Bug bounty programs have emerged as a critical avenue for researchers to identify vulnerabilities in digital platforms.
One such success story involves a recent discovery made within the Red Bull bug bounty program, where a security researcher utilized ChatGPT to craft a domain monitoring script that ultimately led to the identification of a significant Amazon S3 bucket takeover vulnerability.
Setting Up Domain Monitoring
The Red Bull bug bounty program provides a comprehensive scope for vulnerability assessments, specifying domains that participants are encouraged to test.
Understanding the dynamic nature of these programs, the researcher recognized the need for a proactive approach—hence, the development of a domain monitoring script.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
“To streamline my efforts, I enlisted the help of ChatGPT to create this script,” the researcher explained. “It was crucial to track any changes in the bug bounty scope in real-time.”
The script, elegantly crafted in Python, employed the Telegram API to send notifications whenever there were updates regarding the domains in scope.
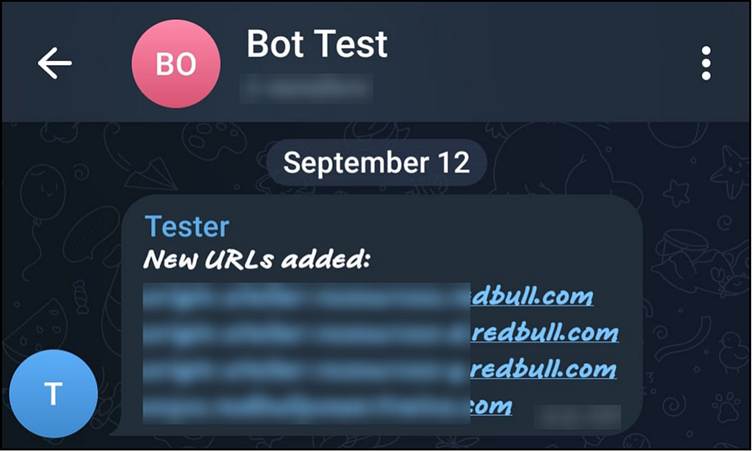
It continuously monitored a public repository for any changes in the bug bounty’s specified domains, sending alerts for new additions or deletions every minute.
By leveraging automation, the researcher ensured they would never miss an update, keeping their finger on the pulse of the bug bounty landscape.
Just a day later, the tracking script sent a notification about a new domain added to the scope. The researcher immediately recognized this as an opportunity to delve deeper into the newly introduced subdomain.
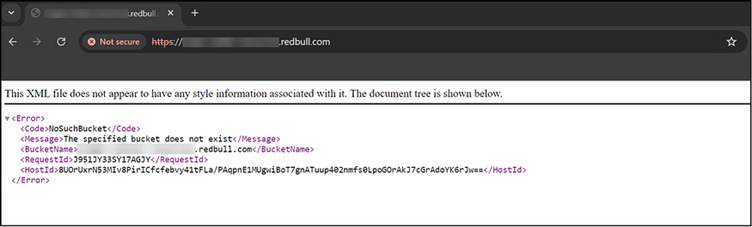
As per a report published by InfoSec, upon investigation, they discovered a misconfigured Amazon S3 bucket associated with the new domain. This misconfiguration presented a potential risk that warranted further examination.
Misconfigured Amazon S3 Bucket
The researcher conducted a series of tests to determine the security posture of the S3 bucket. Utilizing tools such as awscli, they began enumerating the bucket’s permissions.
To their astonishment, they found that the bucket had public write permissions enabled.“This was a classic case of an S3 bucket misconfiguration,” the researcher noted.
“With public write access, I realized I could upload arbitrary files to the bucket, potentially allowing for a complete takeover.”
Exploitation: The S3 Bucket Takeover
To confirm the vulnerability, the researcher followed a straightforward process:
- Enumerating S3 Buckets: They used command-line tools to investigate the bucket permissions.
- Testing for Vulnerability: Verification revealed that the bucket permitted public uploads.
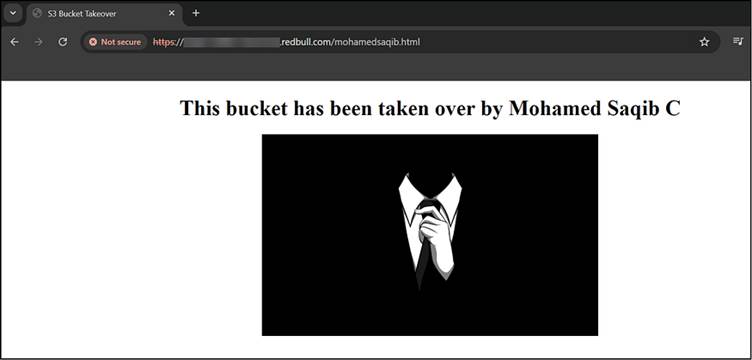
- Confirming Takeover: By uploading a simple HTML file, the researcher successfully demonstrated that the bucket could be taken over.
Upon accessing the hosted file, it was clear that the bucket had been fully compromised.
Recognizing the importance of responsible disclosure, the researcher promptly reported the vulnerability to Red Bull’s security team. The response was positive and swift, with the company appreciating the diligence displayed in their findings.
In a delightful twist, the researcher was rewarded with three trays of Red Bull as a token of gratitude. “It’s not every day you get rewarded with such a fitting prize for your hard work,” the researcher quipped.
This experience underscores the significance of staying vigilant about monitoring changes in bug bounty programs and demonstrates the potential pitfalls that may lie within minor misconfigurations.
The successful automation of the monitoring process, facilitated by ChatGPT, not only streamlined the discovery phase but also highlighted the powerful intersection of technology and security research.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



