Researchers uncovered a new malicious Android app from the Google play store that disguised as a Photo Beautification App steal the SMS verification code and activate the Wireless Application Protocol (WAP) billing.
Since earlier this year, Google made various changes in permission requests for the app for restricting access to the call, and SMS permission and other access are required to ask permission from users to access the app.
These restrictions prevent malicious apps from dropping malware, steal data, personal information, illegally request permission, and minimize the threat vectors.
However, Threat actors always finding new ways to bypass security features by deploying the various tactics and techniques to target the millions of users around the world.
In recent research discovered in Play store names as “Yellow Camera” that posed as poses as a camera and photo beautification or editing app embedded with a routine process that reads SMS verification codes from the System Notifications.
The app downloaded more than 10,000 times, and also user wrote a review that he lost his phone credits after installing this app “The app doesn’t deserve any star rating”.

The app mainly targeting South Asian countries such as Thailand, Malaysia, and some of the Chinese speaking users, but it’s not limited and they keep on expanding the targets Region.
Also Read: Gustuff Android Banking Malware Uses SMS Messages to Hack Users Device
Activate a Wireless Application Protocol (WAP) Billing
The main motivation of this malicious app to activate a WAP billing by reading the system notification. WAP-billing services are widely used as an alternative payment method for users to buy content from WAP-enabled sites.
These WAP billing services charge directly to the user’s phone bill or credits without having to register for services, use credit or debit cards, and this is very convenient for fraudsters.
Once the app installed on the targeted device, it asks for permission to access the notification feature and download the file from (hxxp://new-bucket3ee91e7f[-]yellowcamera[.]s3[-]ap[-]southeast[-]1[.]amazonaws[.]com) that contains the JS payload and address for WAP subscription.
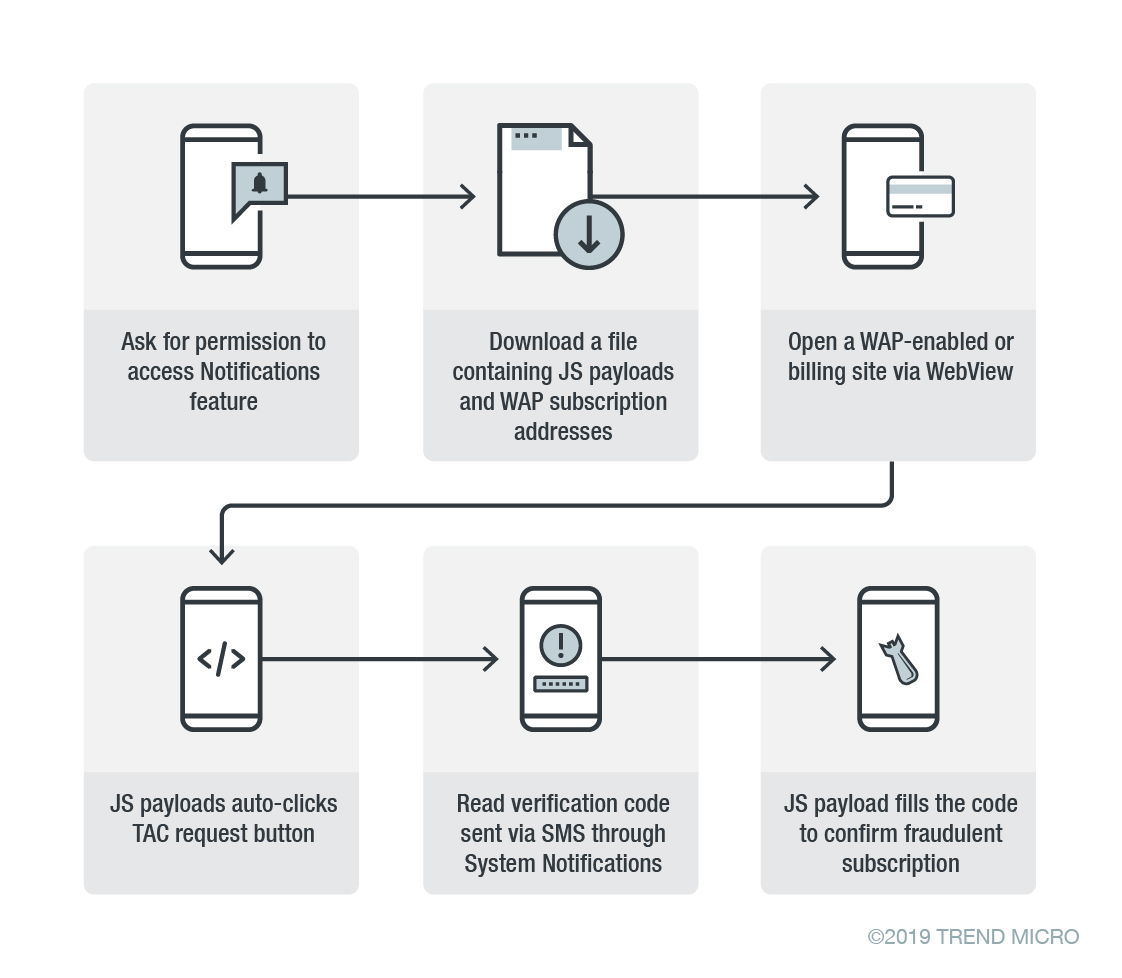
Later it accesses the webview to open a WAP-enabled or billing site JS payloads auto-clicks Type Allocation Code (TAC) requests — codes used to uniquely identify wireless devices.
Finally, once the code received, the malicious read the verification code sent via SMS through the system notifications, and the Javascript code fills the received code and confirms the fraudulent subscription.
According to Trend Micro research” or persistence, the malicious app uses the startForeground API to put the service in a foreground state, where the system considers it to be something the user is actively aware of and thus would not be terminated even if the device is low on memory. “
Trend Micro Mobile Threat Research Team also found other apps that posed as photo filtering or beautifying apps that performing the same routine of fraudulently subscribing the device to a WAP service.
Trend Micro reported these apps to Google. and the app, along with similar ones is no longer in the Play store.
You can refer to the Indicator of compromise here.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.



.png
)
