A critical unauthenticated remote code execution (RCE) vulnerability in HPE Insight Cluster Management Utility (CMU) v8.2 allows attackers to bypass authentication and execute commands as root on high-performance computing (HPC) clusters, researchers revealed today.
Tracked as CVE-2024-13804, the flaw exposes HPC environments to full cluster compromise through weaponized Java client applications.
Technical Breakdown
The vulnerability stems from insecure client-side authorization controls in CMU’s Java Web Start (JNLP) application.
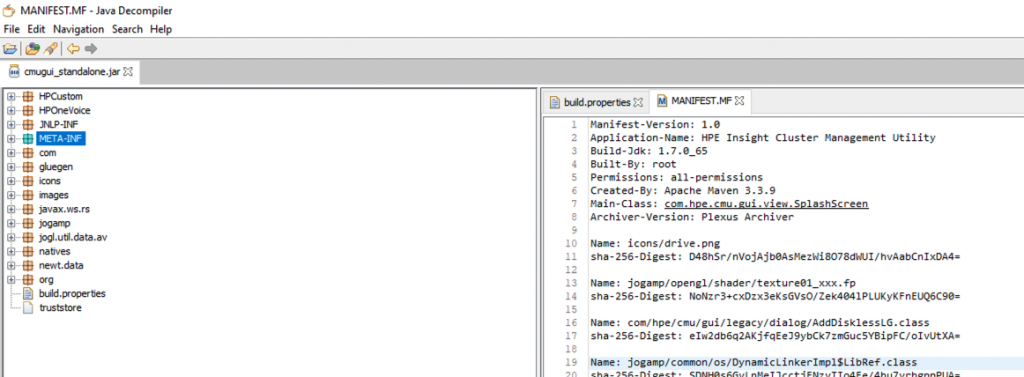
While the GUI client initially restricts administrative functions like cluster provisioning, threat actors can:
1. Decompile Critical JAR Components
Attackers reverse-engineered the cmugui_standalone.jar file using tools like JD-GUI, exposing client-side admin checks in the AdminUserModel.java class.
2. Forge Administrative Privileges
By modifying the isAdmin validation to always return true (shown below), attackers unlock restricted functions:
// Original code
public boolean isUserAdmin() { return this.isAdmin; } // Weaponized version
public boolean isUserAdmin() { return true; } 3. Exploit RMI for Root Commands
The modified client leverages CMU’s Java Remote Method Invocation (RMI) on port 1099 to call the ExecuteCmdLine method, executing OS commands via:
java -jar weaponized_cmugui.jarPoC attacks have demonstrated ifconfig and whoami execution with root privileges on cluster management nodes.
Attack Impact
Successful exploitation enables:


“Client-side authorization checks are security theater without server validation,” warned the researcher who discovered the flaw. “This lets attackers hijack cluster operations as root.”
Mitigation Challenges
HPE confirmed CMU v8.2 reached end-of-life (EOL) in Q4 2024, with no planned patches. Organizations must:
- Network-isolate CMU servers behind firewalls
- Block inbound traffic to port 1099/TCP
- Monitor for suspicious RMI connections
This flaw continues a pattern of RMI-related vulnerabilities in Java-based management tools:
| Year | CVE | Impact |
| 2021 | CVE-2021-44228 | Log4Shell RCE |
| 2023 | CVE-2023-34050 | VMware Aria RCE |
| 2025 | CVE-2024-13804 | HPE CMU Takeover |
HPC operators are urged to accelerate migration to supported cluster managers and audit legacy CMU deployments immediately.
As one enterprise CISO noted: “Critical infrastructure tools hitting EOL without upgrade paths create ticking time bombs.”
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
