Microsoft’s recent attempt to resolve a critical privilege escalation vulnerability has inadvertently introduced a new denial-of-service (DoS) flaw in Windows systems, leaving organizations vulnerable to update failures and potential security risks.
In early April 2025, Microsoft addressed CVE-2025-21204, a security flaw that allowed attackers to abuse symbolic links (symlinks) to elevate privileges via the Windows servicing stack.
The vulnerability centered on the c:\inetpub directory, a default folder for Internet Information Services (IIS). Attackers could exploit misconfigured permissions to create symlinks and gain system-level access.
To resolve this, Microsoft’s April 2025 Windows updates precreated the c:\inetpub folder on all systems, ensuring proper permissions. However, this fix has backfired spectacularly.
The New Flaw: How It Works
Security researcher Kevin Beaumont discovered that Microsoft’s patch introduced a denial-of-service vulnerability in the Windows servicing stack.
Non-administrative users can now create junction points (a type of symlink) within the c:\ drive, disrupting the Windows Update mechanism.
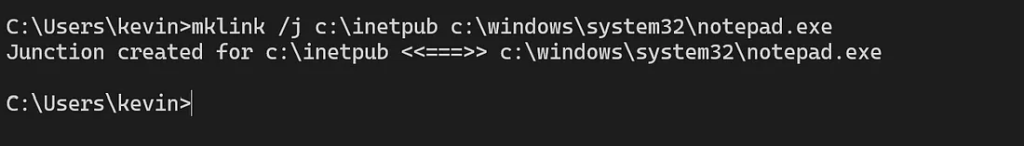
A simple command—executable by any non-admin user via Command Prompt—illustrates the exploit:
mklink /j c:\inetpub c:\windows\system32\notepad.exe This links c:\inetpub to a non-directory file (notepad.exe). Once this junction is created, the Windows servicing stack fails to process updates, causing installations to error out or roll back.
Affected systems cannot install future security patches unless the malicious junction is manually removed.
Implications for Organizations
- Permanent Update Block: Systems with the malicious symlink will remain unpatched indefinitely, exposing them to known exploits.
- Low Barrier to Exploit: Attackers or malicious insiders need only basic user access to trigger the flaw.
- No Official Fix Yet: Microsoft has not acknowledged the issue publicly, despite Beaumont reporting it to the Microsoft Security Response Center (MSRC) two weeks ago.
Microsoft’s Silence and Mitigation Steps
As of April 25, Microsoft has not issued a patch or advisory. Beaumont criticized the lack of communication, noting that the flaw undermines the purpose of the original patch.
- Monitor and restrict user permissions to create symlinks in c:\.
- Use endpoint detection tools to flag unauthorized junction points.
- Manually delete suspicious symlinks in c:\inetpub before installing updates.
This incident highlights the risks of rushed patches in complex systems like Windows.
Symlink-related vulnerabilities have plagued Microsoft for years, and this misstep reinforces the need for rigorous testing of security fixes.
For now, organizations must remain vigilant—ironically, the same updates designed to protect systems could leave them stranded without critical protections.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
