In a groundbreaking development, researchers have uncovered how attackers are exploiting Windows Virtualization-Based Security (VBS) enclaves to create malware that is highly evasive and difficult to detect.
VBS enclaves, designed as isolated and secure regions of memory within a process, are being weaponized to bypass traditional security mechanisms, posing a significant threat to enterprise systems.
VBS Enclaves: A Double-Edged Sword
VBS enclaves were introduced by Microsoft as part of its Virtual Trust Levels (VTL) architecture, aimed at improving system security by isolating sensitive operations from the rest of the operating system.
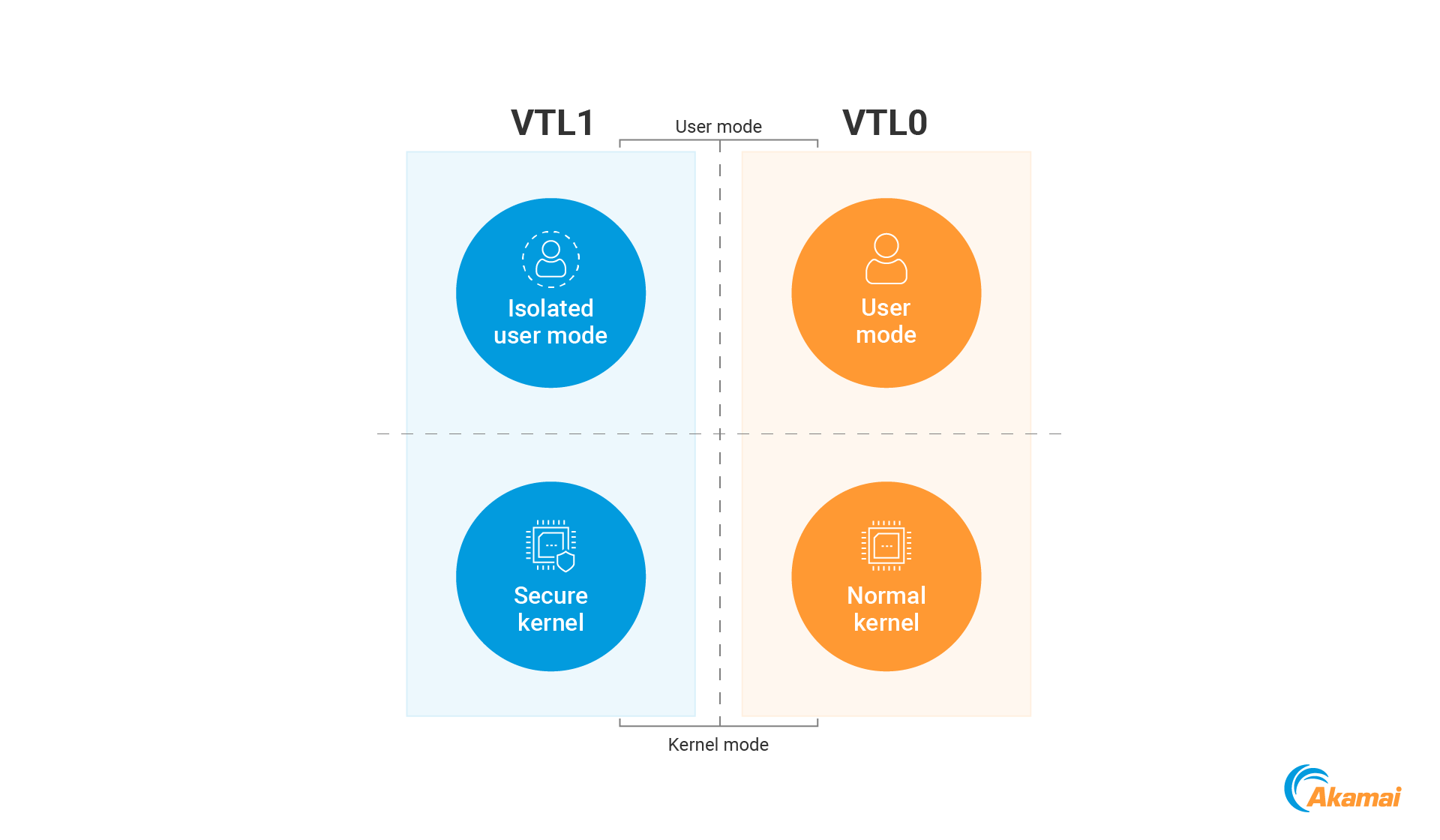
These enclaves operate in an isolated memory region inaccessible to the kernel and other processes, making them invaluable for protecting sensitive data.
However, this same isolation is now being exploited by attackers to hide malicious code from endpoint detection and response (EDR) tools and memory-based forensic analysis.
The key advantage for attackers lies in the enclave’s ability to execute code that is invisible to traditional monitoring methods.
For example, API calls made from within an enclave bypass user-mode hooks and kernel-level monitoring, rendering them undetectable by conventional security tools.
According to Akamai, this capability has led researchers to dub such malware “enclave malware.”
Exploitation Techniques
Attackers have identified multiple pathways to execute malicious code within VBS enclaves.
One approach involves exploiting vulnerabilities in the operating system or third-party enclave modules, such as CVE-2024-49706, which allowed unsigned modules to be loaded into enclaves before being patched.
Another method is the “Bring Your Own Vulnerable Enclave” (BYOVE) technique, where attackers exploit known vulnerabilities in legitimate signed enclave modules to execute malicious payloads.
For instance, CVE-2023-36880, a vulnerability in a Microsoft Edge enclave module, was leveraged to achieve arbitrary read/write access within the enclave memory.
Additionally, attackers can abuse “debuggable” enclave modules intended for development purposes to inject unsigned shellcode into VTL1 (Virtual Trust Level 1), achieving partial execution within the secure environment.
While this method sacrifices some stealth due to its debuggable nature, it still evades API monitoring effectively.
Researchers have also demonstrated a novel evasion technique called “Mirage,” which uses VBS enclaves to store malicious payloads in VTL1 memory.

The payload periodically transfers back to VTL0 (normal memory) for execution before erasing itself, making detection through memory scans nearly impossible.
Unlike traditional techniques that toggle executable states of memory pages, Mirage leverages the isolation of VTL1 to keep payloads completely hidden from forensic tools during dormant stages.
The misuse of VBS enclaves underscores a critical challenge in cybersecurity: technologies designed for protection can also be weaponized by adversaries.
While enclave malware remains largely theoretical at this stage, its potential adoption by advanced threat actors could significantly complicate detection and response efforts.
To mitigate these risks, security teams are advised to establish baselines for legitimate use of VBS enclaves and monitor for anomalies such as unexpected enclave activity in non-standard processes.
Additionally, identifying loaded enclave-related DLLs like vertdll.dll can serve as an early warning mechanism for potential abuse.
As attackers continue to innovate with techniques like BYOVE and Mirage, defenders must remain vigilant and adapt their strategies to counteract emerging threats leveraging trusted execution environments.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
