Linux, traditionally viewed as a more secure operating system than Windows, has experienced a notable increase in malware attacks. In 2022, Linux malware incidents surged by 50%, significantly increasing and highlighting the critical need for robust analysis and defense mechanisms.
This article explores the importance of Linux malware analysis and presents detailed case studies using ANY.RUN’s advanced malware analysis platform.
ANY.RUN is a cloud-based environment for analyzing Windows malware and Linux-based samples. Malware analysts, SOC, DFIR teams can safely examine threats, simulate different scenarios, and gain insights into malware behavior to improve cybersecurity strategies.
ANY.RUN also allows researchers to understand malware behavior, collect IOCs, and easily map malicious actions to TTPs—all in our interactive sandbox.
The Threat Intelligence Lookup platform helps security researchers find relevant threat data from sandbox tasks of ANY.RUN.
The Rising Threat to Linux Systems
Despite Linux’s reputation for enhanced security, its widespread deployment, especially in server environments, has made it an attractive target for cybercriminals.
The prevalence of DDoS botnets on Linux systems underscores the operating system’s vulnerability to sophisticated attacks.
The escalation of Linux malware presents a pressing challenge for cybersecurity professionals, necessitating comprehensive analysis to understand malware behavior and implement effective countermeasures.
Try ANY.RUN Yourself with a 14-day Free Trial
More than 300,000 analysts use ANY.RUN is a malware analysis sandbox worldwide. Join the community to conduct in-depth investigations into the top threats and collect detailed reports on their behavior..
Importance of Linux Malware Analysis
Analyzing malware samples is pivotal for cybersecurity defenses. Analysts can use detailed examination to identify malware’s operational characteristics, understand its impact on infected systems, and gather indicators of compromise (IOCs).
To protect against Linux-based threats, these tips are essential for setting up Web Application Firewalls (WAF), Security Information and Event Management (SIEM) systems, and Security Orchestration, Automation, and Response (SOAR) platforms.
Case Studies in Malware Analysis with ANY.RUN
ANY.RUN’s interactive malware analysis platform provides a powerful tool for dissecting and understanding Linux malware. The following case studies illustrate the platform’s capabilities in identifying and analyzing different types of Linux malware.
Analyzing Mirai: The Botnet Menace on Linux
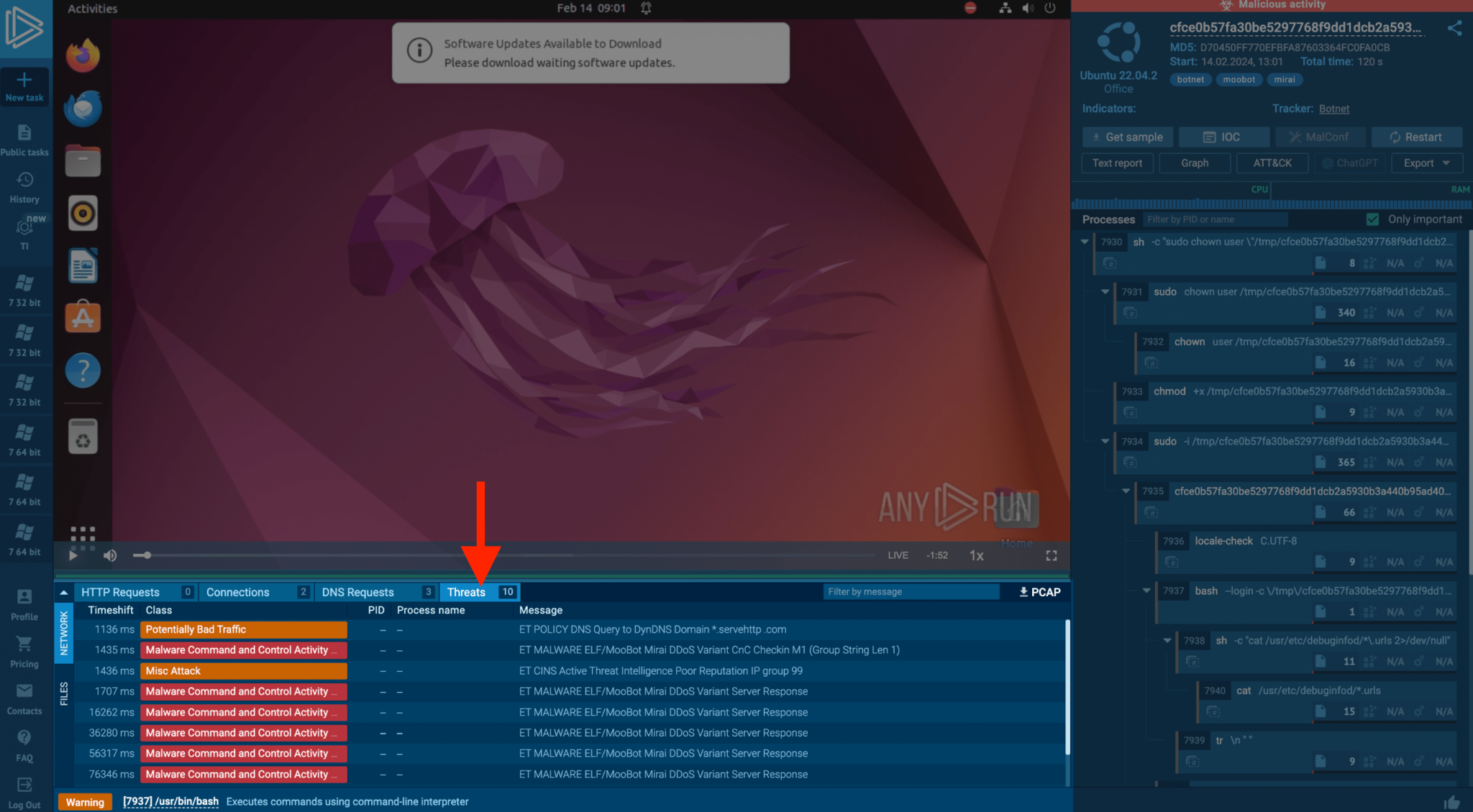
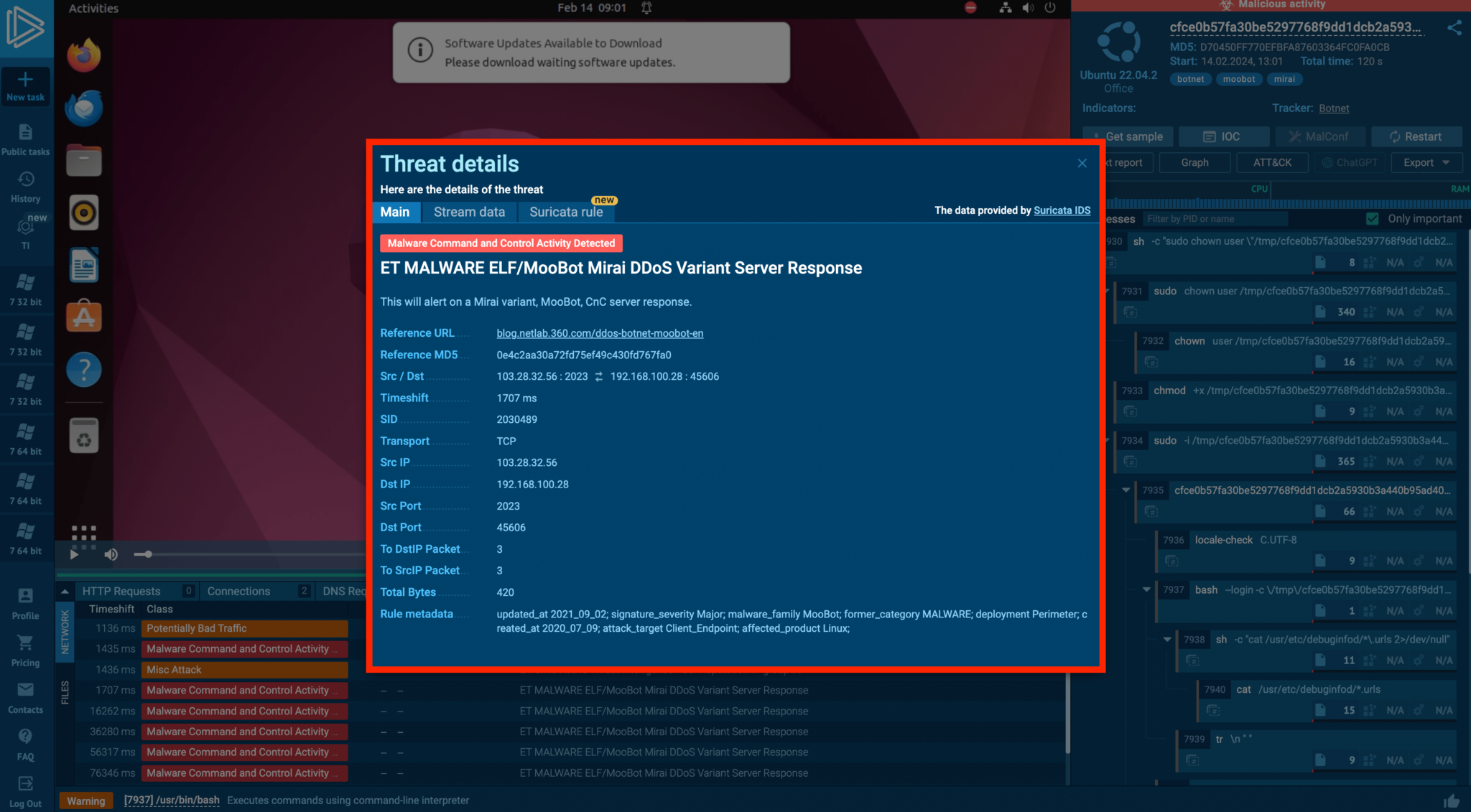
Mirai malware transforms network-connected Linux devices into bots for Distributed Denial of Service (DDoS) attacks. ANY.RUN’s analysis reveals Mirai’s network activities and the triggered Suricata rules, offering insights into the botnet’s behavior and facilitating the collection of IOCs for defensive measures.
If we go to the threats tab in the example, we can see how the botnet is acting in an ANY.RUN task.
Uncovering Linux Miners: Resource Exploitation
Crypto-mining malware exploits system resources to mine cryptocurrency, significantly impairing performance.
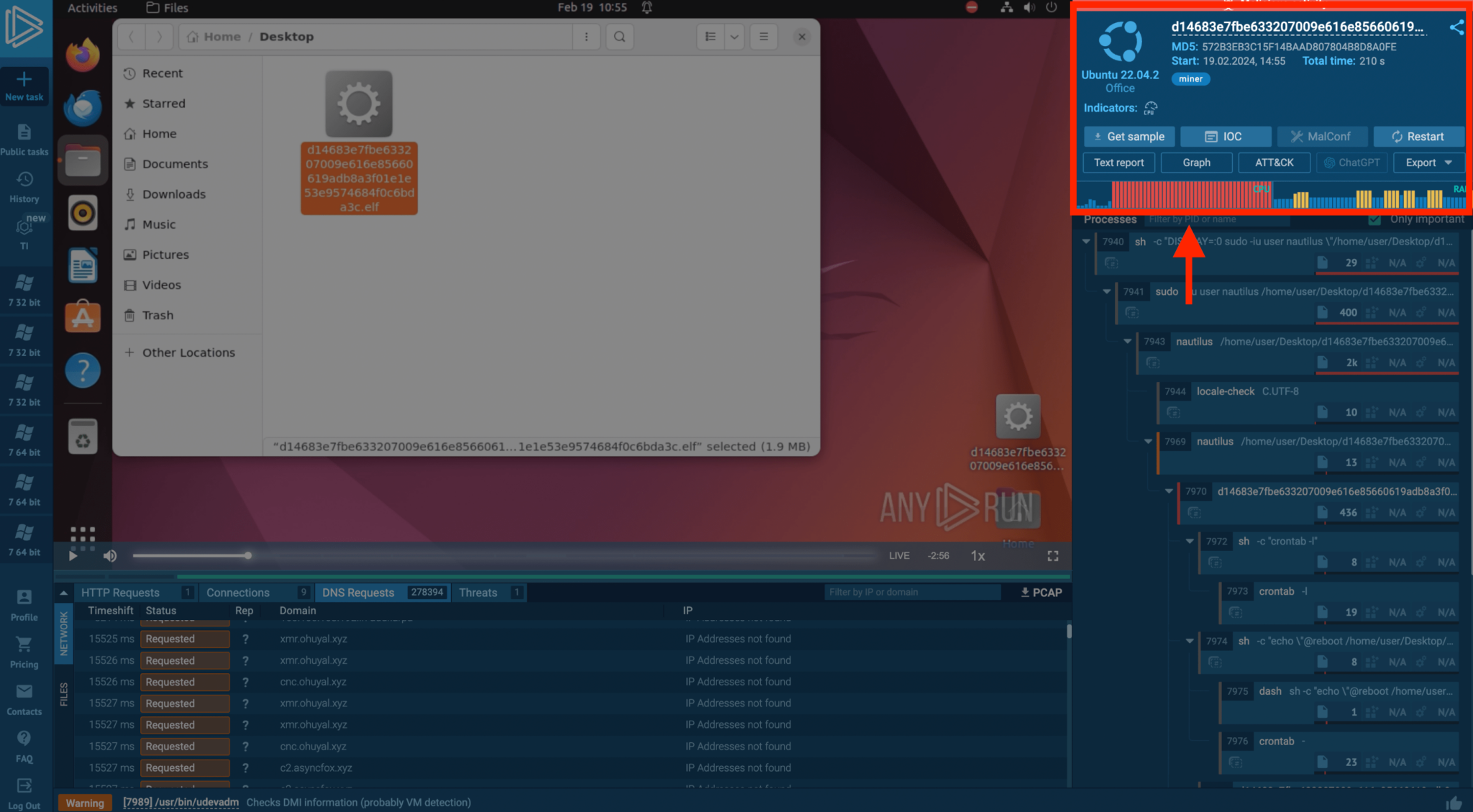
ANY.RUN detected a Linux miner through abnormal network activity and resource consumption, with the CPU and RAM usage spiking post-launch. The analysis also highlighted the miner’s extensive DNS requests, providing a comprehensive view of its network behavior and system data checks.
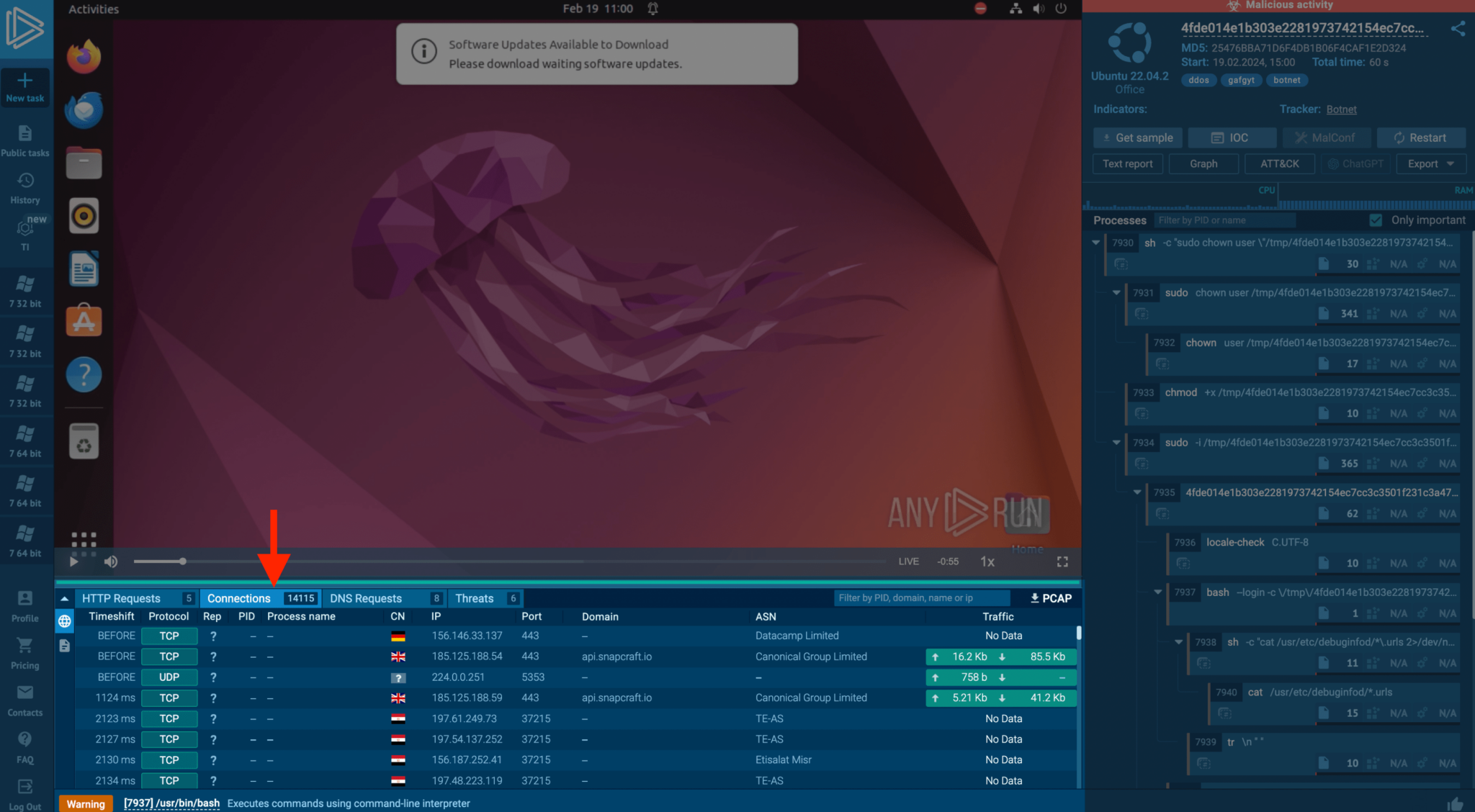
DDoS Attacks on Linux: Operational Tactics
Through this example, ANY.RUN observed a compromised Linux system executing a DDoS attack, attempting to establish over 15,000 connections in a minute.
Identifying such attacks is vital to prevent reputational and regulatory repercussions, especially when targeting critical infrastructure.
The escalation of Linux malware poses a significant threat to digital security. Cybersecurity professionals can improve their defensive strategies, gather priceless IOCs, and gain a deeper understanding of malware behavior through thorough analysis, as ANY.RUN’s case studies show.
As the landscape of cyber threats continues to evolve, the role of advanced malware analysis platforms like ANY.RUN becomes increasingly crucial in safeguarding Linux systems against emerging threats.
As the digital world continues to evolve, the threat of Linux malware grows larger, making the insights and tools provided by ANY.RUN is more essential than ever.
For further information on ANY.RUN’s analysis of crypto-malware and how their platform can assist in combating this threat, you can get access to ANY.RUN sandbox platform for free.
If you’re from the SOC and DFIR teams to investigate incidents and streamline threat analysis. Try all features of ANY.RUN at zero cost for 14 days with a free trial.





