as CVE-2022-22706 and CVE-2021-39793, expose millions of devices to privilege escalation attacks, enabling attackers to bypass security mechanisms, manipulate memory permissions, and execute arbitrary code as a root user.
Technical Breakdown: How the Flaw Works
At the core of the issue is the kbase_jd_user_buf_pin_pages() function in the Mali GPU kernel driver.
This function, responsible for managing GPU operations and memory buffer permissions, fails to correctly enforce permission flags.
Specifically, it checks only the KBASE_REG_GPU_WR flag (representing GPU write access) and ignores the KBASE_REG_CPU_WR flag (indicating CPU write access).
This oversight opens the door for malicious applications to gain write access to read-only memory regions, granting privileges they should not have. The affected drivers include the following versions:
- Midgard GPU Kernel Driver: r26p0 to r31p0
- Bifrost GPU Kernel Driver: r0p0 to r35p0
- Valhall GPU Kernel Driver: r19p0 to r35p0
Proof-of-Concept Exploit
According to the Star Labs Report, Researchers demonstrated how these vulnerabilities are exploited to gain root access:
Exploit Steps
- Memory Manipulation: Hackers first allocate a memory page with write permissions and then exploit the driver to manipulate its mapping, bypassing restrictions.
- Hijacking Kernel Processes: Using their newfound write access, attackers can tamper with privileged system processes such as init or vold.
- Escalating Privileges: By targeting the init process (the parent process in Android devices), hackers can disable SELinux (Android’s key security enforcement mechanism) and execute arbitrary code.
- Root-Level Reverse Shell: With SELinux disabled, a reverse shell payload is executed, allowing remote attackers to gain root access and complete control of the compromised device.
Here’s code from the patched driver highlighting the fixed vulnerability:
@@ -1683,7 +1683,8 @@
kbase_jd_user_buf_unmap(kctx, reg->gpu_alloc,
- (reg->flags & KBASE_REG_GPU_WR));
+ (reg->flags & (KBASE_REG_CPU_WR | KBASE_REG_GPU_WR)));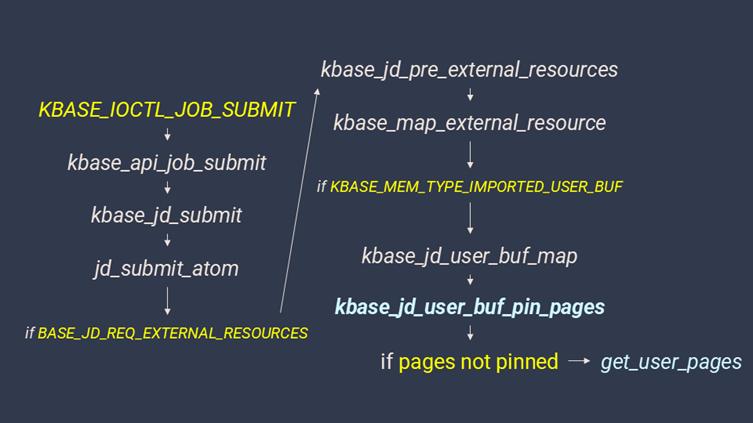
The fix introduces the KBASE_REG_CPU_WR flag check alongside KBASE_REG_GPU_WR, ensuring both CPU and GPU write permissions are validated.
The exploit underscores the severity of hardware-level vulnerabilities. Attackers leveraging this technique can:
- Steal Personal Data: Photos, documents, and other sensitive information can be exfiltrated.
- Spy on Conversations: Microphones and cameras may be activated remotely.
- Brick Devices: Attackers could render devices unusable by corrupting critical system components.
A key demonstration of the attack involved achieving a root reverse shell, bypassing SELinux enforcement and using malicious payloads to hijack system processes like vold and init.
The following Termux output shows how the exploit originates from an unprivileged app user:
~ $ cat /proc/self/attr/current
u:r:untrusted_app_27:s0:c222,c256,c512,c768
~ $ id
uid=10222(u0_a222) gid=10222(u0_a222) groups=10222(u0_a222),3003(inet),9997(everybody)The vulnerabilities in Mali GPU drivers serve as a stark reminder of the growing sophistication of hardware-level exploits.
The phrase “Hackers Can Exploit GPU Flaws to Gain Full Control of Your Device” is no longer a hypothetical scenario—it’s a reality that underscores the importance of timely security updates and heightened user vigilance.
If you’re using a device with Mali GPU drivers, take immediate action to update your software or patch the vulnerabilities to safeguard your data and privacy.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
