The Underground hacking Forums are the market place for cybercriminals to advertise various malware variants and other hacking tools. A new report represents the top malware families advertised.
By analyzing more than 3.9 million posts, Recorded Future’s, Insikt Group identified the top malware variants that are advertised in the hacking and it’s a correlation with real-world attacks.
The majority of the malware’s are in multiple languages that includes openly available dual-use tools, open-source malware, or cracked malware and some of the malware families are three years old.
Insikt Group also learned that Underground hacking Forums in different languages such as English- and Chinese-speaking and focus on different malware, malware categories, and attack vectors.
Top 10 Malware Advertised in Underground hacking Forums
The top 10 malware categories include dual-use tools such as MinerGate and Imminent Monitor, open-source malware that includes njRat, AhMyth, Mirai and over three years old malware Gh0st RAT.
According to the report the Chinese- and English-speaking underground focus more on the Android devices. Following are the most discussed Android Trojan in Chinese forums that includes SpyNote, AhMyth, and DroidJack, in English speaking forums SpyNote and DroidJack.
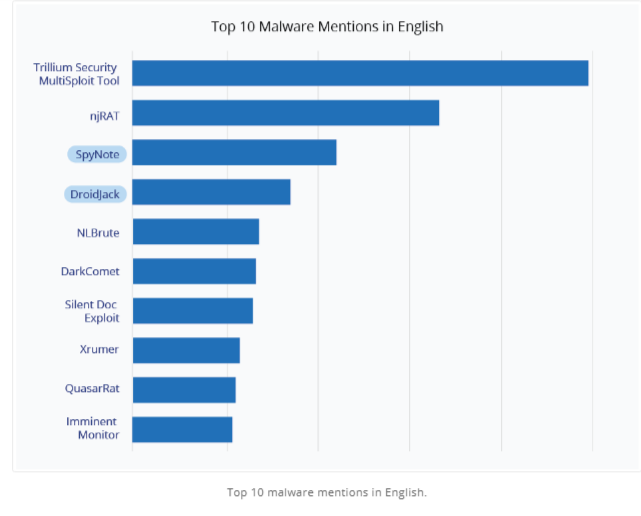
The NJRat is popular among English speaking forums, which is known for its stealthy functions. It uses to run silently in the background and also capable of disabling Antivirus programs and other Windows security features.
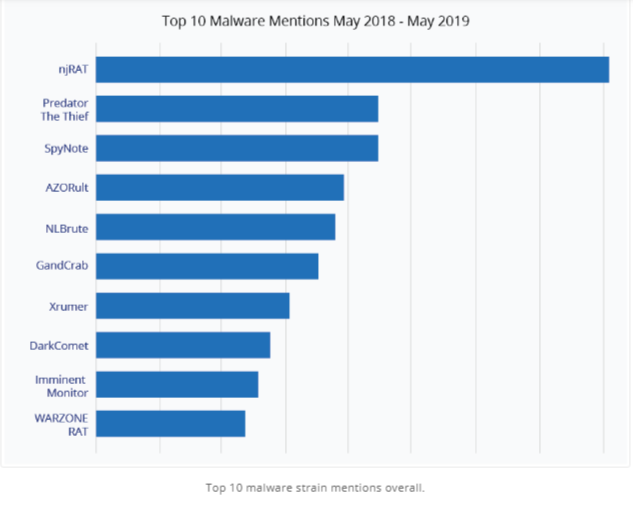
Insikt Group also determines the top malware categories that are mentioned from May 2018 to May 2019, the top categories are the ransomware, crypter, trojan, and web shells.

“Out of the top 150 strains of malware collected, only 11 were ransomware, approximately 50% of the mentions lower-level ransomware that do not have names or branding.”
Following are the top 10 malware mentions that include remote-access trojans, information stealers, brute force and forum specific tools.
Top malware and their delivery mechanism

Top malware hashes

“The malware vendors also post comments on the original sales thread or create new sales threads to provide updates to the variants to get higher post-exposure within the forum to attract additional buyers.”
Organizations are recommended to prioritize patching for security vulnerabilities and to implement proper defense mechanisms and security procedures.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.
Related Read:
Two Hackers of Bayrob Malware Gang Convicted for Infecting more than 400,000 Computers Worldwide



.png
)
