Microsoft has announced the general availability of Copilot for Security threat intelligence embedded experience in the Defender XDR portal.
This AI-powered tool aims to revolutionize the way organizations access, operate on, and integrate Microsoft’s threat intelligence data.
Enhancing Threat Intelligence with Copilot
Microsoft Copilot for Security enables customers to access and utilize Microsoft’s threat intelligence through natural language prompts.
These prompts allow users to ask critical questions about the data and content provided by Microsoft Defender Threat Intelligence (MDTI) and Threat Analytics.
The answers returned are always up-to-date, including information on indicators of compromise (IoCs), intelligence articles, intel profiles, and guidance.
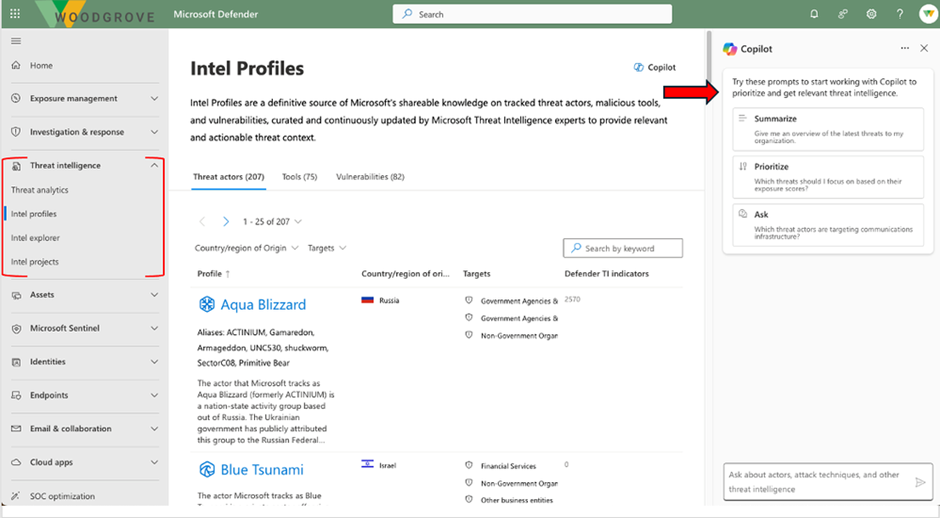
The embedded experience on the right-hand side of the Defender XDR portal has an open prompt bar and a guided experience with three pre-populated prompts.
Scan Your Business Email Inbox to Find Advanced Email Threats - Try AI-Powered Free Threat Scan
The embedded experience, located on the right-hand side of the Defender XDR portal, offers an open prompt bar and a guided experience with three pre-populated prompts.
This feature empowers different security personas to defend against threats at machine speed and scale.
Key Capabilities of the Threat Intelligence Embedded Experience
The Copilot threat intelligence embedded experience in Defender XDR acts as a research assistant, pulling, contextualizing, and summarizing relevant intelligence at machine speed.
Customers can evaluate artifacts and correlate MDTI and Threat Analytics content with other security information from Defender XDR to assess vulnerabilities and understand the scope of an attack.
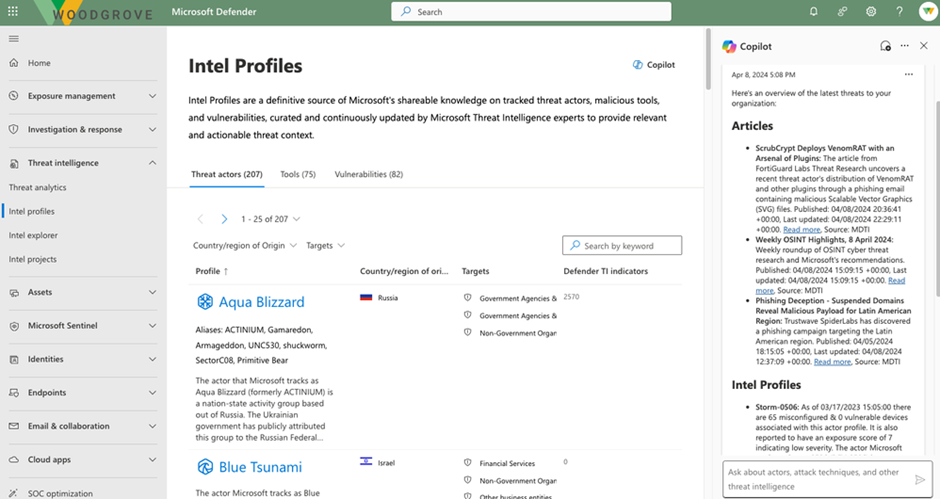
The first pre-populated prompt returns and summarizes intelligence most relevant to your organization.
By clicking on the pre-populated prompt “Give me an overview of the latest threats to my organization,” Copilot returns the latest Intel Profiles and Activity Snapshots, which contain mentions of vulnerabilities, tactics, techniques, and procedures (TTPs) related to the organization’s infrastructure, industry, and region.
Prioritizing Threats and Understanding Risk
Copilot queries Threat Analytics and MDTI to deliver the most relevant intelligence based on an organization’s exposures and vulnerabilities across their attack surface.
By clicking the pre-populated prompt “Which threats should I focus on based on their exposure score,” customers can quickly retrieve information on indicators, such as IP addresses and domains, to enrich artifacts and understand the risk they pose.
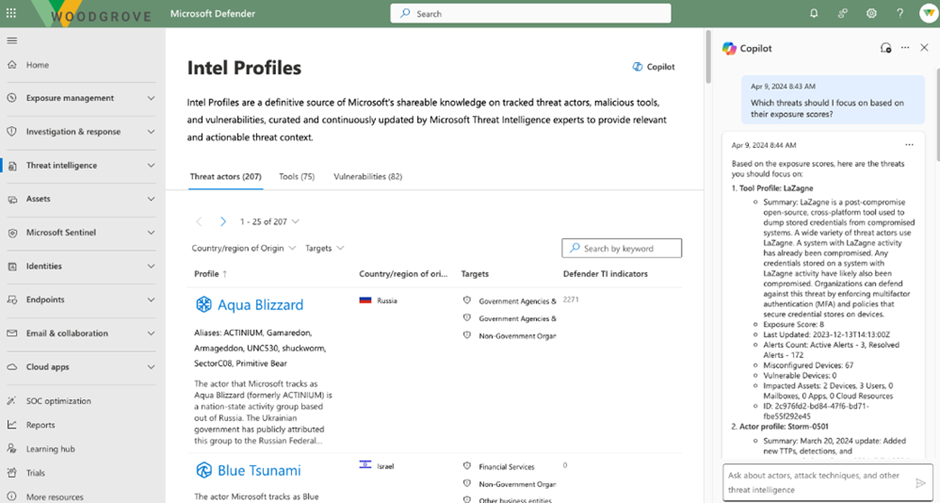
The second pre-populated prompt returns the most critical threat intelligence
Furthermore, Copilot can reason over vulnerability intelligence in MDTI and Threat Analytics to deliver a customized, prioritized list based on a customer’s unique security posture.
By clicking on the pre-populated prompt “Which threat actors are targeting infrastructure in my industry?” Copilot returns summaries of the top threat actors implicated in attacks involving the customer’s industry.
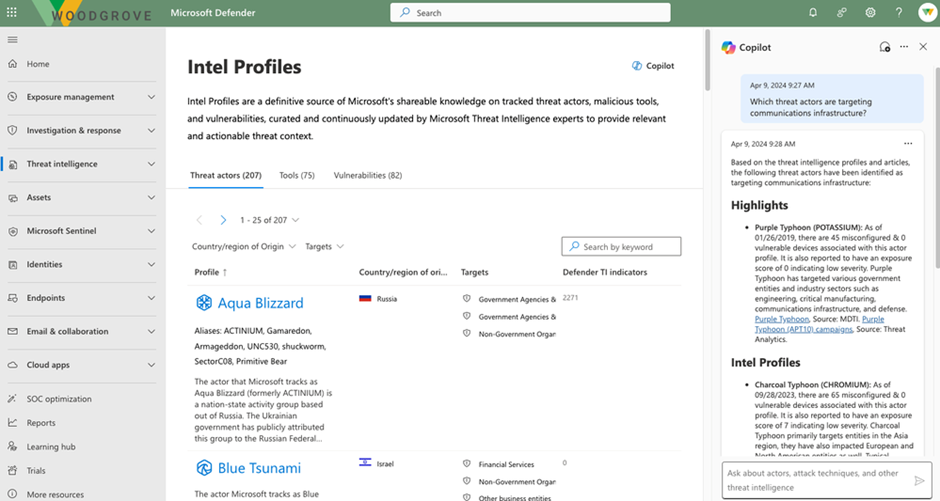
The third pre-populated prompt offers intelligence relevant to your organization based on industry and other factors.
The launch of Copilot for Security threat intelligence in Defender XDR marks a significant step forward in Microsoft’s commitment to providing cutting-edge cybersecurity solutions.
With its AI-driven capabilities and user-friendly interface, Copilot empowers organizations to stay ahead of the ever-evolving threat landscape and protect their critical assets more effectively.
Free Webinar! 3 Security Trends to Maximize MSP Growth -> Register For Free
.webp?w=696&resize=696,0&ssl=1)


.png
)
