A critical security vulnerability in the Essential Addons for Elementor plugin, installed on over 2 million WordPress websites, has exposed sites to script injection attacks via malicious URL parameters.
The flaw, tracked as CVE-2025-24752 and scoring 7.1 (High) on the CVSS scale, allowed attackers to execute reflected cross-site scripting (XSS) attacks by exploiting insufficient input sanitization in the plugin’s password reset functionality, as per a report by Patchstack.
Vulnerability Overview
The vulnerability stemmed from improper handling of the popup-selector query parameter in the plugin’s JavaScript code.
Attackers could craft URLs containing malicious scripts in this parameter, which were executed when unsuspecting users clicked the link.
This type of reflected XSS attack enables session hijacking, phishing redirects, or malware distribution by exploiting the victim’s browser trust in the compromised website.
The vulnerable code resided in the src/js/view/general.js file:
$(document).ready(function(){
let resetPasswordParams = new URLSearchParams(location.search);
if ( resetPasswordParams.has('popup-selector') && (
resetPasswordParams.has('eael-lostpassword')
|| resetPasswordParams.has('eael-resetpassword')
)) {
let popupSelector = resetPasswordParams.get('popup-selector');
if(popupSelector.length){
popupSelector = popupSelector.replace(/_/g," ");
setTimeout(function(){
jQuery(popupSelector).trigger('click');
}, 300);
}
}
});Here, the popup-selector value was retrieved from the URL and injected into the page without validating or escaping its contents, allowing attackers to insert arbitrary JavaScript code.
For example, a URL like https://victim-site.com/?popup-selector=<script>malicious-code</script> would execute the payload.
Patch and Mitigation
The plugin’s developers, WPDeveloper, released version 6.0.15 to address the flaw by implementing strict input validation.
The patched code restricts popup-selector values to alphanumeric characters and specific safe symbols, neutralizing XSS vectors:
// Patched validation logic
popupSelector = popupSelector.replace(/[^a-zA-Z0-9-_. ]/g, "");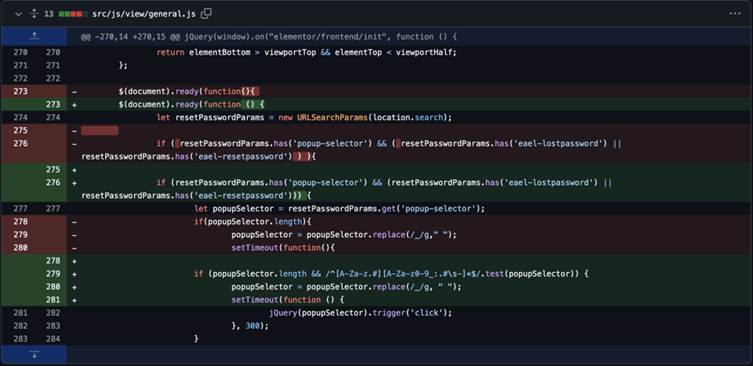
WordPress administrators are urged to immediately update to at least v6.0.15. Those unable to patch should consider disabling the plugin until updates are applied.
This incident underscores persistent risks in WordPress ecosystems, where popular plugins become high-value targets. Essential Addons ranks among Elementor’s most installed extensions, amplifying the flaw’s blast radius.
Sucuri researcher Ben Martin notes, “XSS flaws in plugins with millions of users can enable mass compromise campaigns. Rigorous input sanitization is non-negotiable for plugin developers”.
WordPress users remain advised to enable auto-updates and conduct regular security audits. As of February 2025, no widespread exploits have been reported, but delayed patching could lead to cascading breaches.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
