A new wave of cyberattacks leveraging the Winos4.0 malware framework has targeted organizations in Taiwan through malicious PDF attachments disguised as tax inspection alerts, according to a January 2025 threat analysis by FortiGuard Labs.
The campaign employs multi-stage payload delivery, anti-forensic techniques, and automated security bypass mechanisms to establish persistent access to victim networks while evading detection.
Phishing Campaign Masquerades as Tax Authority Communications
The attack chain begins with phishing emails purportedly sent from Taiwan’s National Taxation Bureau, claiming to contain a list of enterprises scheduled for tax audits.
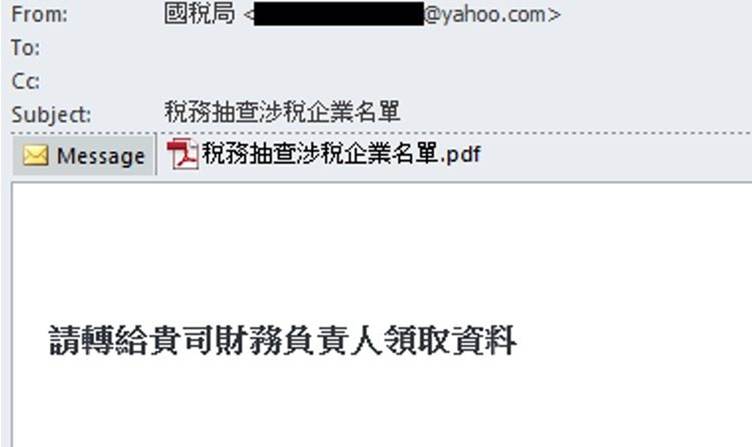
These emails direct recipients to download a malicious ZIP archive attached to a PDF document formatted as an official Ministry of Finance memorandum.
Analysis reveals the PDF (detected as PDF/Agent.A6DC!tr.dldr) contains socially engineered text prompting victims to extract and execute the “20250109.exe” loader from the attached archive.
FortiGuard researchers note this represents a tactical shift from earlier Winos4.0 distribution methods observed in November 2024, which relied on compromised gaming applications.
The strategic use of tax-themed lures during fiscal year-end periods increases click-through rates among corporate finance teams, particularly treasurers explicitly named in the phishing content.
Technical Execution Flow and Evasion Mechanisms
Upon execution, the loader initiates a three-stage process:
- Fake Application Execution: The “ApowerREC.exe” file (a renamed malicious loader) triggers the import of “lastbld2Base.dll”, whose DLLMain function decrypts embedded shellcode containing C2 server configurations (IP 9010[.]360sdgg[.]com) and modular plugin parameters.
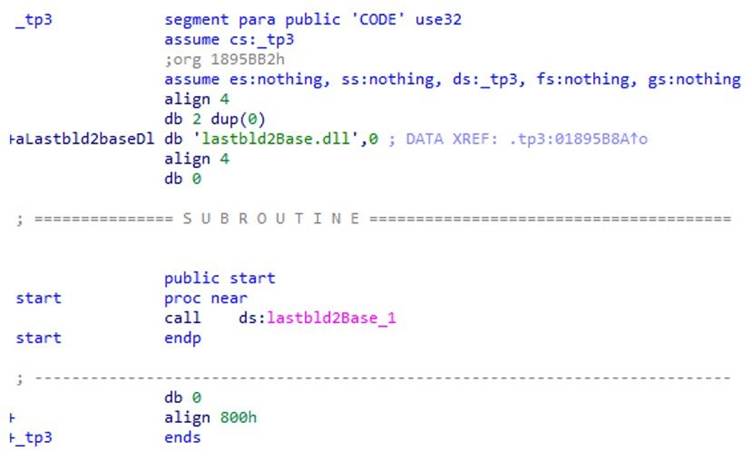
- Anti-Analysis Countermeasures: The shellcode performs sandbox detection via sequential screenshot differential analysis, requiring >20,000 pixel variations between images captured at 2-second intervals to confirm human activity. This stalls automated analysis systems for up to one hour before proceeding.
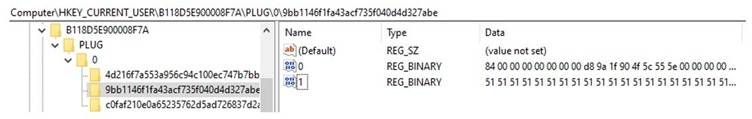
- Registry-Based Payload Storage: Encrypted Winos4.0 modules write to HKEY_CURRENT_USER\B118D5E900008F7A, with secondary shellcode dynamically resolving API calls to unpack the final payload.
The core “loginmodule.dll” establishes eight concurrent threads for lateral movement and data harvesting1:
- MainThread: Disables screen savers via SPI_SETSCREENSAVEACTIVE and forced system wake states (ES_AWAYMODE_REQUIRED). Modifies UAC policies by setting ConsentPromptBehaviorAdmin and PromptOnSecureDesktop registry values to 0 under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System1.
- Anti-AV Thread: Terminates TCP connections associated with 360Safe, Kingsoft, and Huorong security processes using GetTcpTable2 API hooking.
- Clipboard Hijacking: Replaces financial keywords in clipboard data using regex patterns stored in HKEY_CURRENT_USER\B118D5E900008F7A\clipboarddata.
Forensic artifacts show the malware creates mutex objects like Global\MainThreadB118D5E900008F7A to prevent redundant infections and writes keylogged data to C:\ProgramData\B118D5E900008F7A\Regedit.log.
Mitigation Strategies and Defensive Countermeasures
FortiGuard’s response team recommends:
- Enabling Content Disarm & Reconstruction (CDR) on email gateways to neutralize malicious PDF macros.
- Monitoring registry modifications to HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System for UAC bypass attempts.
- Deploying behavioral analysis tools to detect screenshot frequency anomalies and unscheduled system wake events.
Fortinet’s anti-malware suite now blocks associated indicators as W32/Agent.7BBA!tr and W64/ValleyRat.A!tr.spy, with IP reputation services blacklisting confirmed C2 endpoints.
Geopolitical Implications and Campaign Attribution
While no explicit attribution exists, targeting Taiwanese fiscal systems and using Simplified Chinese annotations in USB device logs (“USB device inserted/removed”) suggest potential ties to cross-strait advanced persistent threat groups.
The malware’s infrastructure overlaps with domains previously hosting gaming malware, indicating possible reuse of operational resources across campaigns.
FortiGuard Labs advises organizations to prioritize NSE cybersecurity training modules focused on phishing identification and to implement application allowlisting for executable files.
As Winos4.0 continues evolving its evasion toolkit, multi-layered defenses combining endpoint detection and network traffic analysis remain critical to mitigating these surgically precise attacks.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
