Cybersecurity researchers at vx-underground have reported that over 70 million records from an unspecified division of telecommunications giant AT&T have been leaked online.
The breach, one of the largest in recent times, has raised serious concerns about data security and privacy.
The Breach Exposed
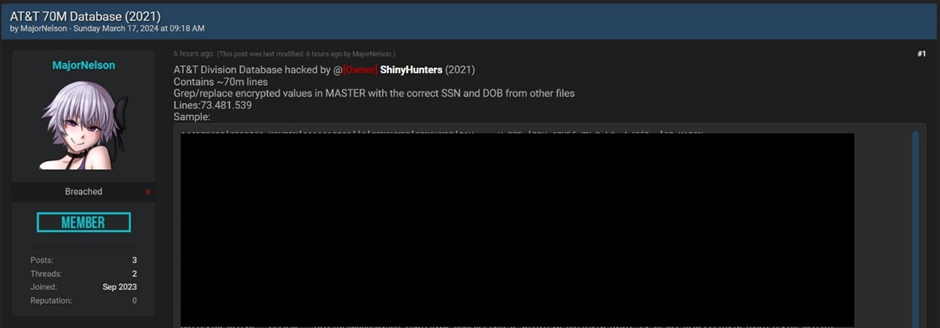
The leaked data, posted on the hacker forum Breached, contains 73,481,539 records.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
However, it remains uncertain whether the information was directly stolen from AT&T or through a third-party organization associated with the company.
Hacker Group Behind the Leak
The individual responsible for the data sale uses the online alias, Major Nelson. They claim the data was acquired from an unnamed AT&T division by the notorious hacker group @ShinyHunters in 2021.
ShinyHunters is infamous for its cyberattacks on several significant organizations, including Tokopedia, Homechef, Chatbooks.com, Microsoft, and Minted.
Security Affairs has reported that threat actors have leaked over 70 million records, which they allegedly stole from AT&T.
Data For Sale
In August 2021, ShinyHunters reportedly demanded $1 million for the entire database or $200,000 for partial access.
The RestorePrivacy website verified the authenticity of the data by analyzing a sample and finding it legitimate.
The leaked data includes sensitive customer information such as Name, Phone number, Physical address, Email address, Social security number, Date of birth, Sample Data Leak
AT&T’s Response
Despite the claims and the evidence presented by researchers and the hacker group, AT&T has denied any breach of their systems.
The telecommunications giant said, “Based on our investigation Thursday, the information that appeared in an internet chat room does not appear to have come from our systems.”
Implications for Customers
The alleged data breach threatens the affected customers, with the potential for identity theft, financial fraud, and other malicious activities.
The data in question could be used by cybercriminals to orchestrate targeted phishing attacks or to sell to other bad actors on the dark web.
As the situation unfolds, AT&T customers are advised to remain vigilant and monitor their accounts for suspicious activity.
It is also recommended that passwords be changed and credit monitoring services be considered to safeguard against potential identity theft.
With Perimeter81 malware protection, you can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits. All are incredibly harmful and can wreak havoc on your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
.webp?w=696&resize=696,0&ssl=1)

