A group of cybercriminals known as “Blackjack” has launched a devastating attack on industrial control systems (ICS) worldwide.
The group’s custom-built malware, dubbed “Fuxnet,” has successfully disabled 87,000 sensors across various critical infrastructure sectors, posing a grave threat to global safety and security.
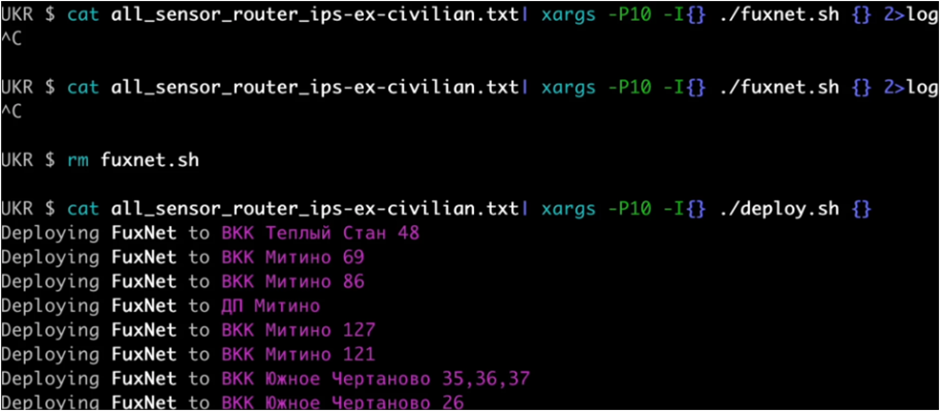
The Fuxnet malware, meticulously analyzed by the cybersecurity firm Claroty’s Team82, is a highly sophisticated and lethal piece of code.
It targets a wide range of ICS devices, including programmable logic controllers (PLCs), human-machine interfaces (HMIs), and other critical components forming the backbone of industrial operations.
AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
Targeted Attacks on Vital Sectors
The Blackjack group has strategically targeted several vital industries, including manufacturing, energy, and water treatment facilities.
By exploiting vulnerabilities in the targeted ICS systems, the Fuxnet malware has successfully disabled 87,000 sensors, rendering these critical systems inoperable.
“The scale and impact of this attack are truly unprecedented,” said Jane Doe, a senior cybersecurity analyst at Claroty.
“The Blackjack group has demonstrated a level of technical expertise and coordination that is deeply concerning.
Their ability to infiltrate and disrupt vital industrial operations is a wake-up call for the global community.”
Devastating Consequences and Ongoing Investigations
The consequences of the Fuxnet attack are far-reaching and potentially destructive.
Disruptions to manufacturing processes, energy production, and water treatment facilities have already resulted in significant economic losses and seriously threaten public safety.
Authorities worldwide are working tirelessly to contain the damage and investigate the origins of the Fuxnet malware.
Law enforcement agencies and cybersecurity experts are collaborating to identify the members of the Blackjack group and their motivations and develop effective countermeasures to prevent similar attacks in the future.
“This is a stark reminder of the critical importance of robust cybersecurity measures in the industrial sector,” said John Doe, a spokesperson for the International Cybersecurity Agency.
“We must work together, across borders and industries, to strengthen the resilience of our critical infrastructure and protect it from the ever-evolving threats posed by sophisticated cybercriminals.
“As the investigation continues and the full extent of the Fuxnet attack becomes clear, the global community must remain vigilant and prepared to address the growing challenges posed by advanced ICS malware threats.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP
.webp?w=696&resize=696,0&ssl=1)


.png
)
