A new zero-day vulnerability in macOS let hackers to bypass the system security warnings and to compromise easily with Synthetic Click. Security researcher Patrick Wardle revealed the critical vulnerability at his conference Objective By The Sea over this weekend.
Last year he showed that it is possible to create synthetic clicks the with automation scripts in macOS High Sierra, later in macOS Mojave the privacy protections have been exported.
Now he found another way to bypass the security protections to perform Synthetic Clicks and to access the user’s data without the user’s consent.
The vulnerability resides in ‘Apple’s code that checks only for the existence of the certificate but not the integrity of the Trusted apps. An attacker can tamper an application from the list of trusted apps to generate synthetic clicks, which was normally allowed by the operating system.
Wardle demonstrated the attack with VLC media player to deliver his malicious plugin for generating a synthetic click on prompt’s without user consent.
“”For VLC, I just dropped in a new plugin, VLC loads it, and because VLC loads plugins, my malicious plugin can generate a synthetic click — which is fully allowed because the system sees its VLC but ‘doesn’t validate that the bundle to make sure it ‘hasn’t been tampered with,” he explained to Techcrunch.
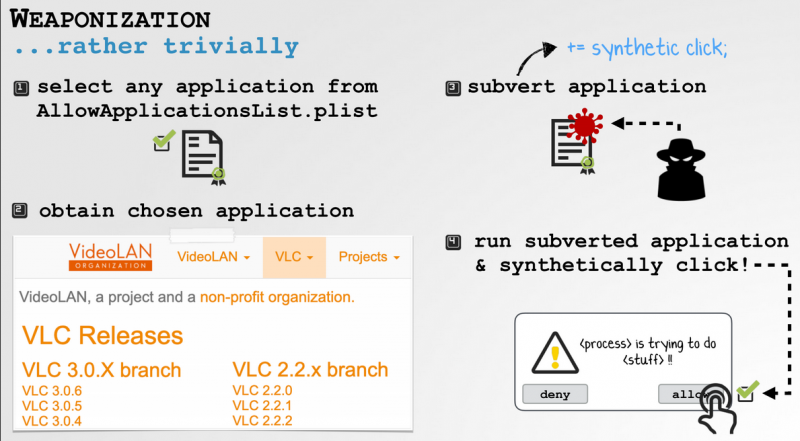
To execute the attack, the attacker should have physical access to the Laptop, but not required to have any elevated privileges.
Wardle reported the vulnerability to Apple before a week, and the company confirms the report, but it is unclear when it is scheduled to address the vulnerability.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity courses online to keep yourself updated.



.png
)
