Cybersecurity researchers have uncovered a sophisticated Android malware campaign known as “Tria Stealer,” which is targeting users in Malaysia and Brunei to collect sensitive information such as SMS data, call logs, WhatsApp messages, and emails.
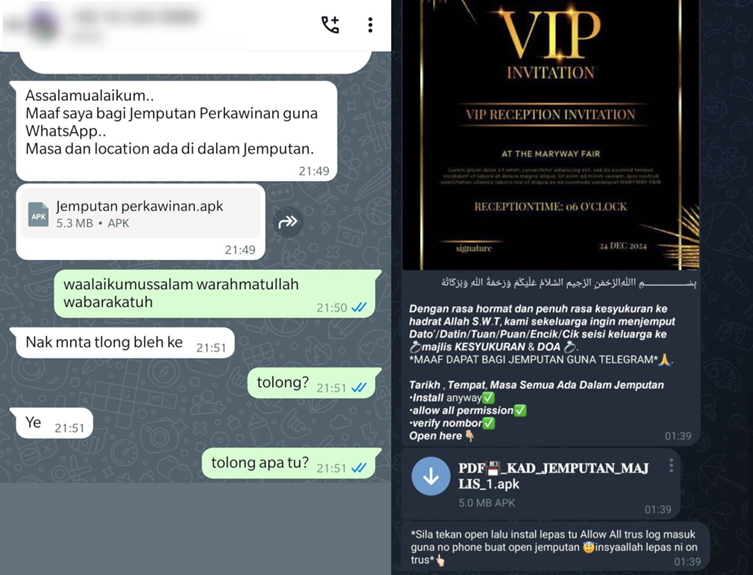
The malware campaign, which has been active since March 2024, uses wedding invitations as a lure to trick victims into downloading malicious apps.
This campaign showcases the growing sophistication of Android threats, as well as the potential risks of data breaches and account hijacking.
How Tria Stealer Operates
The Tria Stealer malware disguises itself as a legitimate Android app, often themed around wedding invitations. Victims are tricked into installing the app by receiving messages via WhatsApp or Telegram, often sent by compromised accounts.
Once downloaded and installed, the app requests dangerous permissions, such as access to SMS, call logs, and network state. It also masquerades as a system settings app to avoid suspicion.
Upon installation, Tria Stealer collects sensitive information, including SMS messages, call logs, device details, and even messages from apps like WhatsApp and Gmail.
This data is then exfiltrated to the attackers through Telegram bots, which act as Command and Control (C2) servers.
The researchers identified two versions of Tria Stealer, with the second version, released in August 2024, introducing advanced features.
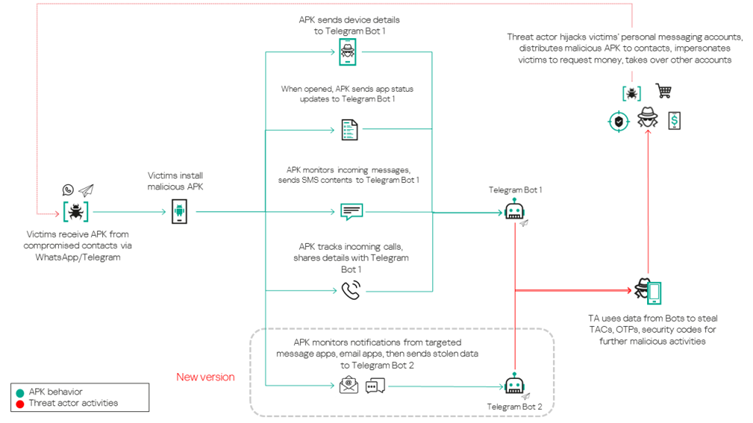
The malware utilizes the BroadcastReceiver function to monitor incoming messages and calls, enabling it to intercept critical information like one-time passwords (OTPs) and transaction authorization codes (TACs).
These codes are then used to hijack accounts on platforms such as WhatsApp, Telegram, and banking applications.
Additionally, newer variants of the malware include functionality for stealing data from notifications posted by popular messaging and email apps, including Gmail, WhatsApp Business, and Yahoo Mail.
The stolen data is repackaged into specific formats and sent to different Telegram bots based on its type, showcasing an organized approach by the threat actors.
Consequences of the Attack
Once Tria Stealer compromises accounts, it serves two primary purposes:
- Distribution of Malware: The malware sends the malicious app link to the victim’s contacts via group chats and direct messages, tricking more users into downloading it and perpetuating the infection.
- Financial Fraud: Impersonating the account owner, attackers request money transfers from the victim’s contacts, often resulting in financial losses.
Experts warn that the stolen information could also be used for other nefarious purposes, such as resetting account passwords, accessing online banking systems, or compromising additional platforms reliant on SMS or email authentication.
Suspected Origin and Target Victims
Investigations suggest that the campaign is orchestrated by an Indonesian-speaking threat actor, evidenced by embedded Indonesian language strings and naming patterns in the malware.
While no individual targeting has been observed, the majority of victims are in Malaysia and Brunei, with Malaysia being the most affected.
A similar malware campaign, UdangaSteal, was active in Southeast Asia in 2023 and early 2024. However, researchers do not attribute Tria Stealer to the same threat actor, as it demonstrates unique code structures, different Telegram bot setups, and enhanced functionality.
Given the rise of such sophisticated malware, cybersecurity experts recommend the following precautions:
- Avoid Downloading APK Files from Unknown Sources: Only download apps directly from trusted sources like the Google Play Store.
- Verify Messages Before Clicking: Be cautious of messages requesting app installations, even if they appear to come from friends or trusted contacts.
- Enable Two-Factor Authentication (2FA): Use 2FA wherever possible to secure your accounts.
- Use Reliable Security Solutions: Install mobile antivirus tools to detect and block malware.
The Tria Stealer malware campaign highlights the evolving tactics of cybercriminals targeting Android users.
By leveraging social engineering techniques and advanced data exfiltration methods, this malware poses a serious threat to personal and financial security. Users are urged to remain vigilant and adopt best practices to safeguard against such attacks.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request



.png
)
