A critical security vulnerability in Xerox’s Versalink C7025 Multifunction Printer (MFP) has been uncovered, exposing enterprise networks to credential theft and lateral attacks.
The flaw, discovered by Rapid7 Principal IoT Researcher Deral Heiland, enables malicious actors to intercept Lightweight Directory Access Protocol (LDAP) and Server Message Block (SMB) authentication data through pass-back attacks.
The vulnerabilities, tracked as CVE-2024-12510 and CVE-2024-12511, threaten organizations relying on these widely used devices for printing, scanning, and document management.
The Versalink C7025’s LDAP configuration flaw allows attackers with admin access to redirect authentication requests to rogue servers.
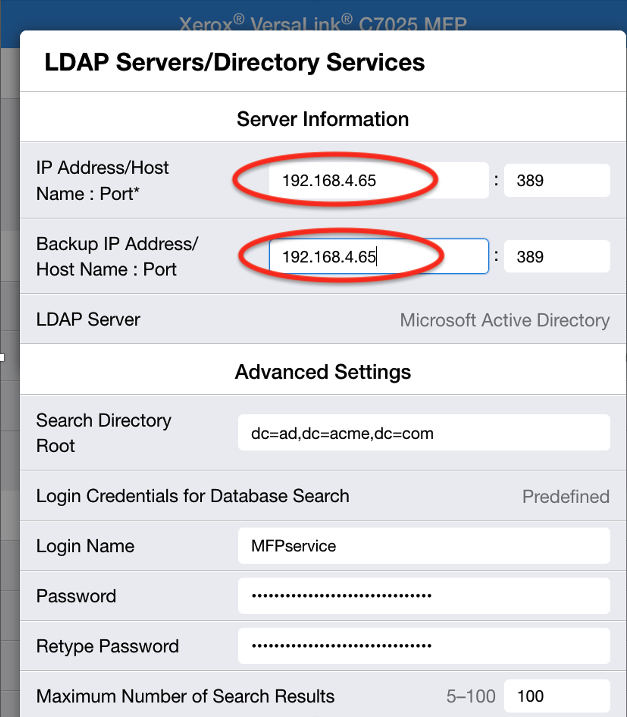
By modifying the LDAP server’s IP address in the printer’s settings, adversaries can capture plaintext credentials through a simple netcat listener.
This method directly compromises Active Directory (AD) integrity, as LDAP is central to user authentication in Windows environments.
For SMB, attackers exploit the device’s address book feature to reroute scan-to-file operations to controlled servers. This tactic harvests NetNTLMv2 handshakes—cryptographic tokens attackers use in relay attacks to infiltrate file servers.
FTP configurations are equally vulnerable, with credentials transmitted in clear text if compromised.
While both attack vectors require administrative privileges or physical console access, enterprises often retain default admin passwords or enable remote management interfaces, lowering the barrier to exploitation.
The implications are severe: captured credentials enable lateral movement, privilege escalation, and data exfiltration across corporate networks.
Xerox has released firmware updates addressing these issues, urging customers to install patches immediately.
Rapid7 recommends additional safeguards: restrict admin access to MFPs, disable unnecessary services like FTP, and implement network segmentation to isolate printers from critical AD infrastructure.
Monitoring for anomalous LDAP/SMB traffic and enforcing multi-factor authentication (MFA) for printer management consoles are also advised.
“These vulnerabilities underscore the risks of treating IoT devices as perimeter appliances rather than core network assets,” Heiland noted.
“Printers, cameras, and sensors often have privileged access but lack robust security controls, making them prime targets for initial breaches.”
The disclosure follows coordinated efforts between Rapid7 and Xerox, reflecting growing scrutiny of IoT device security in hybrid work environments.
For enterprises, the discovery highlights the need to audit connected devices routinely. As MFPs increasingly integrate with cloud services and corporate directories, their role as potential attack vectors grows proportionally.
With credential-based attacks dominating cybersecurity incident reports, mitigating such flaws in edge devices becomes critical to holistic defense strategies.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



