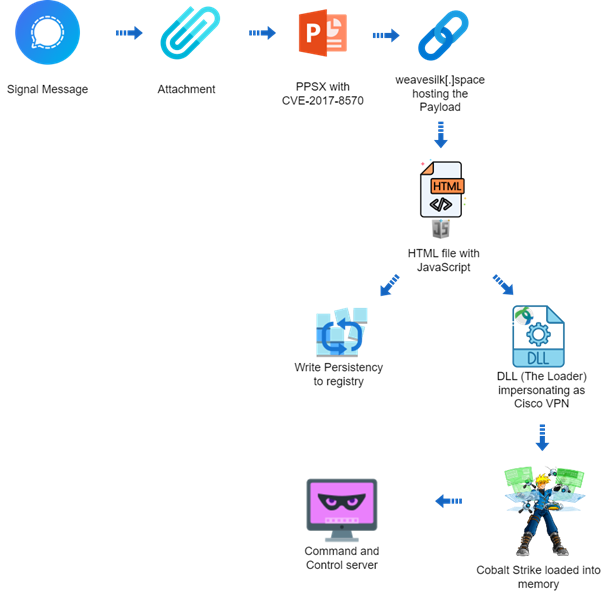
Hackers have leveraged an old Microsoft Office vulnerability, CVE-2017-8570, to deploy the notorious Cobalt Strike Beacon, targeting systems in Ukraine.
It has been closely monitoring the situation and has successfully detected all stages of the attack.
CVE-2017-8570: The Initial Vector
The attack begins with the exploitation of CVE-2017-8570, a vulnerability first identified in 2017.
This vulnerability allows attackers to execute arbitrary code via specially crafted files, making it a potent tool for initial access.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
The attackers used a malicious PPSX (PowerPoint Slideshow) file, masquerading as an old US Army instruction manual for mine-clearing tank blades.

The file was cleverly designed to bypass traditional security measures.
It included a remote relationship to an external OLE object, utilizing a “script:” prefix before an HTTPS URL to conceal the payload, avoid on-disk storage, and complicate analysis.
This technique highlights the attackers’ sophistication and focus on stealth and persistence.
Deep Instinct Threat Lab has played a crucial role in uncovering and analyzing this cyberattack.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Despite the detailed analysis, the operation could not be attributed to any known threat actor.
This lack of attribution adds complexity to the defense against these attacks, as understanding the adversary is critical to predicting and mitigating their tactics and techniques.
Cobalt Strike Beacon: Custom Loader
Central to this campaign is using a custom loader for the Cobalt Strike Beacon, a popular tool among cyber attackers due to its powerful command-and-control (C&C) capabilities and flexibility in deploying further payloads.
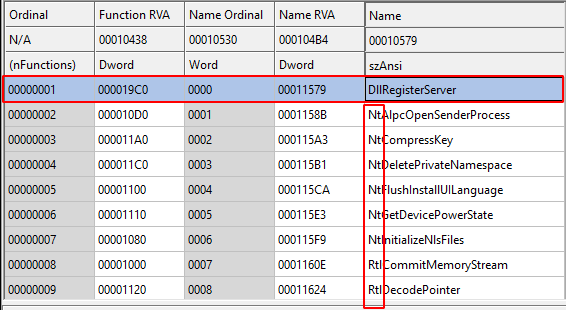
The Cobalt Strike Beacon used in this attack was configured to communicate with a C&C server, cleverly disguised as a popular photography website but hosted under suspicious conditions.
The Beacon’s configuration included a cracked version of the software, indicated by a license_id of 0, and detailed instructions for C&C communications, including the domain name, URI, and public key for encrypted exchanges.
This setup not only facilitates robust control over the compromised systems but also complicates defenders’ efforts to intercept or disrupt communication.
Their technology has successfully detected all stages of the attack, from the initial document delivery to the execution of the Cobalt Strike Beacon.
This comprehensive detection capability is critical in a landscape where attackers constantly evolve their methods to evade detection.
Implications and Recommendations
This attack underscores the importance of vigilance and advanced detection capabilities in the cybersecurity domain.
Organizations are advised to update their systems regularly to patch known vulnerabilities like CVE-2017-8570.
Employ advanced threat detection solutions to identify and mitigate sophisticated threats, such as those posed by custom Cobalt Strike loaders.
As the situation develops, it remains crucial for cybersecurity communities to share information and collaborate on defense strategies, ensuring that they stay one step ahead of cyber adversaries.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training -> Try Free Demo



.png
)
