A sophisticated remote access trojan (RAT) dubbed SnowDog has surfaced on underground cybercrime forums, prompting alarms among cybersecurity experts.
Advertised as a tool for “corporate espionage and advanced intrusions,” the malware is being sold by an unidentified threat actor with claims of stealth, evasion, and remote control capabilities.
The SnowDog RAT: Features and Risks
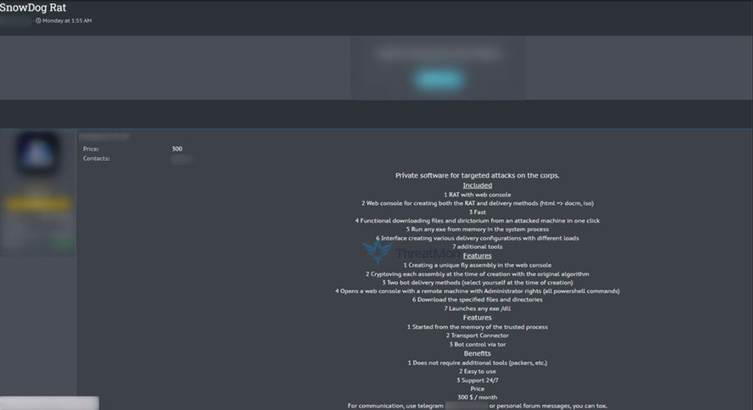
The seller claims SnowDog RAT is tailored for covert operations, enabling attackers to infiltrate corporate networks, exfiltrate sensitive data, and maintain persistent access. Key features include:
- Web-Based Control Panel: Allows hackers to manage compromised devices from any browser, with real-time monitoring of infected systems.
- Multiple Distribution Vectors: Phishing emails, malicious ads, fake software downloads, and exploit kits to breach targets.
- Stealth Execution: Code obfuscation and anti-analysis techniques to evade endpoint security tools.
- Cryptographic Protection: Data encryption for command-and-control (C2) communications, masking malicious traffic as legitimate HTTPS traffic.
A listing reviewed by cybersecurity analysts indicates the RAT can log keystrokes, hijack webcams, extract credentials, and deploy secondary payloads like ransomware.
The seller has priced the malware at an undisclosed amount, offering “lifetime access” and customer support to buyers.
SnowDog’s features suggest a focus on high-value targets, including technology firms, financial institutions, and healthcare organizations.
“This isn’t a script kiddie tool—it’s designed for persistent, long-term espionage,” said Mira Patel, a threat intelligence analyst at SecuRight.
“The encryption and stealth mechanisms make it particularly dangerous for enterprises lacking advanced threat detection.”
Recent months have seen a surge in RAT-based attacks, with a 2025 IBM report noting a 34% year-over-year increase in corporate cyber-espionage incidents.
SnowDog’s emergence aligns with growing demand for “as-a-service” malware, lowering the barrier for less skilled criminals to launch complex attacks.
Mitigation Strategies for Organizations
To counter such threats, experts recommend:
- Employee Training: Regular phishing simulations to reduce click-through rates on malicious links.
- Network Segmentation: Isolate critical systems to limit lateral movement during breaches.
- Multi-Factor Authentication (MFA): Prevent credential theft from granting full network access.
- Endpoint Detection and Response (EDR): Deploy tools to flag unusual activities, such as unexpected data transfers or registry changes.
“Real-time monitoring and zero-trust frameworks are essential to detect RATs like SnowDog,” advised Carlos Mendez of CyberDefense Solutions. “Assume breaches will happen and focus on rapid containment.”
Interpol’s Cybercrime Division has flagged SnowDog-related forums for takedown while cybersecurity firms analyze samples to develop detection signatures. However, the malware’s modular design complicates reverse-engineering efforts.
Authorities urge organizations to report suspicious activity, noting that RATs often lie dormant for weeks before activating.
“The longer a RAT remains undetected, the more damage it can inflict,” warned INTERPOL’s Elena Rivera.
As cybercriminals monetize advanced tools, enterprises must prioritize proactive defense measures. SnowDog’s sale underscores a worrying trend: off-the-shelf malware now rivals nation-state arsenals in sophistication.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



