A vulnerability in Verizon’s Call Filter app for iOS has been discovered, allowing unauthorized access to customer call logs.
This flaw allowed any individual with the requisite technical knowledge to retrieve incoming call data—complete with timestamps—for any Verizon phone number, posing serious risks to privacy and safety.
The Vulnerability Unveiled
The Verizon Call Filter app is designed to help users block spam calls and manage call logs. However, a researcher recently found the app vulnerable to a serious security lapse.
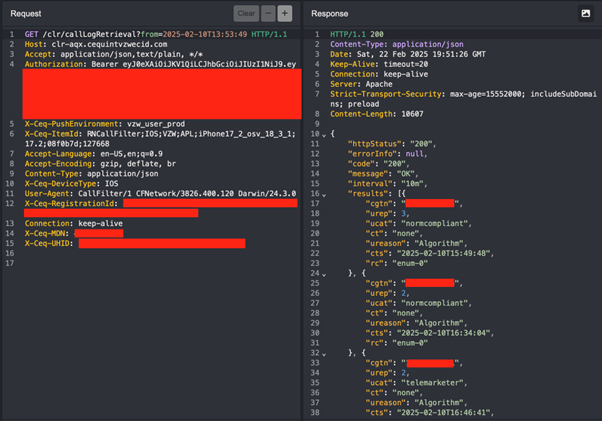
At the core of this issue was the app’s interaction with Verizon’s servers to fetch call history data. A network request sent to the endpoint /clr/callLogRetrieval facilitated this retrieval.
A critical flaw lay in how the app failed to validate that the phone number being queried matched the phone number tied to the signed-in user.
By modifying the phone number in the request header (X-Ceq-MDN) while keeping a valid authorization token (JWT), an attacker could fetch call log data for any Verizon customer.
The JWT payload looked like this:
{
"sub": "SIGNED_IN_USER_PHONE_NUMBER_HERE",
"iat": "1740253712",
"iss": "df88f1ed1dfd9a903e4c8dca7f00089e134c6c4e0a566cd565147ba1dadf78a6",
"secret": "REDACTED",
"alg": "ECDSA-256",
"exp": "1740255512"
}Why This Matters
Call logs might seem inconsequential, but they are far more revealing than they appear.
Metadata such as timestamps and call durations can paint a picture of an individual’s daily routine, personal relationships, and confidential contacts.
For high-risk individuals like journalists, law enforcement officers, politicians, or domestic abuse survivors, such information falling into the wrong hands could have catastrophic consequences.
The breach impacts Verizon’s extensive customer base—possibly extending to all subscribers, as the Call Filter service is believed to be enabled by default.
The findings suggest that the vulnerability was not restricted to specific accounts or user groups.
The server hosting the vulnerable API appears to be owned by Cequint, a telecom technology company specializing in caller ID services.
This raises further questions about the security of customer data stored or managed by third-party contractors like Cequint, especially when such data is tied to one of the largest mobile carriers in the U.S.
While technical details of this vulnerability are now public, its discovery is a stark reminder of the need for vigilance in protecting digital identities.
Whether through stricter validations, internal audits, or addressing the role of third-party security lapses, it’s clear that carriers like Verizon must double down on keeping customer data safe.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



