Over 900 websites inadvertently expose over 10 million passwords, many of which are in plaintext, alongside sensitive billing information and personally identifiable information (PII) of approximately 125 million users.
This massive data exposure is attributed to misconfigured Firebase instances, a popular development platform for creating mobile and web applications, which, due to its ease of use, has led to widespread security oversights.
The Root of the Problem: Firebase Misconfigurations
Firebase, known for its comprehensive suite of tools that aid developers in building, managing, and growing their apps, has a critical flaw in its security rules configuration.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities. :
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
The platform allows for easy misconfiguration with zero warnings, leading to hundreds of sites exposing user records.
This issue came into the spotlight following the initial investigation into Chattr.ai, prompting a more extensive scan for exposed PII across the internet due to misconfigured Firebase instances.
The Hunt for Exposed Data
The quest to uncover the extent of this exposure began with a rudimentary scanner developed in Python, designed to check for Firebase configuration variables in websites or their loaded JavaScript bundles.
However, this approach quickly hit a roadblock as the program began to run out of memory within an hour of its operation.
A subsequent version of the scanner, rewritten in Go by a team member known as Logykk, proved more efficient, not suffering from the memory leak issues of its predecessor.
Despite the improved efficiency, the scanning process was a waiting game. It was initially estimated to take around 11 days but extended to 2-3 weeks to comb through 5 1/2 million domains.
The team also undertook the painstaking task of manually checking each domain, a time-consuming and repetitive process.
A recent report by env has revealed that around 900 websites have inadvertently exposed over 10 million passwords, including sensitive billing information and personally identifiable information (PII) of approximately 125 million users.
Catalyst: The Secondary Scanner
The breakthrough came with the introduction of Catalyst. This secondary scanner automated checking for read access to common Firebase collections and those explicitly mentioned in the JavaScript itself.
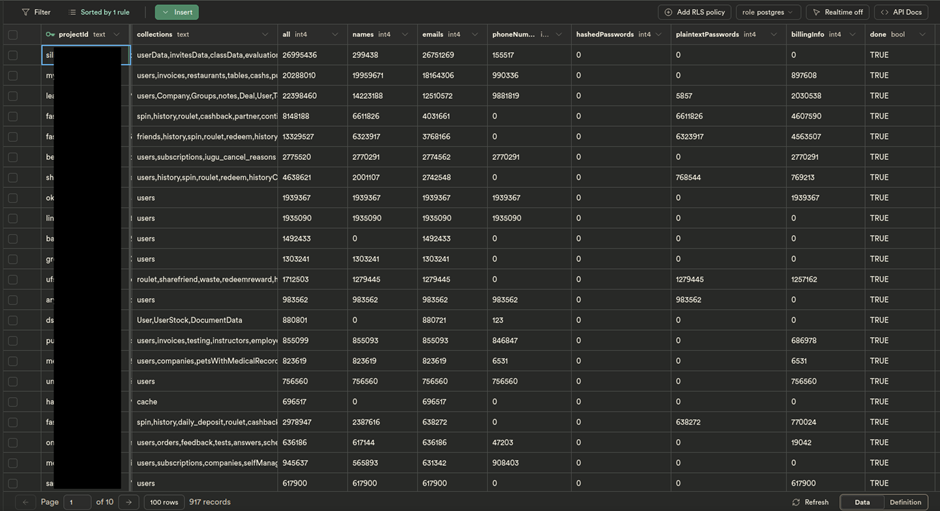
This tool not only identified accessible collections but also assessed the impact of the exposed data by sampling 100 records and extrapolating the findings across the total size of the collection.
The findings were stored in a database using Supabase, an open-source competitor to Firebase, chosen with a touch of irony.
The database contained detailed records of the exposed data, including project IDs, website URLs, counts of names, emails, phone numbers, hashed passwords, plaintext passwords, and billing information.
The Alarming Numbers
The scan revealed staggering numbers:
- Total records exposed: 124,605,664
- Names: 84,221,169
- Emails: 106,266,766
- Phone Numbers: 33,559,863
- Passwords: 20,185,831 (with a significant portion in plaintext)
- Billing Info: 27,487,924
Notable Sites Affected
Among the most affected were:
- Silid LMS: A learning platform with 27 million affected users, leading in total exposed user records.
- Online gambling network: Featuring rigged games and the most exposed bank account details and plaintext passwords.

- Lead Carrot: An online lead generator with 22 million affected people.
- MyChefTool: A restaurant business management app, leading in exposed names and emails.
The team’s efforts to notify the affected sites resulted in 842 emails sent over 13 days, with an 85% delivery rate.
However, only 24% of site owners fixed the misconfiguration, and only 1% responded to the emails.
Alarmingly, only two site owners offered a bug bounty in response to the findings.
This extensive investigation illuminates the critical need for better security practices and awareness among developers using platforms like Firebase.
It also underscores the importance of automated tools in identifying and mitigating data exposure risks on the Internet.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
.webp?w=696&resize=696,0&ssl=1)


.png
)
