A new wave of cyber espionage attacks has brought BPFDoor malware into the spotlight as a stealthy and dangerous tool for compromising networks.
According to security experts at Trend Micro, BPFDoor is a state-sponsored backdoor attributed to the advanced persistent threat (APT) group known as Earth Bluecrow (also referred to as Red Menshen).
This malware exploits reverse shells and sophisticated Berkeley Packet Filtering (BPF) techniques to infiltrate and control systems across telecommunications, finance, and retail sectors in regions such as South Korea, Hong Kong, Myanmar, Malaysia, and Egypt.
Understanding BPFDoor Malware
BPFDoor, a backdoor detected as Backdoor.Linux.BPFDOOR, is uniquely powerful due to its reliance on BPF, a kernel-level packet filtering technology.
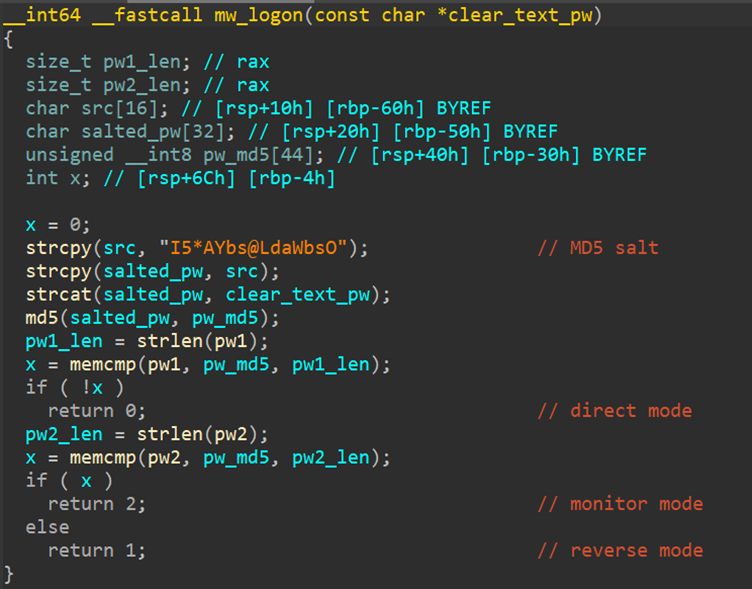
While its core functionalities resemble rootkits, BPFDoor distinguishes itself through its ability to remain undetected by firewalls and evade conventional network scans.
The malware activates upon receipt of “magic sequences” — specific byte strings embedded in network packets — that trigger predefined actions on the target machine.
The primary stealth capabilities of BPFDoor include changing process names, avoiding port listening, and bypassing security logs.
This makes it highly suitable for long-term espionage, allowing attackers to embed themselves deeply within a network without raising suspicion.
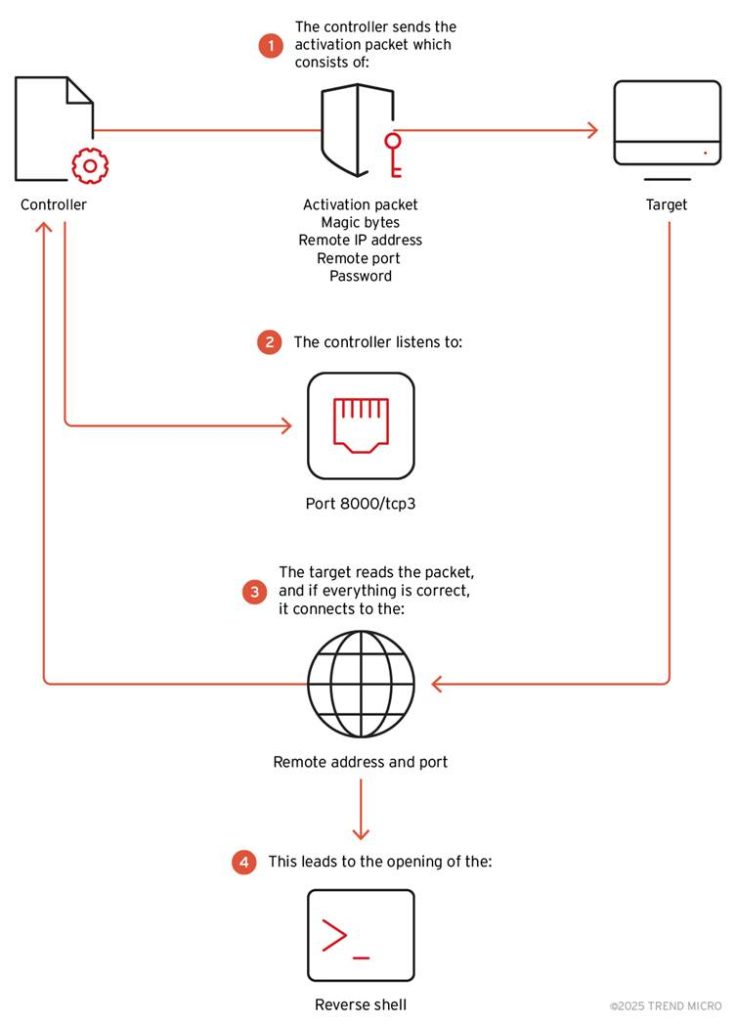
Reverse Shell Technique and Lateral Movement
One of BPFDoor’s alarming capabilities is its use of reverse shells to expand control over infected systems.
A reverse shell allows attackers to run commands remotely on compromised servers by reversing the typical client-server communication model. Through this mode, attackers can move laterally across networks to access sensitive data or control additional systems.
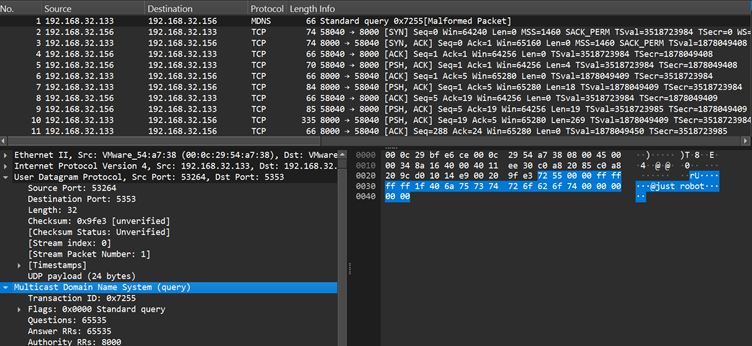
Using a custom controller, threat actors deploy reverse shells via three protocols: TCP, UDP, and ICMP. Once activated, the malware communicates with the attacker’s system by bypassing standard security defenses.
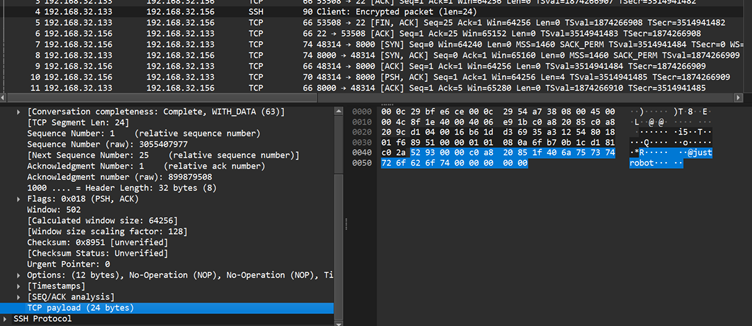
For example, a controller command can ask BPFDoor to open an encrypted reverse shell session between an infected host and an attacker’s machine, enabling seamless remote access.
The controller also allows attackers to modify parameters like passwords, magic sequences, and destination ports, enhancing customization for varying targets.
Such versatility enables Earth Bluecrow to adapt its attacks for different industries and geographies.
Targets and Defense Mechanisms
Trend Micro’s investigation revealed BPFDoor primarily targets Linux-based servers in sectors critical to national and corporate security.
Recent attacks have been observed on telecommunications providers in South Korea and Myanmar, financial institutions in Egypt, and retail businesses in Malaysia.
Defenders are urged to monitor network activity for unusual TCP, UDP, or ICMP packets containing suspicious magic sequences or patterns indicative of BPFDoor activity.
BPFDoor’s ability to use reverse shells, combined with its stealthy nature, poses significant risks to organizations worldwide.
As Earth Bluecrow continues to refine its techniques, companies must bolster their defenses to protect against this advanced cyber espionage tool.
Detection, response, and proactive security measures are critical to countering BPFDoor and safeguarding sensitive networks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
