In early January 2025, a new ransomware strain identified as Contacto surfaced, showcasing advanced techniques designed to bypass conventional security measures.
This analysis provides insights into its operational mechanisms, particularly suited for professionals venturing into ransomware analysis.
Operational Mechanisms
Upon execution, Contacto ransomware employs the GetConsoleWindow() and ShowWindow() functions to retrieve and conceal its command prompt, ensuring stealth during execution.
It establishes a mutex named ContactoMutex to prevent multiple instances of itself from running simultaneously.
To maximize its control over the infected system, Contacto escalates privileges.
It iterates through a predefined list of security privileges such as SeDebugPrivilege and SeTakeOwnershipPrivilege and utilizes the SetPrivileges() function to enable these rights via the AdjustTokenPrivileges API.
This escalation allows the ransomware to manipulate system files and settings effectively.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Encryption Process
Contacto employs an innovative threading model that enhances the efficiency of file encryption.
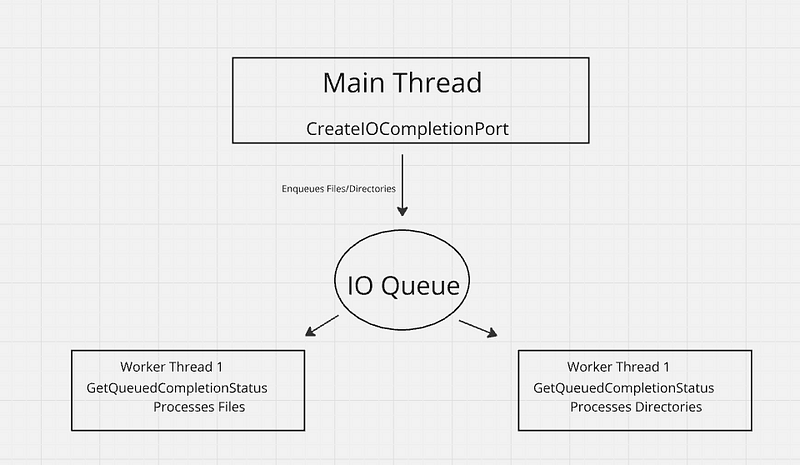
By determining the number of available processors, the system creates double the number of threads, which facilitates a streamlined workflow.
Each thread is tasked with executing a worker function dedicated to file access.
This design ensures sequential access and modification rights through meticulous error handling, thereby minimizing the risk of disruptions and optimizing resource utilization.
The encryption process begins with dynamic key generation, where Contacto produces two cryptographic keys: a primary key (32 bytes) and a secondary key (8 bytes).
These keys are generated using a hybrid random number generator, ensuring a strong foundation of randomness.
To further bolster security, the keys undergo hashing through iterative SHA-256 rounds, which guarantees that each file is encrypted with a unique key combination.
According to the research, this approach significantly enhances the security of the encryption process, making it resilient against potential decryption attempts.
In addition to its threading and key generation strategies, Contacto utilizes a chunk-based encryption method.
Rather than encrypting entire files, the system focuses on specific segments, such as headers and footers, utilizing adaptive chunk sizes tailored to the performance capabilities of the system and the size of the files.
This targeted approach not only speeds up the encryption process but also helps maintain a degree of file integrity, rendering recovery efforts more complex and challenging for unauthorized users.
By optimizing performance while safeguarding the content, Contacto effectively balances security and efficiency in its encryption procedures.
The ransomware’s final acts include modifying system configurations, such as disabling Windows Defender through registry manipulation and deleting backup copies to hinder recovery attempts.

Additionally, it implements a visual alteration of the victim’s desktop by changing the wallpaper to display a ransom note.
The Contacto ransomware represents a sophisticated threat, employing advanced techniques for system infiltration, data encryption, and stealth operations, making it a critical subject for ongoing cybersecurity vigilance and analysis.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
