In today’s interconnected world, where digital communication and transactions dominate, phishing attacks have become an ever-present threat.
By masquerading as trustworthy entities, phishing attacks deceive users and organizations into divulging sensitive information, such as passwords, financial data, and personal details.
Phishing attacks, among the most prevalent techniques cyber criminals employ, can be straightforward yet highly effective.
Unlike breaching fortified firewalls and other robust defenses, tricking individuals into clicking malicious links or opening infected attachments is comparatively more straightforward.
The objectives of phishing attacks vary, ranging from delivering malware to stealing funds and pilfering credentials.
However, exercising sufficient vigilance can detect most attempts to extract personal information.
What is Phishing Attack?

A phishing attack is a deceptive tactic employed by cybercriminals to trick individuals or organizations into revealing sensitive information or performing certain actions that can be exploited for malicious purposes.
Phishing attacks typically involve impersonating a trustworthy entity through emails, text messages, or fraudulent websites, such as a legitimate company, government agency, or financial institution.
The attackers aim to manipulate their targets into divulging confidential data, such as passwords, credit card numbers, social security numbers, or login credentials.
They frequently employ various psychological, urgency, and social engineering techniques to create a belief in legitimacy and urgency, luring victims to perform the desired actions.
Phishing attacks can lead to severe consequences, including identity theft, financial loss, unauthorized access to accounts, and compromised systems. Consequently, it is essential to maintain vigilance and implement preventative measures to defend against such attacks.
Types of Phishing Attacks
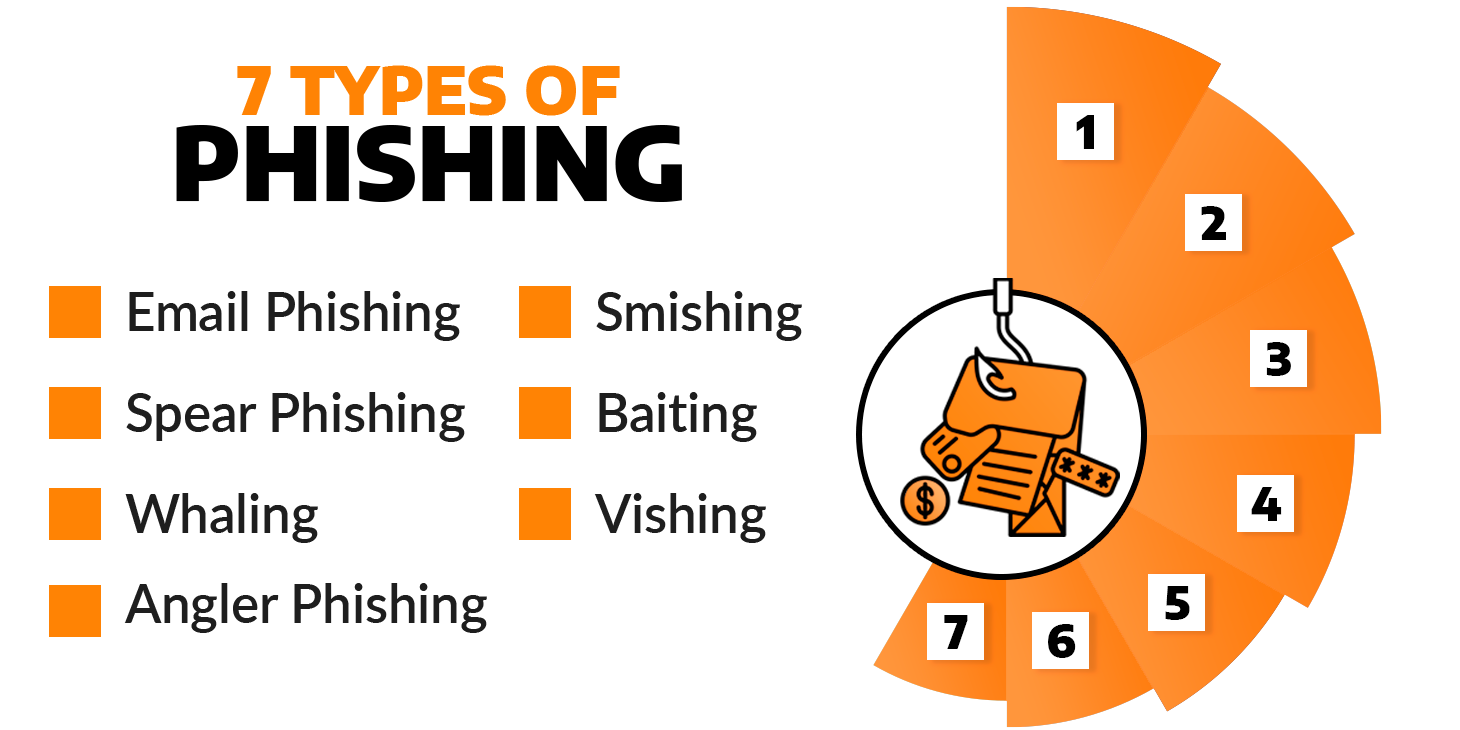
Cybercriminals employ several types of phishing attacks to exploit individuals and organizations. Some common types include:
- Email Phishing: Attackers send deceptive emails, often impersonating legitimate organizations, intending to trick recipients into revealing sensitive information or performing malicious actions.
- Spear Phishing: This attack addresses specific individuals or organizations, using personalized information to appear more authentic and increase the likelihood of success.
- Whaling: Similar to spear phishing, whaling targets high-profile individuals, such as CEOs or top executives, aiming to gain access to valuable company information or financial assets.
- Smishing: Phishing attacks are conducted via SMS or text messages, in which perpetrators convince targets to click on fraudulent links or provide personal information.
- Vishing: Vishing, also known as voice phishing, entails attackers making phone calls, posing as representatives of reputable organizations, and convincing victims to divulge sensitive information.
- Pharming: Intruders manipulate DNS settings or employ malware to reroute users from legitimate websites to fraudulent ones, where they can harvest sensitive data.
- Clone Phishing: Attackers create a replica of a legitimate email or website, making minor modifications to deceive recipients into providing their credentials or other sensitive data.
- Man-in-the-Middle (MitM) Attacks: In this type of attack, the attacker intercepts communication between two parties, gaining unauthorized access to information shared during the conversation.
- Business Email Compromise (BEC): Attackers impersonate company executives or employees to trick employees into initiating unauthorized wire transfers or revealing sensitive business information.
- Angler Phishing: This type of attack targets social media platforms, where attackers create fake customer support accounts or pages to steal login credentials or personal information.
How Does a Simple Phishing Attack Lead to Major Cyber Attacks
- Initial Compromise: In a simple phishing attack, an attacker sends a fraudulent email or message to trick a user into divulging sensitive information, such as login credentials or account details. The attacker gains unauthorized access to the victim’s account or network if successful.
- Credential Harvesting: With the compromised credentials, the attacker can access the victim’s email, social media, or other accounts. This allows them to gather more information about the victim, including contacts, personal details, and potentially additional login credentials.
- Lateral Movement: With access to the victim’s account or network, the attacker can move laterally within the organization’s systems, escalating their privileges and seeking additional targets. They may exploit vulnerabilities in the network, search for weakly protected accounts, or target privileged users with higher access levels.
- Internal Reconnaissance: Once inside the network, the attacker conducts reconnaissance to gather information about the organization’s infrastructure, systems, and potential high-value targets. They may search for valuable data, intellectual property, or sensitive information that could be monetized or used for future attacks.
- Persistence and Persistence: The attacker may establish persistence within the compromised systems by installing backdoors, creating additional user accounts, or modifying existing configurations. This allows them to maintain access even if initial entry points are discovered and patched.
- Expansion of the Attack: With a foothold in the organization’s network, the attacker can launch more advanced attacks such as spear-phishing, ransomware deployment, or data exfiltration. They can leverage compromised accounts and systems to distribute malicious payloads, infect other devices, or gain unauthorized access to critical infrastructure.
- Advanced Malware Deployment: The attacker may deliver sophisticated malware or exploit kits to compromise additional systems or gain control over critical infrastructure. This can include deploying ransomware, stealing sensitive data, or conducting sabotage activities.
- Data Breach and Damage: A successful phishing attack can lead to a data breach, exposing sensitive information, customer data, or proprietary information. The consequences include financial losses, reputational damage, legal ramifications, and regulatory non-compliance.
Top Prevention Checklist for Phishing Attacks
Phishing attacks have emerged as a significant threat in today’s digital landscape, exploiting human vulnerability rather than relying solely on technical vulnerabilities.
Cybercriminals utilize deceptive tactics to trick individuals and organizations into divulging sensitive information or performing malicious actions. Implementing robust preventive measures is crucial to combat this pervasive threat.
The following prevention checklist provides a comprehensive and detailed approach to shutting down phishing attacks.
By following these guidelines, individuals and organizations can enhance their defenses, minimize the risk of falling victim to phishing attempts, and safeguard valuable information and assets.

- Raise Awareness
- Educate individuals about the nature of phishing attacks, standard techniques employed, and potential consequences.
- Train employees to recognize phishing indicators, such as suspicious email senders, unfamiliar URLs, or unexpected requests for personal information.
- Conduct regular awareness campaigns, emphasizing the importance of vigilance and reporting any suspicious activity.
- Implement Email Security Measures
- To detect and prevent spoofed emails, utilize spam filters and email authentication protocols, such as SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
- Enable email encryption to protect sensitive information in transit.
- Deploy advanced threat protection solutions to identify and block malicious attachments or links.
- Strengthen Password Security
- Encourage the use of strong, unique passwords for all accounts.
- Implement multi-factor authentication (MFA) wherever possible to add an extra layer of security.
- Regularly update and change passwords, particularly after any suspected phishing incident.
- Verify Website Authenticity
- Train individuals to check for secure connections (HTTPS) and valid SSL certificates when visiting websites.
- Encourage using reputable browser extensions or anti-phishing tools to identify fraudulent websites.
- Caution against clicking on links from unsolicited emails or unfamiliar sources.
- Enable Security Software
- Install reputable antivirus, anti-malware, and firewall software on all devices.
- Keep security software updated to ensure protection against the latest phishing threats.
- Perform regular system scans to detect and remove any potential malware.
- Foster a Culture of Reporting
- Encourage individuals to report any suspected phishing emails or incidents promptly.
- Establish clear reporting procedures and provide accessible channels for reporting.
- Implement a swift response mechanism to investigate and mitigate reported incidents.
- Stay Informed and Updated
- Keep abreast of the latest phishing trends, techniques, and vulnerabilities.
- Regularly update software, applications, and operating systems to patch any known security vulnerabilities.
- To stay informed about emerging threats, subscribe to relevant security alerts and industry news sources.
By diligently following this detailed prevention checklist, individuals and organizations can significantly reduce the risk of falling victim to phishing attacks.
It is crucial to remain proactive, continuously evaluate and strengthen security measures, and foster a security-conscious culture to counter the ever-evolving phishing landscape.
Remember, shutting down phishing attacks requires a multi-layered approach that combines technology, education, and user awareness. By working together, you can combat this pervasive threat and safeguard your digital ecosystem.
Best Phishing Attacks Prevention Tools
- Email Security Gateways: Email security gateways scan incoming emails for suspicious content, attachments, and URLs. They use various techniques such as machine learning, heuristics, and blacklisting to identify and block phishing attempts.
- Anti-Phishing Software: Anti-phishing software helps detect and block phishing websites by analyzing URLs, website reputation, and content. These tools can be installed on web browsers, operating systems, or as browser extensions.
- Web Filtering and Content Filtering: Web filtering tools block access to known malicious websites and restrict users from visiting potentially dangerous or unauthorized websites. They can also filter out suspicious or malicious content from web pages.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple authentication factors, such as a password and a unique code sent to their mobile device, reducing the effectiveness of stolen credentials.
- Security Awareness Training: Conducting regular security awareness training for employees is crucial. Training programs educate employees about phishing techniques, red flags to watch for, and best practices for handling suspicious emails or links.
- Web Browser Security Features: Modern web browsers often come with built-in security features that can help protect against phishing attacks. These features include anti-phishing filters, warnings about potentially harmful websites, and safe browsing modes.
- DNS Filtering: DNS filtering solutions block access to known malicious domains by analyzing and filtering DNS queries. They can help prevent users from accessing phishing websites or downloading malicious content.
- Security Information and Event Management (SIEM): SIEM tools collect and analyze security event data from various sources to detect and respond to security incidents, including phishing attacks. They can provide real-time alerts and insights into suspicious activities.
- Endpoint Protection Software: Endpoint protection solutions offer antivirus, anti-malware, and anti-phishing features to detect and block malicious files, links, and attachments on endpoints such as laptops, desktops, and mobile devices.
- Incident Response and Reporting Tools: Having incident response tools in place enables organizations to respond to and mitigate phishing attacks quickly. These tools facilitate incident documentation, tracking, and reporting for post-incident analysis and improvement.
How do you Train your Employee for Phishing Attacks?
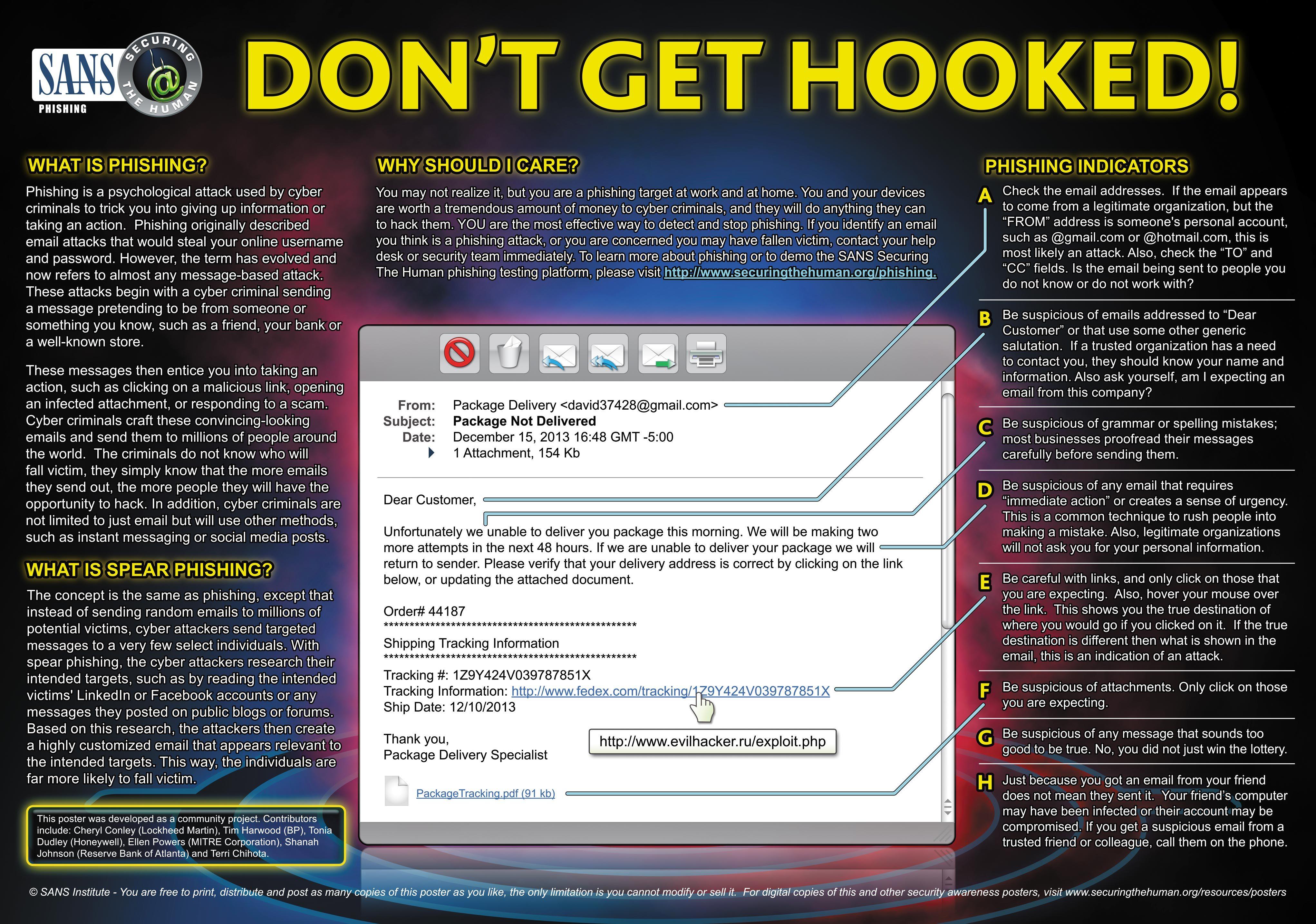
- What is Phishing: Educate employees on what phishing is and how it works. Explain that phishing involves fraudulent emails, messages, or websites that trick individuals into revealing sensitive information, such as login credentials or financial details.
- Standard Phishing Techniques: Describe common phishing techniques, such as email spoofing, deceptive URLs, and social engineering. Explain that attackers often use social engineering tactics to manipulate individuals into taking actions that compromise security.
- Identifying Phishing Emails: Provide guidelines for identifying phishing emails. Teach employees to look for signs of suspicious emails, such as generic greetings, spelling or grammatical errors, requests for personal information, urgent or threatening language, and unfamiliar senders.
- Suspicious Attachments and Links: Instruct employees to be cautious with email attachments and links. Advise against opening attachments or clicking on links in suspicious emails, especially if they are unexpected or come from unknown sources.
- Verifying Requests: Encourage employees to verify any unusual or suspicious requests they receive, especially those related to sensitive information or financial transactions. Provide clear channels for employees to confirm the legitimacy of requests, such as contacting the person directly or the relevant department.
- Secure Password Practices: Emphasize the importance of strong passwords and password hygiene. Instruct employees to create unique and complex passwords, avoid reusing passwords across different accounts, and enable two-factor authentication where available.
- Reporting Phishing Attempts: Establish a straightforward process for reporting phishing attempts. Encourage employees to promptly report suspicious emails or incidents to the designated IT or security team. Please provide them with the necessary contact information or reporting tools.
- Security Updates and Patching: Stress the importance of keeping software, operating systems, and applications updated with the latest security patches. Explain that attackers often target vulnerabilities in outdated software.
- Regular Training and Refreshers: Conduct regular training sessions and refreshers to reinforce security awareness. Provide real-life examples of phishing emails and encourage employees to actively participate in simulated phishing exercises to test their ability to identify and respond to phishing attempts.
- Ongoing Communication: Maintain ongoing communication about phishing threats and best practices through various channels, such as email newsletters, internal messaging platforms, and bulletin boards. Share real-world examples of phishing attacks to keep employees informed and vigilant.
Conclusion
The prevention checklist provides a comprehensive and detailed approach to shutting down phishing attacks.
By implementing these preventive measures, individuals and organizations can significantly reduce their susceptibility to phishing attempts and protect valuable information and assets.
By raising awareness, implementing email security measures, strengthening password security, verifying website authenticity, enabling security software, fostering a culture of reporting, and staying informed and updated, we can establish a robust defense against phishing attacks.
Remember, combating phishing attacks requires a collective effort that involves continuous education, proactive security measures, and vigilant user awareness.
By following this prevention checklist and staying proactive in the face of evolving threats, we can create a safer digital environment and protect ourselves from the harmful consequences of phishing attacks.
Together, let’s shut down phishing attacks and ensure the security and integrity of our digital interactions.



.png
)
