Researchers discovered a previously undetected multi-platform malware called ACbackdoor that has both Linux and Windows Variant to infect the respective users and steal sensitive information.
Dubbed ACbackdoor Linux variant has a completely no detection rate while the Windows variant has a higher detection rate than the Linux variant.
Researchers believe that the ACbackdoor variant is completely undocumented to the infosec community, and there is no evidence found that the malware associated with any known threat groups.
Malware has a variety of sophisticated features such as arbitrary execution of shell commands, arbitrary binary execution, persistence, and update capabilities.
Malware authors behind this campaign have previously experience targeting Linux systems, and now they turn out to attack the Windows users.
Also, the Linux variant has been written better than Windows in terms of persistence mechanism along with the different backdoor commands.
ACbackdoor Infection Process
Both Linux and Windows variant has a variety of similarities, for instances, both variants using the same protocol to communicate with the command & control server and minor implementation differences.
In the binary analysis, researchers found that the Linux binary is a statically linked ELF file, while the Windows binary is a dynamically linked PE file.
Linux variant infection activities found in the Romanian host server, but the infection process and the delivery were unclear.
Windows variant of ACbackdoor initially reported by @nao_sec via twitter, and the using a Fallout Exploit Kit as a delivery medium.
Backdoor Functionality
Unlike other Widows malware, the ACbackdoor Windows version doesn’t pose any complete functionality, but the Linux variant has a sophisticated feature in terms of the infection process.
After the complete infection, the Windows variant collecting architecture, system, and MAC address information by calling the correspondent Windows API functions.
“At the same time, Linux variant uses a different technique that mainly relies on uname system call to retrieve architecture and system information, in addition to a combination of socket / ioctl system calls to retrieve the MAC address, Intezer said via a blog post.
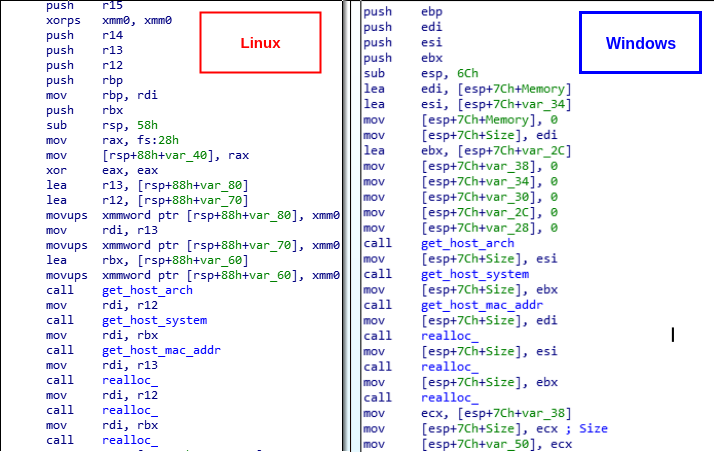
“The Windows instance will initialize a registry entry so that the malware will be executed on system start-up. The Linux instance will set up various symbolic links and add an initrd script for the malware to also run on system start-up.”
At the final stage, both variants using the same HTTPS protocol to communicate with the c2 server and share the collected information from victims.
These specific details along with the analysis above have led us to conclude that the authors behind ACBackdoor are more comfortable operating in Linux systems, while they may currently be experimenting in Windows by porting their malware to this system. Intezer Wrote.



.png
)
