Researchers observed a new PHP web shell dubbed Ensiko with ransomware capabilities that attack PHP installed on platforms such as Linux, Windows, macOS, and others.
The malware is capable of providing remote access and accepts commands from the attacker via a PHP reverse shell.
Security researchers from Trend Micro observed that the malware scans infected servers for the presence of other webshells, defacing websites, sending mass emails, downloading remote files, disclosing information about the affected server, brute-force attacks against file transfer protocol (FTP), cPanel, and Telnet, overwriting files with specified extensions, and more.
Webshell With Ransomware Capabilities
The malware is password-protected, it displays a not found page with a hidden login form. It uses RIJNDAEL_128 with CBC mode to encrypt files in the web directories and appends the “.bak” extension.
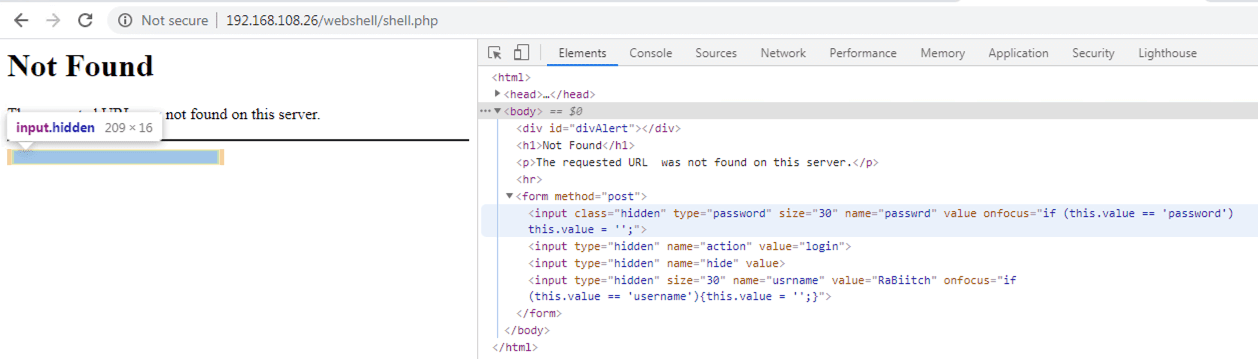
It also drops an index.php file and sets it as the default page using a .htaccess file, the malware also loads additional tools onto an infected system.

Following are the Ensiko’s capabilities;
| Features | Description |
| Priv Index | Download ensikology.php from pastebin |
| Ransomeware | Encrypt files using RIJNDAEL 128 with CBC mode |
| CGI Telnet | Download CGI-telnet version 1.3 from pastebin;CGI-Telnet is a CGI script that allows you to execute commands on your web server. |
| Reverse Shell | PHP Reverse shell |
| Mini Shell 2 | Drop Mini Shell 2 webshell payload in ./tools_ensikology/ |
| IndoXploit | Drop IndoXploit webshell payload in ./tools_ensikology/ |
| Sound Cloud | Display sound cloud |
| Realtime DDOS Map | Fortinet DDoS map |
| Encode/Decode | Encode/decode string buffer |
| Safe Mode Fucker | Disable PHP Safe Mode |
| Dir Listing Forbidden | Turn off directory indexes |
| Mass Mailer | Mail Bombing |
| cPanel Crack | Brute-force cPanel, ftp, and telnet |
| Backdoor Scan | Check remote server for existing web shell |
| Exploit Details | Display system information and versioning |
| Remote Server Scan | Check remote server for existing web shell |
| Remote File Downloader | Download file from remote server via CURL or wget |
| Hex Encode/Decode | Hex Encode/Decode |
| FTP Anonymous Access Scaner | Search for Anonymous FTP |
| Mass Deface | Defacement |
| Config Grabber | Grab system configuration such as “/etc/passwd” |
| SymLink | link |
| Cookie Hijack | Session hijacking |
| Secure Shell | SSH Shell |
| Mass Overwrite | Rewrite or append data to the specified file type. |
| FTP Manager | FTP Manager |
| Check Steganologer | Detects images with EXIF header |
| Adminer | Download Adminer PHP database management into the ./tools_ensikology/ |
| PHP Info | Information about PHP’s configuration |
| Byksw Translate | Character replacement |
| Suicide | Self-delete |
The threat actor also employees the steganography technique to hide code within the exchangeable image file format (EXIF) headers of an image file.

The malware also includes two scanning methods;
Backdoor Scan – Scans for the existence of a web shell from a hardcoded list.
Remote server scan – Checks infected web server for the presence of other web shells.
Also it employees a function Mass Overwrite that used to rewrite/append the content of all files with directories and subdirectories.
By injecting an Ensiko web shell attacker can enable remote administration, file encryption, and many more features on a compromised web server.
IoC
SHA-256 Hash
5fdbf87b7f74327e9132b5edb5c217bdcf49fe275945d502ad675c1dd46e3db5
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity, and hacking news updates.
Also Read
APT Group Actively Exploiting Internet-facing Vulnerable ColdFusion Server and Uploading Webshell
APT 34 Hackers Group Owned Hacking Tools, Webshell, Malware Code, C2 Servers IP Leaked in Telegram



.png
)
