Offensive security released Kali Linux 2023.1 with new tools for purple and blue teamers for defensive security.
On March 13th Kali Linux penetration distro completed 10 years of providing amazing services to the cyber security community.
On celebrating its 10th anniversary the Offensive security team released Kali Linux 2023.1 with Kali purple designed for defensive security.
What’s New With Kali Linux 2023.1
- Kali Purple – Defensive security
- Python Changes – Python 3.11 & PIP
- 2023 Theme – New Theme for 2023
- Desktop Updates – Xfce 4.18 & KDE Plasma 5.27
- Default Kernel Settings – What makes the Kali kernel different
- New Tool – 7 New Tools added
The Kali purple consists of SOC In-A-Box architecture which includes SOC analysis, Blue / Red / Purple team exercises, and design security controls.
It includes over 100 defensive tools such as Arkime, CyberChef, Elastic Security, GVM, TheHive, Malcolm, Suricata, and Zeek.
“We made offensive security accessible to everyone. No expensive licenses required, no need for commercial grade infrastructure, no writing code or compiling tools to make it all work… Just download Kali Linux and do your thing,” reads the announcement.
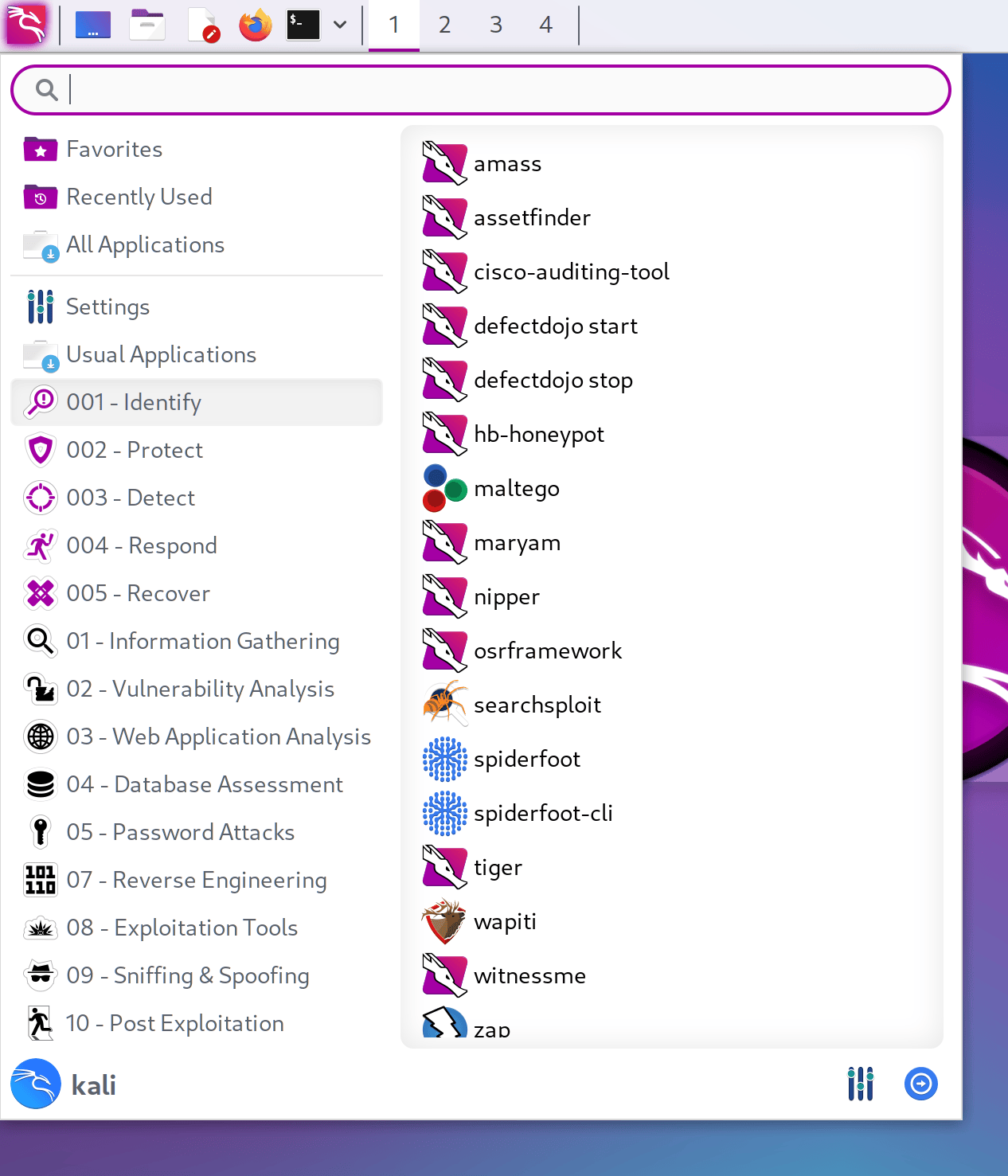
Following is the Kali Linux 2023.1 defensive menu structure.
- Identify
- Protect
- Detect
- Respond
- Recover
Python Updates and Errors
Debian is moving to the next stable update, so there could be package updates everywhere. These updates may affect Python’s PIP behavior.
To avoid this warning Kali Team has provided a “temporary patch which prevents breaking of old packages.”
“Active package maintainers are upgrading their work to be the latest version, otherwise, it’s a long wait for the next release! Python is no exception, and Python 3.11 is now in Debian, which comes with more informative error tracebacks and huge speed increase (between 10-60%).”
Fresh 2023 Theme in Kali Linux 2023.1
Every year’s first release of Kali includes a theme refresh, following the 2023 update, and also includes wallpapers for desktop, login, and boot displays.

The desktop environments Xfce, KDE, and GNOME also updated to the latest versions to make feeling good.
Issues Fixed
Nvidia users had a nightmare with Kali Linux as their 525 series broke with some of the GPU models.
Kali Team states that the bug affects all the Linux distributions including Debian, Ubuntu, and Arch Linux.
The only possible solution is to uninstall the Nvidia drivers, then reboot:
┌──(kali㉿kali)-[~]
└─$ sudo apt purge “nvidia“
[…]
┌──(kali㉿kali)-[~]
└─$ sudo reboot -f
New Tools Added
Following are the new tools added with the Kali Linux
Arkime – Packet Capture
CyberChef – Tool for Encryption
DefectDojo – Vulnerability Data Report
Dscan – Scanner
Kubernetes-Helm – Kubernetes Package Manager
PACK2 – Attack Tool
Redeye – Analytic tool
Unicrypto – Cryptographic Libraries
How to Get Kali Linux 2023.1
If you are a new user you can download it from here. If you already have an existing Kali Linux installation, you can do a quick update using the commands.
┌──(kali㉿kali)-[~]
└─$ echo “deb http://http.kali.org/kali kali-rolling main contrib non-free non-free-firmware” | sudo tee /etc/apt/sources.list
[…]
┌──(kali㉿kali)-[~]
└─$ sudo apt update && sudo apt -y full-upgrade
[…]
┌──(kali㉿kali)-[~]
└─$ cp -vrbi /etc/skel/. ~/
[…]
┌──(kali㉿kali)-[~]
└─$ [ -f /var/run/reboot-required ] && sudo reboot -f
You should now be on Kali Linux 2023.1 We can do a quick check by doing:
┌──(kali㉿kali)-[~]
└─$ grep VERSION /etc/os-release
VERSION=”2023.1″
VERSION_ID=”2023.1″
VERSION_CODENAME=”kali-rolling”
You are also recommended to review our Kali Linux Tutorials which cover dozens of Kali Linux Tools. Also, Learn the Kali Linux course and complete Kali Linux Commands List.
Other Version Coverages:




 years old on Monday, March 13th! Join the celebration with office hours, an AMA, and a Puzzle Challenge.
years old on Monday, March 13th! Join the celebration with office hours, an AMA, and a Puzzle Challenge.  Challenge: coming
Challenge: coming 
.png
)
