A sweeping wave of suspicious online activity is putting organizations on alert as hackers ramp up their efforts to probe vulnerabilities in Ivanti Connect Secure (ICS) and Ivanti Pulse Secure (IPS) VPN systems.
Cybersecurity firm GreyNoise has identified a dramatic nine-fold increase in suspicious scanning activity, suggesting coordinated reconnaissance that could foreshadow future exploitation.
According to GreyNoise, more than 230 unique IP addresses targeted ICS and IPS VPN endpoints on April 18 alone—a sharp escalation from the typical daily average of fewer than 30.
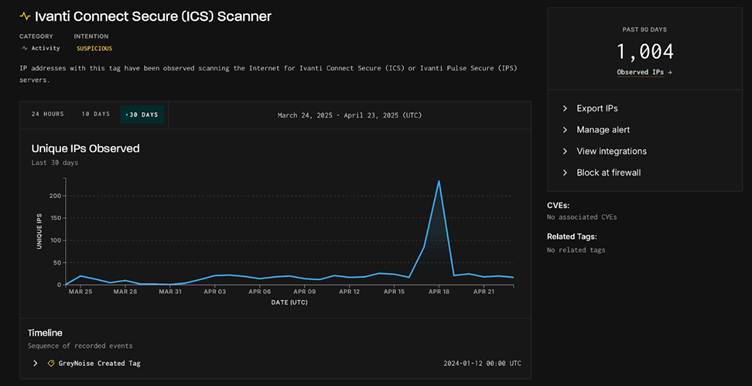
Even more concerning, over the past 90 days, the number of unique IPs involved in similar activity soared to 1,004.
“This isn’t just isolated noise,” a GreyNoise spokesperson explained. “Spikes like this are often the prelude to more serious threats, particularly as attackers look for new vulnerabilities before they’re publicly disclosed.”
Threat Landscape
The cybersecurity firm’s analysis paints a detailed picture of the infrastructure behind these probes:
- Malicious IPs (244 total): Many are routed through Tor exit nodes and well-known cloud or virtual private server (VPS) providers, making them difficult to track and block.
- Suspicious IPs (634 total): These tend to use lesser-known or niche hosting platforms and less mainstream cloud infrastructure, often to avoid detection.
- Benign IPs (126 total): Activity from these addresses is not currently associated with malicious intent.
Importantly, all identified IPs are “not spoofable,” meaning attackers are not attempting to disguise their origin—a sign of confidence or automation in their approach.
The scans are not limited to a single region. The top source countries for these scanning activities are the U.S., Germany, and the Netherlands, while the top destinations are organizations based in the U.S., Germany, and the U.K. This global footprint underscores the broad appeal of Ivanti systems as a target for cybercriminals.
Ivanti Connect Secure and Pulse Secure VPNs are widely used for enterprise remote access. Their strategic role makes them an attractive target for hackers, particularly as organizations continue to rely on remote work.
While no specific vulnerabilities (CVEs) have been publicly linked to this latest scanning campaign, past incidents show that such reconnaissance is often a harbinger of forthcoming attacks.
History shows that spikes in scanning activity often lead to active exploitation, sometimes before a new vulnerability is even discovered.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
