Microsoft has taken a significant step toward enhancing cybersecurity by introducing a new phishing attack protection feature for Microsoft Teams.
The feature aims to safeguard users from brand impersonation in chats initiated by external domains, a common tactic used by cybercriminals to launch phishing attacks.
The new feature, which proactively alerts users to potential impersonation risks during first contact with external domains, will be rolled out in phases.
It is scheduled to begin its targeted release in late October 2024, with global availability expected by mid-February 2025.
Targeting External Chat Risks
The growing popularity of Microsoft Teams as a business collaboration tool has also made it a target for cyber threat actors. Organizations that allow communication with external domains through Teams are particularly vulnerable to phishing attacks.
Cybercriminals often impersonate trusted brands to deceive employees, aiming to steal credentials, deploy malware, or carry out ransomware attacks.
Are you from SOC/DFIR Teams? - Analyse Malware Files & Links with ANY.RUN Sandox -> Try for Free
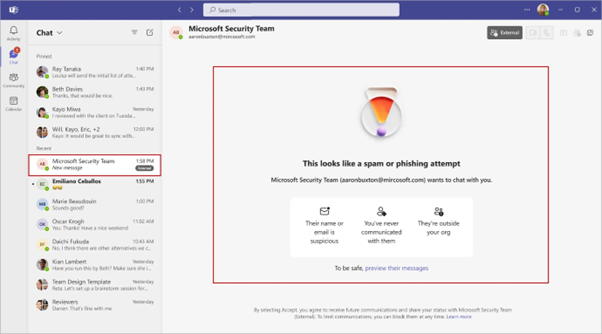
To counter these threats, Microsoft’s new security feature will scan incoming messages from external senders during their initial contact. If an attempt to impersonate a trusted brand or domain is detected, the system will flag it with a high-risk alert.
The warning will prompt users to closely inspect the sender’s name and email address before engaging further.
Microsoft plans to roll out the new feature in two phases:
- Targeted Release (Preview): Starting in late October 2024, the feature will be available for select users in the Targeted Release program, allowing organizations to test and provide feedback before the global launch.
- General Availability (Worldwide): The broader rollout will begin in mid-November 2024 and is expected to complete by mid-February 2025.
Although the initial completion date was set for mid-January 2025, Microsoft has slightly adjusted the timeline to ensure a smooth deployment of this important security enhancement.
How It Works
Currently, Teams users can receive messages from external domains if allowed by their organization. These messages, while subject to user acceptance, lack impersonation risk detection capabilities. The new feature introduces several safeguards:
- Messages from external senders will automatically be checked for impersonation risks during the first interaction.
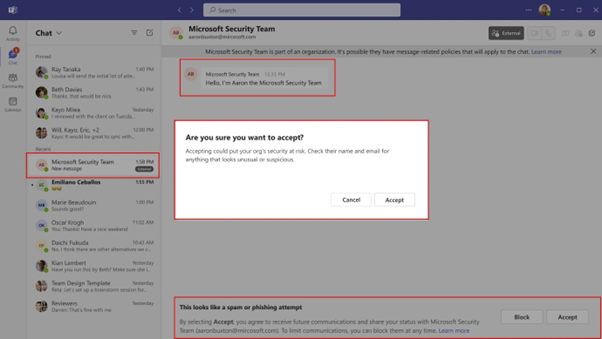
- If a risk is detected, users will see a high-risk warning in the Accept/Block prompt.
- Users must preview external messages before making a decision, ensuring they stay cautious.
- Even after accepting a message, an additional warning will remind users to verify the sender’s authenticity.
The feature will be enabled by default and requires no action from IT administrators. However, organizations can monitor impersonation attempts via audit logs and are advised to educate employees on recognizing these alerts.
Microsoft’s new feature comes at a critical time, as phishing campaigns targeting Teams users have surged. Notably, threat groups like FIN7 and Storm-1811 have impersonated IT support personnel to deceive employees.
These actors exploit Teams’ default settings to initiate contact, often after overwhelming victims with “email bombing” tactics.
Once trust is established, attackers manipulate victims into granting remote access through tools like Microsoft Quick Assist or Teams’ screen-sharing feature.
This access is then exploited to install malware, harvest credentials, and move laterally within networks. Recent incidents also revealed ransomware operations, such as the deployment of Black Basta ransomware through these methods.
Between November 2024 and January 2025, researchers observed over 15 incidents of such attacks, with activity peaking in early 2025.
Microsoft’s integration of advanced phishing protection into Teams signals a proactive approach to combating modern cybersecurity threats.
By prioritizing user safety without disrupting workflows, the tech giant reaffirms its commitment to creating a secure collaboration environment.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
