Security researchers have uncovered a sophisticated method of exploiting the Dynamic Host Configuration Protocol (DHCP) administrators group to escalate privileges within Windows domains.
This technique, dubbed “DHCP Coerce,” leverages legitimate privileges to compromise entire networks potentially.
The vulnerability centers around the DHCP (Dynamic Host Configuration Protocol) service, which is essential for network administration. It automates the assignment of IP addresses, simplifying the management of network connections.
However, this convenience comes with a downside. Attackers can exploit the DHCP Administrators group by leveraging specific configurations and permissions, enabling them to escalate their privileges within a Windows domain.
The exploitation process involves several technical steps, including manipulating DHCP settings and using malicious scripts.
By gaining elevated privileges, attackers can potentially take over the entire domain, accessing and manipulating data at will.
This vulnerability is particularly concerning because it can be exploited remotely without physical access to the network.
However, this research demonstrates that even well-intentioned access controls can be manipulated maliciously.
The exploitation process involves several technical steps, including manipulating DHCP settings and using malicious scripts.
By gaining elevated privileges, attackers can potentially take over the entire domain, accessing and manipulating data at will.
This vulnerability is particularly concerning because it can be exploited remotely without physical access to the network.
The DHCP Administrators Group
The DHCP administrators group is an Active Directory (AD) group that manages DHCP servers.
Members are supposed to have limited permissions and be restricted to querying and modifying DHCP service configurations.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
This leads to a domain takeover when the DHCP server is installed on a Domain Controller (DC).
Akamai researchers have identified a novel privilege escalation method that explicitly targets Active Directory (AD) environments.
This technique exploits the DHCP administrators group to elevate privileges and gain unauthorized access to valuable resources.
Abusing DHCP Options
DHCP options are configurations advertised to network clients, such as IP addresses, subnet masks, and DNS server information.
The researchers demonstrated that attackers can manipulate these options to inject malicious configurations.
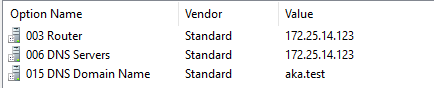
One such option is “Proxy autodiscovery,” which can be used to configure a web proxy and compromise client credentials.
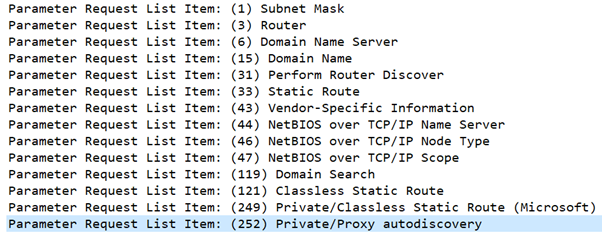
The DHCP Coerce Technique
The DHCP Coerce technique manipulates the DNS Server option to redirect DHCP DNS Dynamic Updates to an attacker-controlled address.
This coerces the DHCP server to authenticate using Kerberos, which can then be relayed to compromise the server.
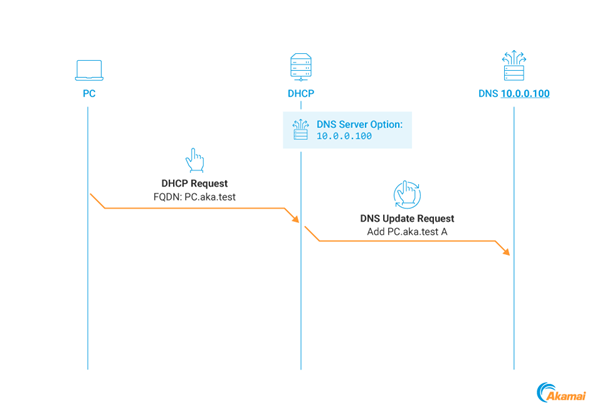
Kerberos Relay Attack
By coercing a Kerberos authentication and relaying it, attackers can impersonate the DHCP server machine account and gain full control over the server.
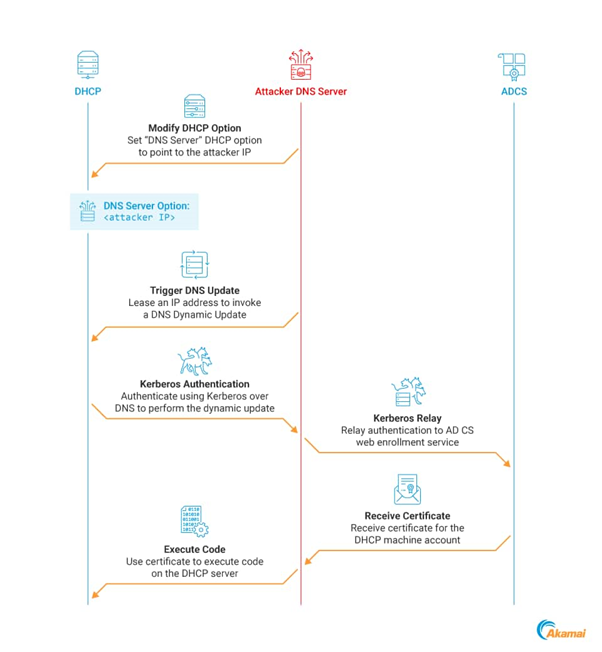
This is particularly concerning when DHCP servers are installed on DCs, which is the case in 57% of the networks the researchers observe.
Mitigating the Threat
The researchers have provided detailed mitigation and detection steps to counter this technique.
These include identifying risky DHCP configurations, mitigating relay attacks against AD Certificate Services (AD CS), practicing DHCP administrator’s group hygiene, using network segmentation, and identifying DNS anomalies.
The discovery of the DHCP Coerce technique highlights the importance of vigilance in network security.
DHCP Configuration Security
- Audit Logs: Check for unusual DHCP server log activities.
- Scope Limitation: Carefully configure DHCP scopes to prevent unauthorized access.
- Snooping: Use DHCP snooping on switches to block fake DHCP messages.
AD CS Relay Attack Mitigation
- LDAP Security: Enable LDAP signing and switch to LDAPS for secure communication.
- Authentication Protection: Use Extended Protection for Authentication to guard against MitM attacks.
- Kerberos Armoring: Implement FAST for added Kerberos protocol security.
DHCP Administrators Group Management
- Membership Audits: Regularly review group membership for unauthorized access.
- Least Privilege: Restrict group membership to essential personnel only.
- RBAC: Apply Role-based Access Control for precise access management.
Network Segmentation
- VLANs: Implement VLANs for logical network segmentation.
- Firewall Rules: Enforce strict rules between segments to control traffic and prevent attacks.
- Data Separation: Store sensitive data in secure, segmented network zones.
DNS Anomaly Detection
- Logging: Enable DNS query logging to spot unusual patterns.
- DNSSEC: Implement DNS Security Extensions to validate DNS response authenticity.
- Threat Intelligence: Use feeds to block known malicious domains and IPs.
Implementing these strategies can significantly bolster your network’s defense against DHCP abuse, AD CS relay attacks, and DNS anomalies. Regular updates and reviews of security protocols are essential for maintaining effective protection.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.



