Imagine a government that tracks your daily movements, monitors your communications, and catalogs your digital habits.
While this conjures images of authoritarian regimes, a parallel reality exists in the United States, where law enforcement agencies leverage the vast data reservoirs of Big Tech companies to construct intrusive profiles of citizens.
Over the past decade, Google, Meta, and Apple have collectively shared user data for over 3.16 million accounts with U.S. authorities, creating what critics call the world’s most pervasive surveillance infrastructure.

The Scale of Data Sharing
Between 2014 and 2024, U.S. law enforcement requests to tech giants surged exponentially. Google disclosed a 530% increase in accounts shared, Meta reported a 675% jump, and Apple’s compliance rose by 621%.
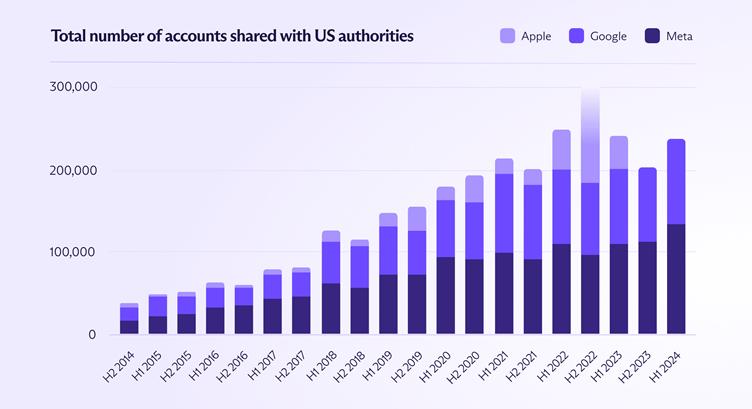
This escalation peaked in mid-2022, when Apple alone handed over details for 300,000 accounts in six months.
These figures exclude secretive requests under the Foreign Intelligence Surveillance Act (FISA), which enable warrantless access to data for national security purposes.
In the most recent 12-month period with available data (late 2023 to mid-2024), U.S. agencies submitted nearly 500,000 data requests to Google and Meta — surpassing the combined total of all 14 Eyes Alliance nations, including the UK, Canada, and Australia.
This reliance reflects a systemic shift: law enforcement now treats Silicon Valley as a de facto extension of its investigative toolkit.
The Architecture of Surveillance
Tech companies’ business models depend on harvesting user data for targeted advertising. Meta’s 2023 revenue was 98% ad-dependent, while Google Ads accounted for 77% of Alphabet’s income.
To sustain this, platforms deploy invasive tools like the Meta Pixel, which embeds trackers across third-party websites, from healthcare portals to banking apps.
A 2024 investigation revealed that Meta accumulated 20,000 pages of data on a single journalist, documenting offline purchases, app usage, and even interactions with local government services.
Apple and Google similarly compile granular profiles through location histories, search queries, and ecosystem integrations.
Once collected, this data becomes vulnerable to reverse warrants — a controversial legal tool allowing bulk access to information based on geographic areas (“geofencing”) or search terms.
Such methods have led to wrongful arrests, including individuals falsely accused of burglary and murder.
The Oversight Gap
While companies claim to scrutinize data requests, FISA Section 702 permits intelligence agencies to bypass judicial review entirely.
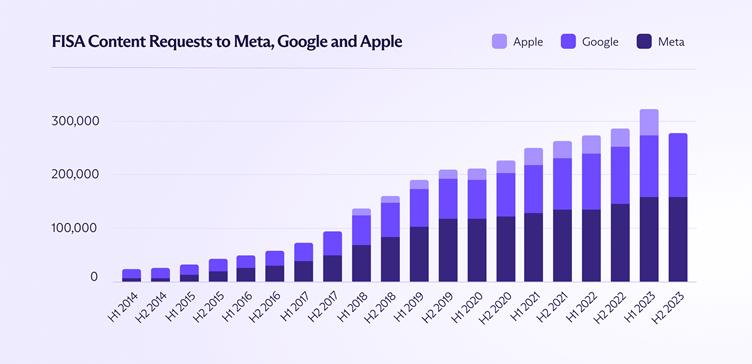
Between 2014 and 2023, FISA content demands to Meta spiked 2,171%, while Google saw a 594% increase. National Security Letters (NSLs), which prohibit companies from disclosing requests, further obscure accountability.
Legal experts argue that even “legitimate” subpoenas often overreach. “Geofencing warrants cast a digital dragnet,” explains civil liberties attorney Alan Butler. “They sacrifice individual privacy for investigative convenience”.
End-to-end encryption — a proven safeguard — remains incompatible with ad-driven platforms. Apple, despite marketing itself as privacy-focused, has quadrupled its ad revenue since 2020, outpacing social media rivals like Snap and X.
This tension underscores a systemic conflict: protecting user privacy would require dismantling surveillance capitalism itself.
The company publishes annual transparency reports and open-sources its code, contrasting sharply with Big Tech’s opacity, as per a report by Proton.
“Marginalized communities face unprecedented digital threats,” says Proton CEO Andy Yen. “Privacy isn’t a luxury — it’s a right”.
As governments and corporations deepen their data symbiosis, such alternatives may represent the last line of defense for civil liberties.
The scale of modern surveillance hinges on a Faustian bargain: convenience in exchange for constant monitoring. Until regulatory or technological shifts disrupt this paradigm, Big Tech’s grip on personal data will only tighten — one subpoena at a time.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



