A sophisticated malware campaign has compromised over 1,500 PostgreSQL servers, leveraging fileless techniques to deploy cryptomining payloads.
The attack, identified by Wiz Threat Research and attributed to the threat actor group JINX-0126, exploits publicly exposed PostgreSQL instances configured with weak or default credentials.
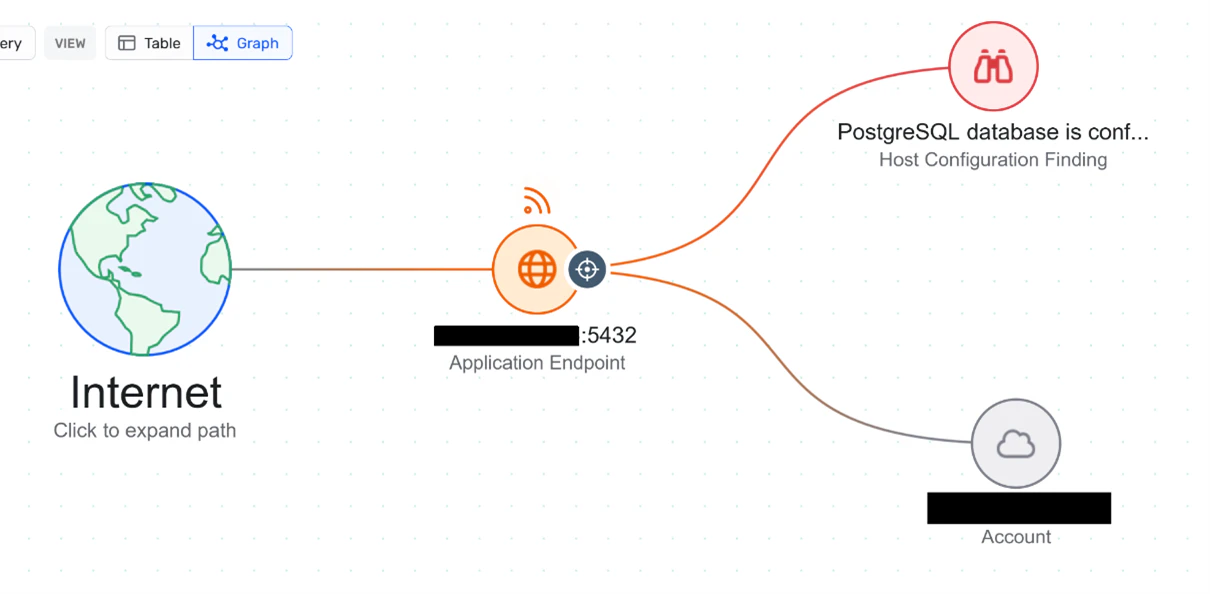
The attackers utilize these vulnerabilities to execute XMRig-C3 cryptominers without leaving detectable files on the system.
Fileless Payloads Evade Detection
The campaign demonstrates advanced evasion tactics, including the deployment of binaries with unique hashes for each target and fileless execution of the miner payload.
These measures are designed to bypass traditional security solutions that rely on file hash reputation for detection.
The attackers also assign unique mining worker IDs to each compromised server, further complicating detection efforts.

Analysis of the campaign revealed that the attackers abuse PostgreSQL’s COPY ... FROM PROGRAM function to drop and execute malicious payloads.
Upon gaining access, they perform system discovery commands such as whoami and uname, followed by deploying a dropper script that eliminates competing cryptominers and installs their own malware.
Technical Details of the Attack
The malware includes a binary named “postmaster,” which mimics legitimate PostgreSQL processes to avoid suspicion.
This binary is packed with obfuscation techniques and encrypted configurations, ensuring its persistence on infected systems.
It creates cron jobs for regular execution and modifies PostgreSQL configuration files to block external access while maintaining communication with internal networks.
Additionally, a secondary binary named “cpu_hu” is deployed to execute cryptomining operations.
This binary operates filelessly via memory-based execution, further reducing its footprint on the compromised systems.
Both binaries are tailored per victim, with unique configurations embedded in their code to ensure operational efficiency and evade detection.
Widespread Impact Across Cloud Environments
The campaign highlights the widespread vulnerability of cloud-hosted PostgreSQL instances.
Wiz’s research indicates that nearly 90% of cloud environments host PostgreSQL databases, with approximately one-third of these being publicly exposed.
This misconfiguration provides an easy entry point for opportunistic attackers like JINX-0126.
By analyzing wallets associated with the campaign on C3Pool, researchers estimated that each wallet had approximately 550 active mining workers, confirming the scale of the attack across more than 1,500 servers globally.
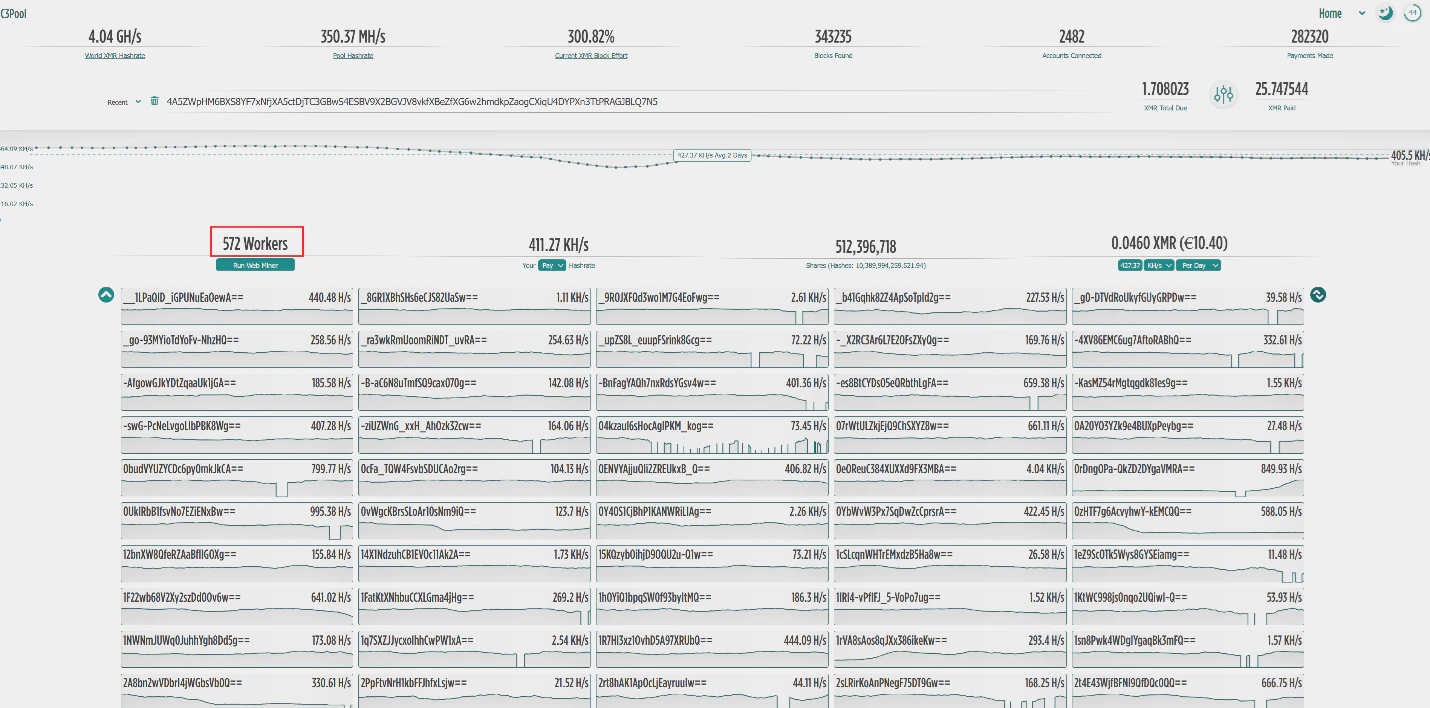
According to the Report, To counter such threats, organizations must ensure robust security configurations for their PostgreSQL instances, including disabling public exposure and enforcing strong authentication mechanisms.
Tools like Wiz Dynamic Scanner can identify exposed instances and detect weak credentials within cloud environments.
Additionally, runtime sensors can monitor for suspicious activities indicative of such attacks, from initial exploitation to fileless cryptomining operations.
This incident underscores the critical need for proactive database security measures in cloud environments to prevent exploitation by increasingly sophisticated threat actors.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
.webp?w=696&resize=696,0&ssl=1)


.png
)
