Researchers discovered a new malware campaign from the Winnti threat group that utilizes the supply-chain attacks with a new set of artifacts to inject a sophisticated backdoor in windows computers.
Winnti group activities are being monitored since 2013, since then it continuously targeting various private sectors including Aviation, Gaming, Pharmaceuticals, Software development, Telecommunication and Technology that resides in Asia.
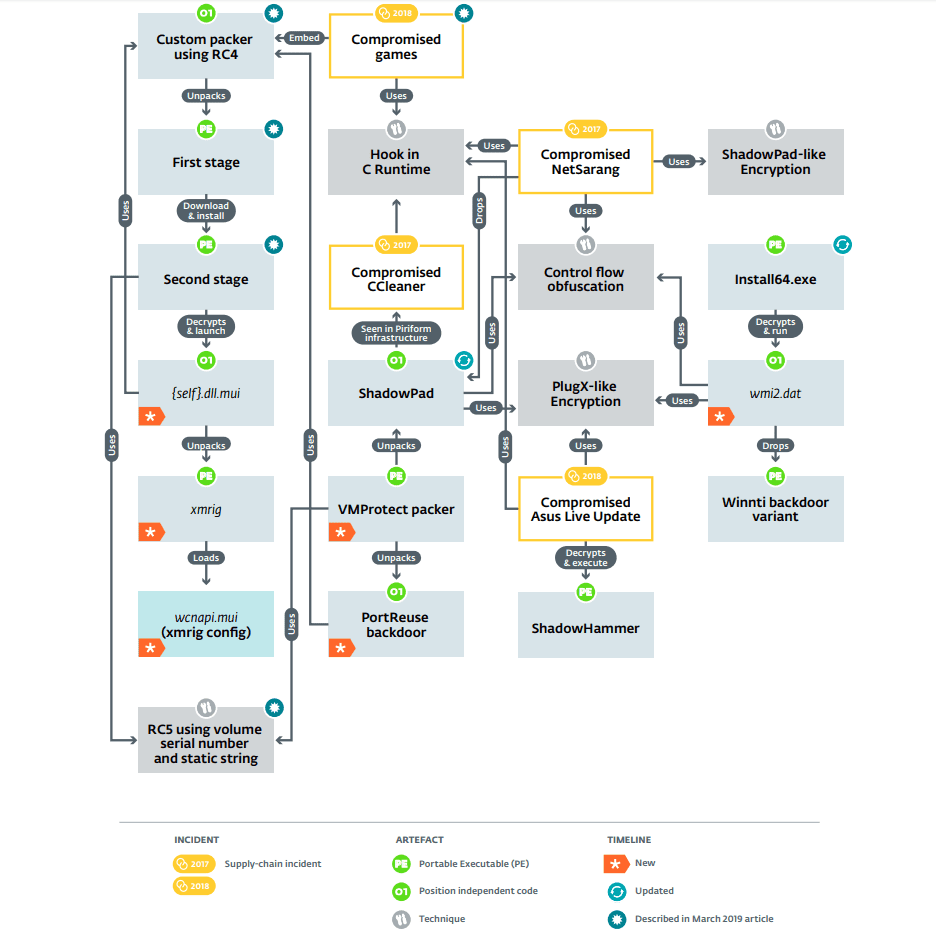
Researchers from ESET uncovered a VMProtected packer that was used to deliver the backdoor called PortReuse using cipher and key generation technique and also it delivered another malware called shadowpad.
There are various artifacts are learned in this research and found that it using the same technique, events relationships, and code for the various targeted attacks.
Winnti group believed to be Aliases with different threat actors in the recent past including Winnti Umbrella, Axiom, Group 72, APT41, Blackfly, and Suckfly.
Also, it responsible for recently uncovered an operation called ShadowHammer that targeted the ASUS computer software update tool to inject a backdoor.
This new research exposing the arsenal and methods of the Winnti Group that deliver the PortReuse backdoor on windows computers that deployed in a targeted organization network.
PortReuse Backdoor Activities
Researchers digging deeper into a custom packer that was uncovered in the previous report found the more executable files and believed to be used in supply-chain attacks using compromised software.
But actually they discovered a new listening-mode modular PortReuse backdoor that injects into a running process already listening on a TCP port.
Attackers used the following formats during the initial launch and only a single file is written to disk to start PortReuse:
- Embedded in a .NET application launching the initial Winnti packer shellcode
- In a VB script that deserializes and invokes a .NET object that launches the shellcode
- In an executable that has the shellcode directly at the entry point

Later the custom packer decrypt and launch a first component InnerLoader ( InnerLoader.dll ), also researchers able to extract the packer metadata. “The metadata from the packer, including absolute file path when it was packed”.
According to the ESET report, “ In the case of the .NET injector, InnerLoader targets a process called GameServer_NewPoker.exe and in the case of the VBS injector, it will look for a process listening on port 53 (DNS). These payloads are, again, packed using the same packer and are called NetAgent and SK3 according to the packer configuration. ”
PortReuse backdoor is targeting different commonly used ports including 53 (DNS over TCP), 80, 443, 3389 (RDP), and 5985 (Windows Remote Management).
In order to perform the network hook in targeted victims, the backdoor initially needs to inject into the running process.
ESET researchers were able to decrypt several payloads packed using this custom VMProtected packer and them that the payload was either the PortReuse backdoor or the ShadowPad malware.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates


