Cybersecurity experts have raised alarms about the Rhadamanthys Infostealer, a sophisticated malware now being distributed through Microsoft Management Console (MMC) files with the MSC extension.
This new tactic, confirmed by the AhnLab Security Intelligence Center (ASEC), exploits the flexibility of MSC files, which are XML-based and capable of executing scripts, commands, and programs.
The malware’s innovative use of MMC highlights the growing threat posed by attackers leveraging legitimate tools for malicious purposes.
Two Methods of Exploitation
The Rhadamanthys Infostealer employs two distinct methods to spread via MSC files:
- Exploiting apds.dll Vulnerability (CVE-2024-43572):
This method involves exploiting a vulnerability in the apds.dll file. Specifically, attackers use the resource named “redirect.html” within apds.dll to execute malicious code.
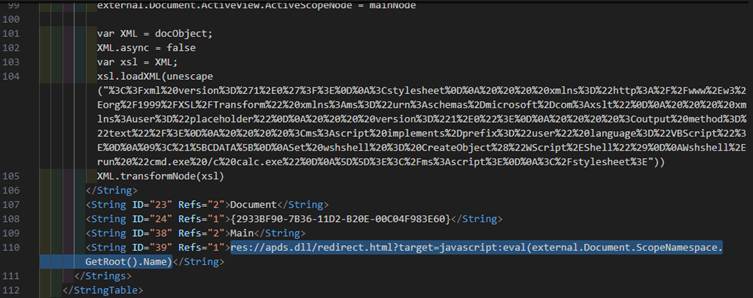
By embedding a specific syntax (res://apds.dll/redirect.html?target=javascript:eval(…)) in the MSC file, the malware accesses and executes code directly within the vulnerable DLL.
This approach bypasses MMC and allows attackers to execute arbitrary commands. However, this vulnerability has been patched, reducing its current effectiveness.
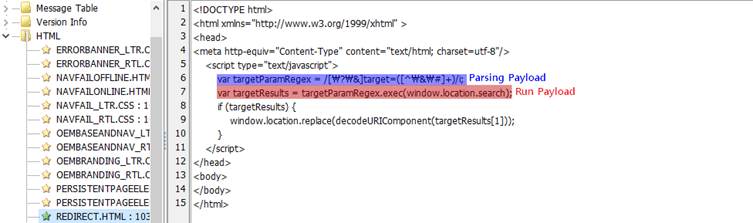
- Using Console Taskpad:
The second method leverages MMC’s Console Taskpad feature, which interprets and executes commands embedded between <ConsoleTaskpads> tags in an MSC file.
Unlike the DLL exploitation method, this technique does not rely on vulnerabilities but instead uses MMC’s legitimate task execution capabilities.
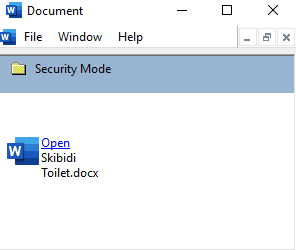
Attackers disguise malicious MSC files as seemingly harmless documents, such as MS Word files.
When opened, these files trigger a PowerShell script download from an external source, which subsequently executes the Rhadamanthys Infostealer.
Although patches have mitigated some vulnerabilities like CVE-2024-43572, the continued use of Console Taskpad for malware distribution underscores the need for vigilance. To protect against such threats:
- Avoid opening MSC files from unknown or untrusted sources.
- Ensure that all software is updated with the latest security patches.
- Use robust antivirus solutions capable of detecting unconventional attack vectors.
- Educate users about phishing tactics and suspicious file formats.
The rise in MSC-based malware campaigns highlights how attackers adapt their methods to exploit overlooked tools like MMC.
As cybercriminals continue refining their techniques, organizations must remain proactive in securing their systems against evolving threats like Rhadamanthys Infostealer.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



