Security researchers from Trend Micro observed a new malware activity targeting devices running the Linux platform, the malware samples found to be connected with Momentum Botnet.
The malware campaign targets to install a backdoor on the Linux platform that accepts commands from attackers server to conduct various types of DoS attacks against a given target.
Momentum Botnet Attack Campaign
The Momentum botnet targets the Linux platform running on various CPU architectures such as ARM, MIPS, Intel, Motorola 68020, and more. Mirai, Kaiten, and Bashlite are the backdoor variants distributed by the Momentum botnet.
The botnet exploits various vulnerabilities on the targeted router devices and web services to deploy and execute PowerShell scripts.
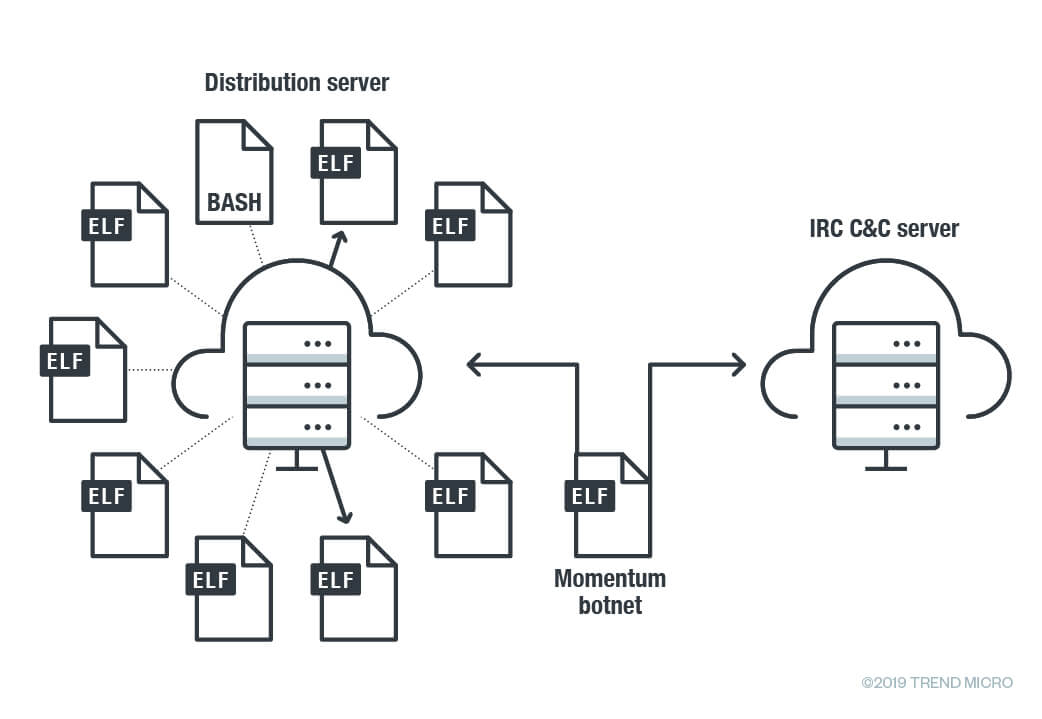
Once the botnet infects the device it modified run commands config file “rc” and adds them to command and control (C&C) server through internet relay chat (IRC) channel.
Then the infected device gets connected with the distribution server, it uses various commands to launch 36 different methods using the compromised devices.
| Command | Description |
| ACK | ACK flooder |
| ADV-TCP | TCP flooding – Improved SSYN Attack |
| BLACKNURSE | An ICMP packet flooder |
| DNS | DNS amplification flooder |
| ECE attacking (Not in use) | Type of SYN flood |
| ESSYN | ExecuteSpoofedSyn Flooder |
| FIN attacking (Not in use) | FIN flood |
| FRAGACK | ACK Fragmentation Flood |
| FRAG-TCP | Spoofed TCP Fragmentation Flooder |
| GRE | GRE flood |
| HOLD (Not in use) | TCP connect flooder(frag) |
| HTTP | HTTP Flooder |
| HTTPFLOOD | HTTP flooding |
| JUNK | TCP flooder (frag) |
| LDAP | LDAP amplification flooder |
| MEMCACHE | MEMCACHE amplification flooder |
| NSACK | Type of ACK flood |
| NSSYN | Type of SYN flooder |
| OVH | Type of UDP flooding (DOMINATE) |
| PHATWONK | Multiple attacks in one e.g. xmas, all flags set at once, usyn (urg syn), and any TCP flag combination. |
| RTCP | A Random TCP Flooder Fragmented packet header |
| SACK | Type of TCP flood |
| SEW Attack | Type of SYN flood |
| SSYN2 | Type of SYN flood |
| STUDP | STD Flooder |
| STUDP | STD Flooder |
| SYN | SYN flooder |
| SYNACK | SYN-ACK flood |
| TCPNULL | TCP-Nulled flooding – Flood with TCP packets with no flag set |
| UDP | UDP flood |
| UDP-BYPASS | A udp flooder (vulnMix) |
| UNKNOWN | UDP Flooder |
| URG attacking | – |
| VOLT-UDP | Spoofed UDP Flooder, Can Bypass most firewall |
| VSE | Valve Source Engine Amplification |
| XMAS | TCP Xmas flood |
Researchers observed that with MEMCACHE, LDAP, DNS, and Valve Source Engine, the malware attack typically spoofs the source IP address to publicly accessible servers.
The botnet is also capable of “opening a proxy on a port on a specified IP, changing the nick of the client, disabling or enabling packeting from the client, and more.”
With LDAP DDoS reflection, Memcache attack the botnet spoofs the source IP address and with UDP-BYPASS attack targets the host by constructing and unloading a legitimate UDP payload on a specific port.
The Momentum botnet includes other capabilities such as Fast flux, Backdoor and Propagate to spread and compromise devices.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
