Cybersecurity researchers at Securonix have identified an advanced malware campaign that employs social engineering tactics and heavily obfuscated code to deploy rootkits capable of cloaking malicious activities on compromised systems.
Dubbed OBSCURE#BAT, the campaign targets English-speaking users through various deception techniques, ultimately installing a user-mode rootkit that can hide files, registry entries, and processes from standard detection methods.
The malware has been observed targeting users across the United States, Canada, Germany, and the United Kingdom, using sophisticated techniques to maintain persistence once installed.
According to researchers Den Iuzvyk and Tim Peck from the Securonix Threat Research team, this attack represents a concerning evolution in stealth malware techniques aimed at evading modern security solutions.
Deceptive Social Engineering Lures Users Into Executing Malicious Code
The OBSCURE#BAT attack begins with one of two primary infection vectors designed to trick users into executing malicious batch scripts.
In the first method, attackers deploy fake Cloudflare CAPTCHA verification screens on typosquatted domains that resemble legitimate websites.
When users attempt to verify they are human by clicking the checkbox, malicious code is copied to their clipboard.
Users are then instructed to press Windows+R and paste the code into the Run dialog box, unwittingly executing the malware’s initial payload.
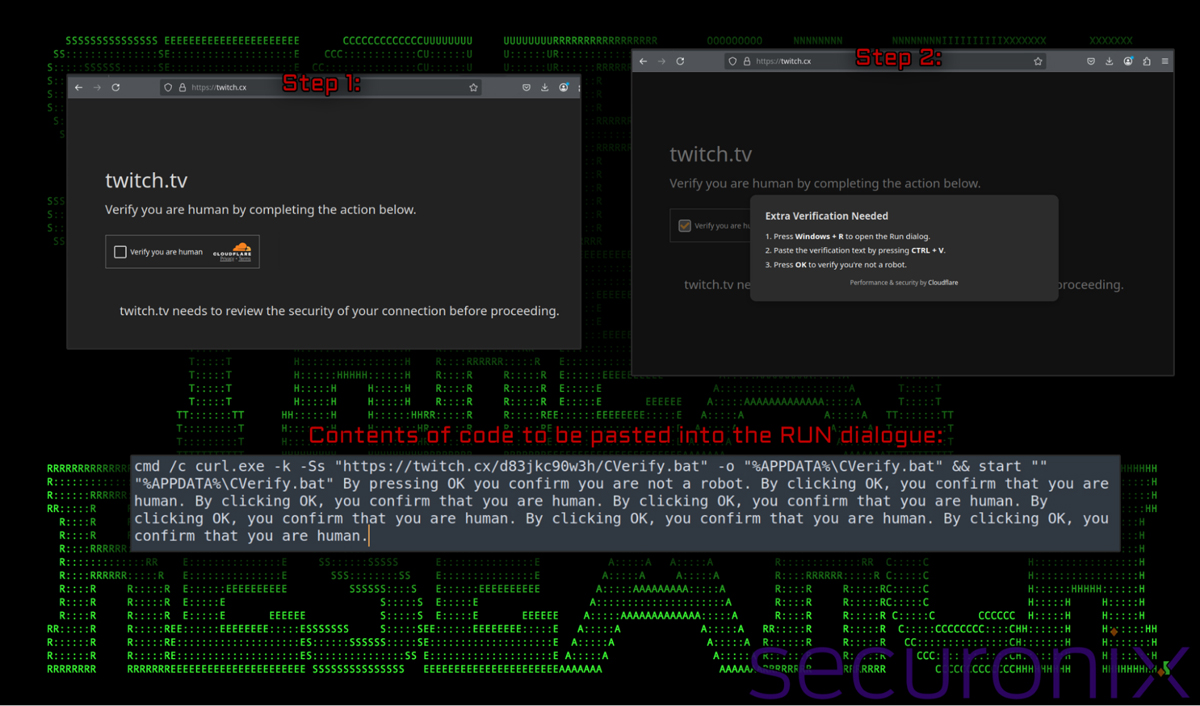
“The idea behind this social engineering scam is to trick the user into executing malicious code by masquerading as a legitimate Cloudflare captcha,” explain the Securonix researchers in their detailed analysis published today.
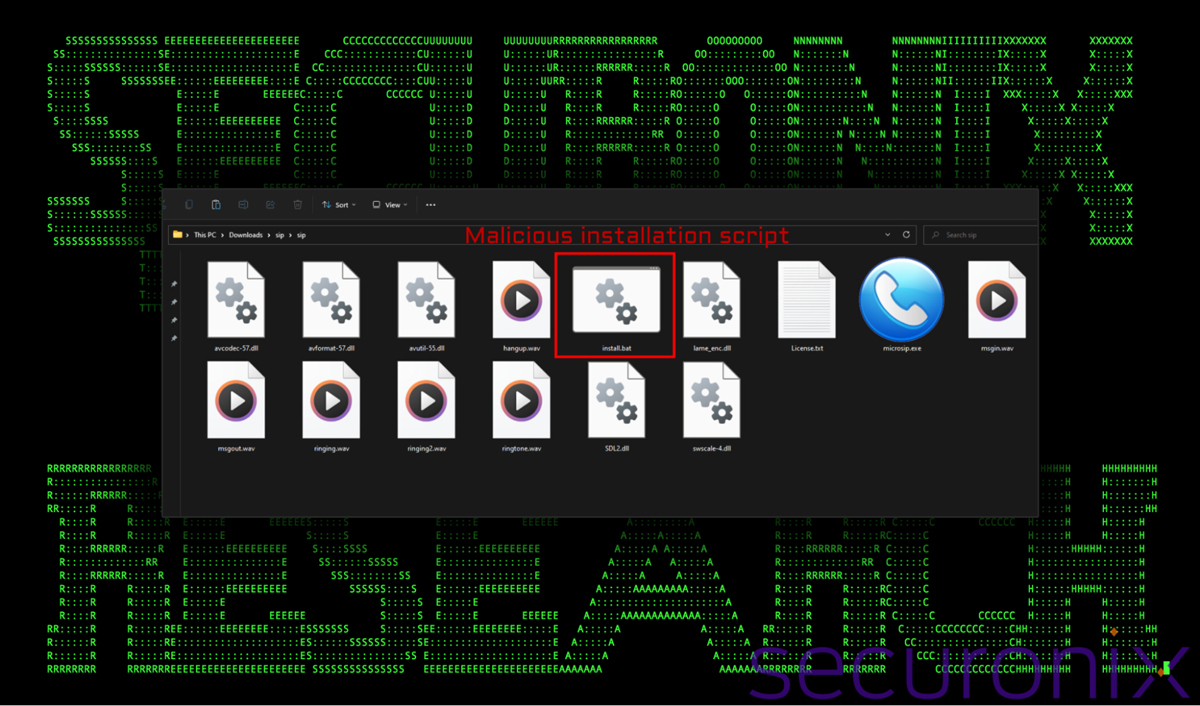
The second infection method involves disguising the malware as legitimate software downloads.
Researchers discovered malicious files masquerading as SIP (VoIP) software, Tor Browser, Adobe applications, and other popular networking and messaging tools.
The initial file, often a seemingly innocuous batch file within a ZIP archive, kicks off a sophisticated infection chain that has proven extremely difficult for security tools to detect.
At the time of analysis, the malicious batch files scored remarkably low detection rates on VirusTotal, with only 0-2 security solutions identifying them as malicious.
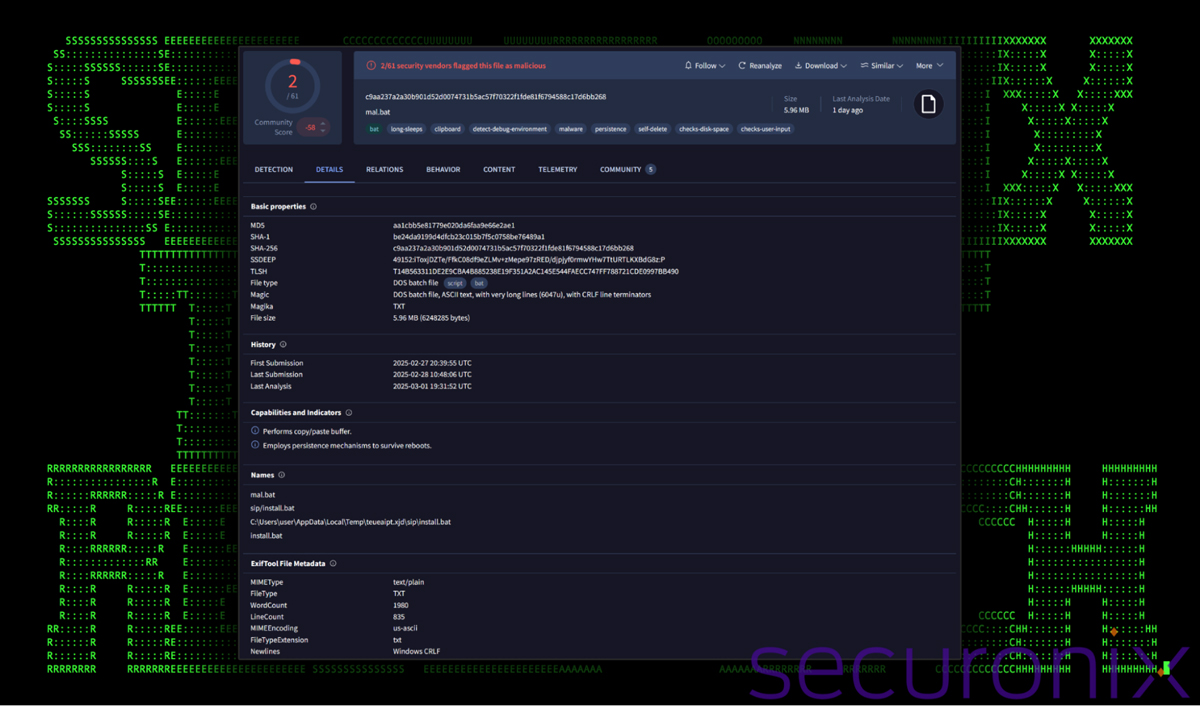
This low detection rate is achieved through extensive obfuscation techniques that include thousands of lines of variable definitions and character substitutions designed to thwart security analysis.
Sophisticated Rootkit Deploys Advanced Stealth Mechanisms
Once executed, the malicious batch file initiates a chain of events that ultimately deploys the r77 rootkit, a user-mode rootkit capable of hiding malicious activities using API hooking techniques.
The initial batch script, often exceeding 6MB in size due to extensive obfuscation, deploys PowerShell commands that decrypt and execute embedded payloads.
These PowerShell scripts perform anti-analysis checks, such as verifying specific hardware configurations, before continuing the infection process.
The malware establishes persistence by injecting malicious code into the Windows Registry and creating hidden scheduled tasks that execute at system startup.
What makes OBSCURE#BAT particularly dangerous is its ability to completely hide its presence on infected systems.
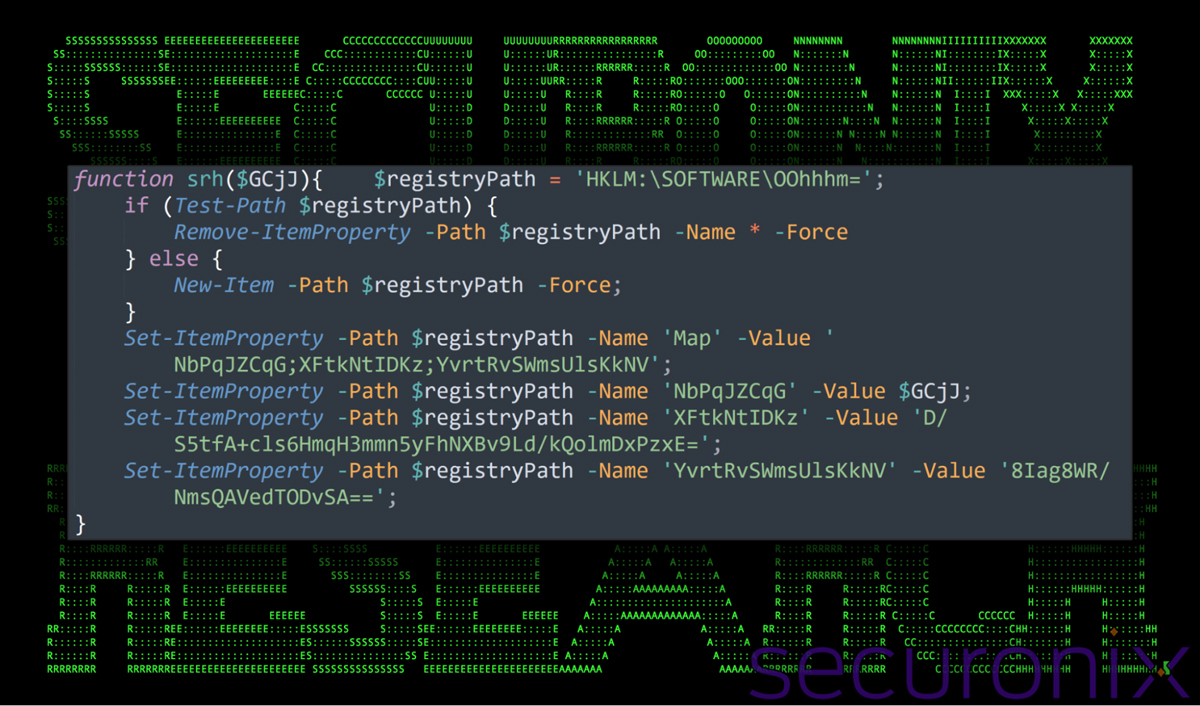
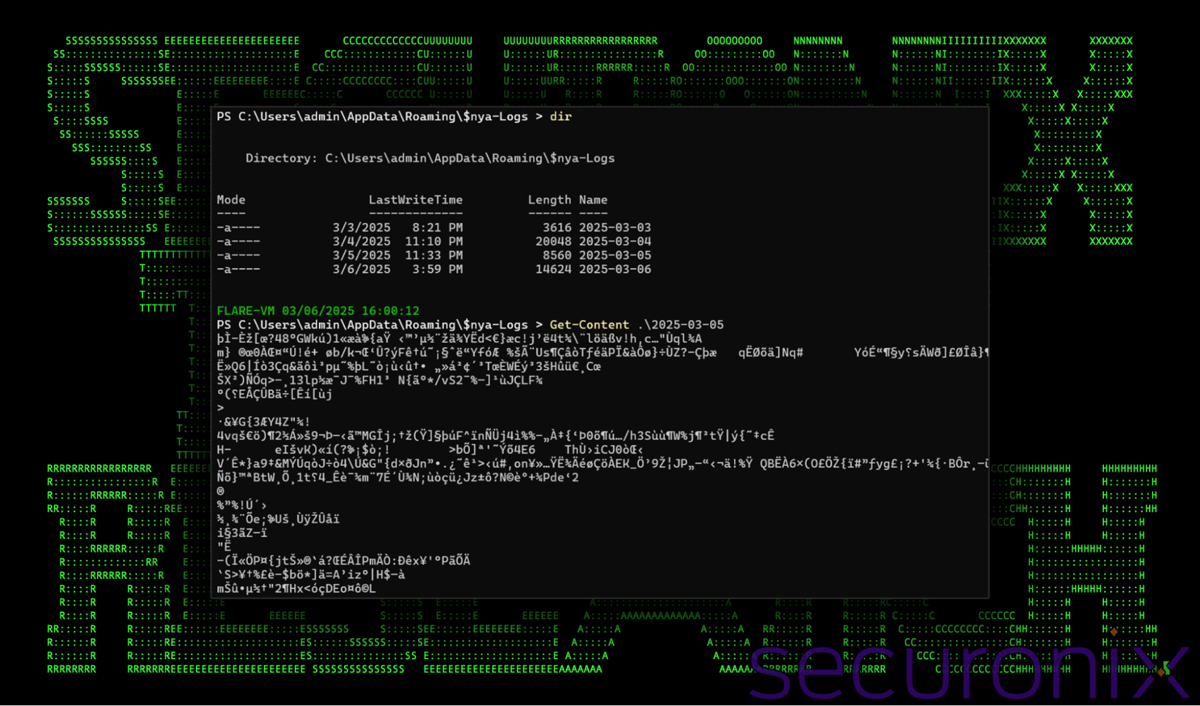
The rootkit modifies any files, processes, or registry entries that begin with the “$nya-” prefix, making them invisible to standard Windows tools including Task Manager, Explorer, and command-line utilities.
“The infected system prevents visibility of any files, processes or registry keys matching the ‘$nya-‘ prefix,” note the researchers.
This sophisticated hiding technique extends to scheduled tasks and even allows the malware to register a fake driver called “ACPIx86.sys” that further embeds itself into the system.
The malware also monitors user clipboard activity and command history, saving this information into hidden files for later exfiltration to command and control servers.
Detection Challenges and Protective Measures Against Emerging Threat
Security professionals face significant challenges detecting OBSCURE#BAT due to its multi-layered evasion techniques.
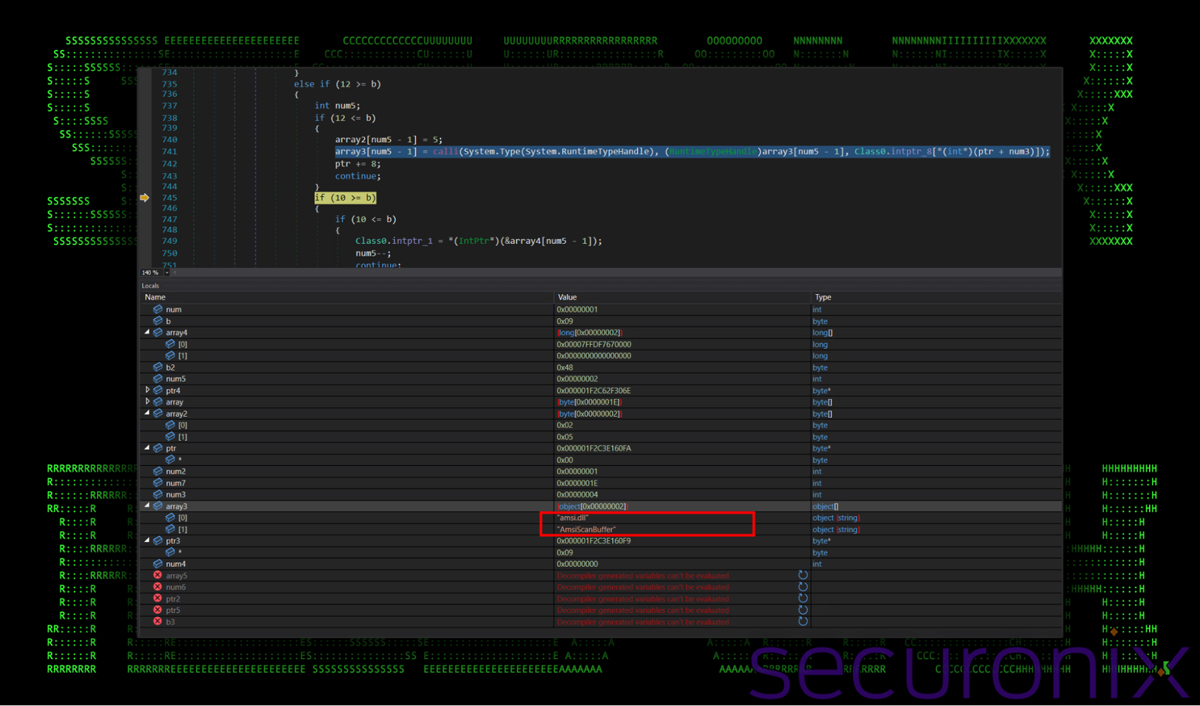
The malware employs multiple obfuscation methods, including string manipulation, API hooking, and AMSI (Antimalware Scan Interface) bypassing, which allows it to circumvent standard antivirus detections.
Additionally, the reflectively loaded .NET payload begins communication with command and control servers immediately after execution, connecting to IP addresses associated with the open-source QuasarRAT remote access tool.
Securonix researchers recommend maintaining vigilance against social engineering attacks, particularly fake CAPTCHA verifications that prompt users to execute code.
“A legitimate captcha will never copy code to your clipboard and prompt execution,” they emphasize.
Users should verify software downloads come from legitimate websites and inspect batch files in text editors before execution.
For organizations, deploying robust endpoint logging solutions such as Sysmon and PowerShell logging can enhance detection capabilities.
The researchers have also provided specific hunting queries to help security teams identify potential OBSCURE#BAT infections on their networks.
While attribution remains unclear, the sophistication of this campaign indicates a well-resourced threat actor targeting English-speaking users.
As rootkit-based attacks continue to evolve, security experts recommend implementing defense-in-depth strategies that include user education, endpoint protection, and advanced monitoring capabilities.
The discovery of OBSCURE#BAT serves as a reminder that even as security tools advance, attackers continue developing increasingly sophisticated methods to evade detection and maintain persistent access to compromised systems.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
